How would you like to earn money just by sitting at home in front of a computer and viewing ads?
Us neither.
What if you could earn $1.20 an hour?
We’re not sure how you’d manage to cover the costs of your internet connection at that rate, but if you could somehow get online for free, and you were ready to work a solid 12 hours a day, 7 days a week, you could get out with close to $6000 a year.
In many parts of the world, that’s serious money, so we’re not surprised that people are willing to do it.
One online service that will pay you at that sort of rate is a company called ClixSense, which basically pays you for viewing ads, completing online surveys, categorising images or videos, making Google searches, and so on.
ClixSense also runs an affiliate network, so you can earn commission on the earnings of new members whom you bring to the party, as a way of keeping the ClixSense click-machine fuelled with clickers.
As far as we can see, ClixSense is itself is affiliated with pay-per-click networks, so that every time you click an ad via the ClixSense system, the company racks up its per-click fee, some of which is paid out to you.
According to ClixSense’s website, 6,626,048 members have earned more than $20 million by delivering more than 3.5 billion page views over the past nine years.
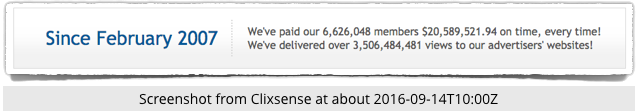
That averages out at about $3 and 500 views per user, for a pay rate of well under one cent per view.
What ClixSense didn’t tell its 6.6 million members when they signed up and chose a password was that it simply stored those passwords in plaintext in a database, along with other personal information.
Passwords were unsalted, unhashed and unstretched, so that when the service was hacked recently, the crooks didn’t need to spend any time cracking the stolen passwords because they were essentially pre-cracked and ready to dump.
And dumping the passwords is exactly what the attackers did.
According to Ars Technica, the passwords were allegedly published to take some sort of revenge on ClixSense for failing to admit that the breach had happened:
!!!We are releasing ~2.2 million users sample today. […] Site owner tell users no leak happened but reset user pass. This is proof leak happened and only publicaly release sample because owner lied to people. […] To purchase all dbs+emails+source contact any of us in usual way.
So, not only another breach, but also an authentication database of plaintext passwords, even though we’ve known for close to 40 years that it’s neither desirable nor necessary (and certainly no longer acceptable) to store passwords directly.
ClixSense has, in fact, published an update about the hack, saying:
Members we want to keep you informed on what is happening with our recent hack. It has come to our attention that this hacker did get access to our database server for a short period of time. He was able to gain access to this not directly but instead through an old server we were no longer using that had a connection to our database server. (This server has since been terminated).
He was able to copy most if not all of our users table, he ran some SQL code that changed the names on accounts to “hacked account” and deleted many forum posts. He also set user balances to $0.00.
We were able to restore the user balances, forum and many account names. Some of you were asked to fill out your name again as we did not want to restore this from our backup due to the amount of time it would have taken to get back online.
What does this all mean? Simply put, your ClixSense account information is now much more secure.
ClixSense isn’t actually saying why you should feel confident that your already-breached personal data is now being stored securely.
The only security improvement mentioned in the breach notification is that the insecure server that led to the attack – a server that ClixSense rather paradoxically claims “we were no longer using” – has been turned off.
What to do?
- Don’t use the same passwords on two different sites. Even if you choose a super-strong password, it only takes one careless site to leak that password in directly usable form.
- Don’t store passwords in plaintext. As we said above, that has been neither desirable, nor necessary, nor acceptable, for many years.
- Don’t retire a server but leave it active on your production network. That’s like replacing all the locks on your house, except for the lock on your back door that you already know is broken.
- Don’t make unsupported claims in a breach notification. If you want to convince your users that you are now taking security seriously, you need to provide some evidence so that they have a reason to believe you.
LEARN MORE: What (not!) to say after a data breach ►

Anonymous
For some bored 10-16 year old kid on summer break, it’s possible to make serious Steam money to buy Hats or Keys. I would hate to think of how many kids grew up, forgot they even signed up for this, and lost their hopelessly repeated password.