Thanks to
Graham Chantry, Fraser Howard and Benjamin Humphrey
of SophosLabs for their work on this article.
Beware the latest arrival on the ransomware scene: Zepto.
It’s very similar to the well-known Locky malware, and the consequences of an attack are the same: your files end up scrambled, at which point the crooks offer to sell you the decryption key.
In fact, the Zepto and Locky malware families are similar enough that when you get to Zepto’s “pay page,” where the crooks tell you how much you need to pay to unscramble your data, you see this:
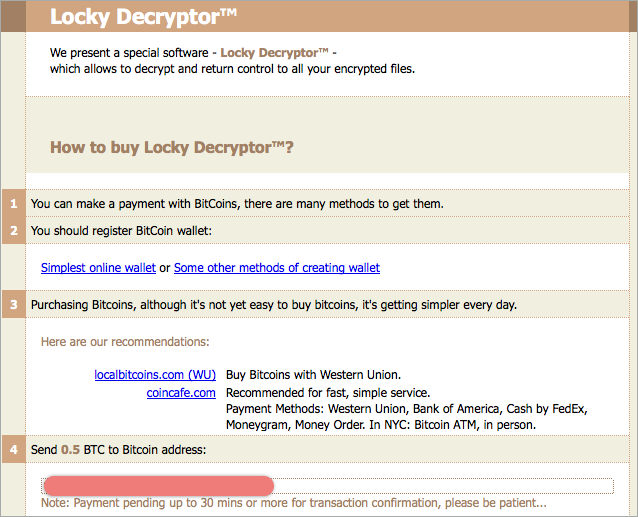
There is one obvious difference from a Locky infection, however: after a Zepto attack, your files will have been renamed so that they end .zepto. (Locky got its name because it uses the extension .locky instead.)
The idea behind renaming all your files is so that you can see just how much is at stake if you don’t pay up.
You can see not only how near you are to recovering your precious data, but also just how far.
How Zepto arrives
In the past week, we’ve seen variants of Zepto distributed in two main ways, both of which are commonly used by ransomware criminals:
- In emails with an attached
ZIParchive. - In emails with an attached
DOCMfile.
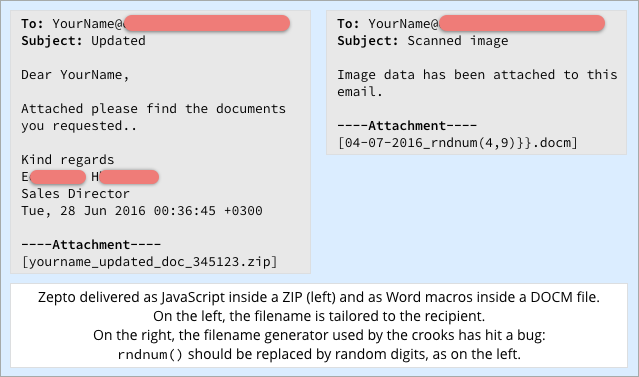
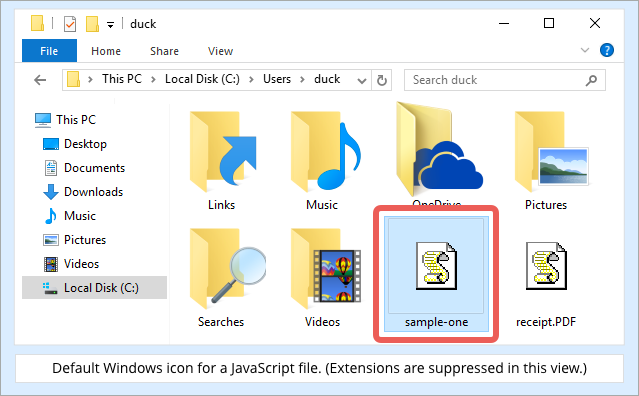
In the first case, opening up the ZIP archive will unpack a file with a .JS (JavaScript) extension.
If JavaScript seems like a strange format for an attachment that claims to be a document, remember that Windows suppresses the .JS part of the name by default, and shows the file with an icon that gives the impression of a text file:
Opening the JavaScript file, however, runs the script program inside, which in turn downloads the ransomware as an EXE (Windows program) file, and runs it.
In the second case, the attachment is DOCM, so that double-clicking on the file opens it by default in Microsoft Word.
But DOCM is short for “document with macros,” a special type of document that contains embedded scripts written in VBA (Visual Basic for Applications).
VBA is a programming language that has many similarities with JavaScript, and that can be used for much the same purposes, including spreading malware.
Macros inside a Word file don’t run by default (a security precaution introduced many years ago by Microsoft), but they do produce a prompt like the one here, as good as inviting you to use the [Options] button to adjust your security settings.
In the recent Zepto attacks we’ve seen, the booby-trapped documents were blank, opening rather unusually to an empty page:
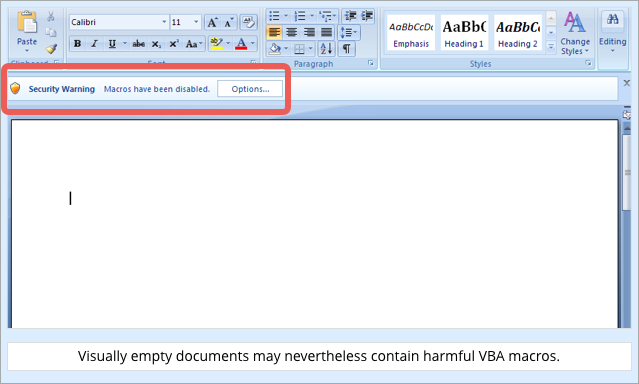
Most documents that carry macro-based ransomware include some sort of explanation or excuse to encourage you to click [Options] and change your security settings – often, ironically, under the guise of improving security somehow.
Here, the crooks have kept quiet, hoping you’ll click on [Options] of your own accord.
We’re not sure whether this was by accident (because they forgot to include explanatory instructions), or by design (to avoid the sort of message that has become widely associated with ransomware).
Enabling macros has the same side-effect as opening the JavaScript file above: the VBA script downloads the ransomware as an EXE (Windows program) file, and runs it.
Sophos products detect and block these attack vectors under a variety of names, including: Mal/DrodZp-A (attached ZIP files), Troj/JSDldr-LU (JavaScript downloaders inside the ZIPs), Troj/DocDl-DUN (attached Word macro files), Mal/Ransom-EM and Troj/Ransom-DJF (the ransomware EXE files).
Time to pay
Much like Locky, Zepto starts off by “calling home” to a web server run by the crooks, from which it downloads an encryption key to scramble your data.
The crooks keep the corresponding decryption key to themselves, which is what they later offer to sell back to you. (See above, where the asking price is half a bitcoin – BTC 0.5, currently about $300.)
Your data files are both scrambled and renamed, so that encrypted files end up with names that look like this:
FA3D5195-3FE9-1DBC-E35E-89380D21F515.zepto FA3D5195-3FE9-1DBC-7E8D-D6F39B86044A.zepto FA3D5195-3FE9-1DBC-1683-7BF4FD77911D.zepto FA3D5195-3FE9-1DBC-30B9-E2FF891CDB11.zepto
The first half of each name is the same for every file, and is a unique identifier that tells the crooks who you are if you decide to pay up to get your data back.
After your files are scrambled, Zepto presents a “how to pay” message, to make very sure you know that you can recover your data for a fee.
The message appears in three different ways: as your desktop wallpaper; in an image that’s opened up in the Windows Photo Viewer; and as an HTML page that’s saved into every directory where files have been scrambled.
The personal identification ID in the “how to pay” message is the same as the first half of each scrambled filename.
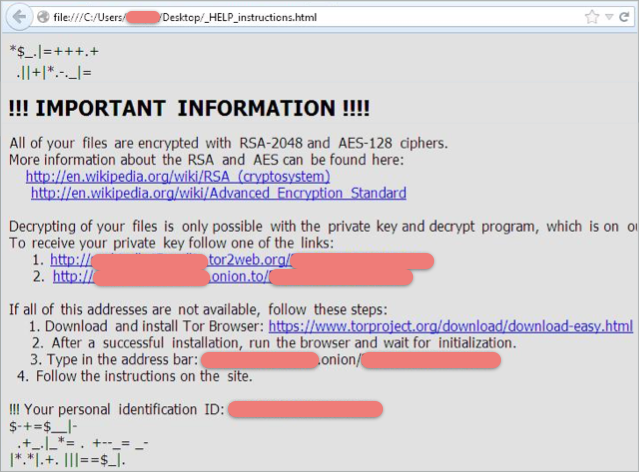
Following the instructions in _HELP_instructions.html takes you to the “pay page” shown at the start of the article.
What to do?
We regularly offer advice on preventing (and recovering from) attacks by ransomware and other nasties.
Here are some links we think you’ll find useful:
- To defend against ransomware in general, see our article How to stay protected against ransomware.
- To protect against JavaScript attachments, tell Explorer to open .JS files with Notepad.
- To protect against misleading filenames, tell Explorer to show file extensions.
- To protect against VBA malware, tell Office not to allow macros in documents from the internet.
- To learn more about ransomware, listen to our Techknow podcast.
LISTEN NOW
(Audio player above not working? Listen on Soundcloud or access via iTunes.)


Wilbur
Thanks for those screen shots – I have received a lot of spam with attached zipfiles that match the naming convention shown in your example. They come in with a variety of subjects – “Documents copies”, “Financial report”, “new invoice”, “report”, “Updated” etc. They usually arrive in groups of threes – three messages, all identical except for file name random number, sender details and time sent. I have wondered what nastiness was hidden in the zipfiles but never enough to actually open one.
I’m running a Mac (and I don’t have Microsoft Word installed) so it looks like these would have no effect on my system. But – and this is a serious question, not an attempt to start a religious war – are there currently any ransomware threats directed against Mac’s OS X circulating? I know there are some generic viruses out there but ransomware makes me extra nervous.
Paul Ducklin
Ransomware has been tried on the Mac. Nothig like the wave of attacks on Windows yet…let’s hope it stays that way, although once the crooks figure out how to make money off Macs I imagine they will put in more effort. In cybercrime, sadly, nothing seems to breed success quite like success.
https://nakedsecurity.sophos.com/2016/03/08/ransomware-arrives-on-the-mac-osxkeranger-a-what-you-need-to-know/
If you are worried about blocking malware on your Mac, Sophos Home is free (covers Windows, too):
https://home.sophos.com/
HtH.
Larry M
Duck wrote: “If JavaScript seems like a strange format for an attachment that claims to be a document, remember that Windows suppresses the .JS part of the name by default, and shows the file with an icon that gives the impression of a text file:”
Why anyone (even a novice) would leave this default for more than the first 10 minutes is completely beyond my comprehension.
Larry M
Duck wrote “Macros inside a Word file don’t run by default (a security precaution introduced many years ago by Microsoft), but they do produce a prompt like the one here, as good as inviting you to use the [Options] button to adjust your security settings.”
Jerks using macros for malware distribution have made it necessary for me to share macros with colleagues by pasting them into email and then walking them through installation over the phone.
Chuck
Do you know, or can you tell me if ransomware also encrypts files on external hard drives that are attached? Or just the files on the computer?
Paul Ducklin
Most ransomware (including Zepto, as far as I know) overwrites any writable directories it can find, whether they’re mapped via drive letters or are accessible via network shares.
Removable drives are generally assigned a drive letter or a mount point (a sub directory where their contents are visible) automatically when you plug them in, and are therefore as much at risk from data-scrambling by ransomware as the C: drive itself.
Jim Doss
Sadly, I can answer this through personal experience – Yes, the virus can get to files on external HDDs. It got to mine on a NAS, which isn’t ever directly connected to my computer, but through my router.
Jon
When did Sophos pick up Zepto? We were infected with Zepto on 4th July @ about 14:00. Sophos was fully uptodate but detected nothing.
Garry
I would also be interested to know when Sophos picked up Zepto, a customer of mine has just been hit with Zepto today at around 16:00 and also had a fully updated Sophos AV and PureMessage, Zepto arrived as a email with a docxm attachment which a user opened.
Paul Ducklin
As far as I can see it ought to have been stopped (including by generic threat blocking rules that are malware-independent, assuming they’re turned on).
Of course both of us can only speculate without digging into it more carefully…
…so may I therefore urge you to email Support (support AT sophos DOT com) so we can look into this?
Chris
We were hit with Locky on 6th July at 14:30 from an infected web link which called the js. Fully up-to-date Sophos AV and WebFilter
Anna Brading
Hi, sorry to hear that. Have you contacted Sophos Support? Details here: https://secure2.sophos.com/en-us/support/contact-support.aspx
Garry
Thanks for your suggestion Paul to log a call with Sophos, I have done that and continue the clean up process.
I connected the infected PC to an isolated internet connection off the domain this morning to aquire the most recent virus definitions (it was up to date as of 16:00 last night when we disconnected everything)
Sophos updated and then found a file in
C:\users\(the user)\appdata\local\temp\filarmon.exe and labelled it as a Troj/Agent-ASRN
not sure if this is the culprit yet but it’s looking likely.
Caleb
ESET is catching it and deleting it either through its email plugin or HTTP filter or memory scanner. ESET is doing a good job. Nothing against Sophos, just offering some feedback. I manage about 1200 ESET agents.
Oliver
We have been hit yesterday at 12:13, with fully up to date and fully licensed Sophos Firewall AND Endpoint Protection which checks ALL mail attachments on the mail server AND Endpoint Protection on the client AND word macros blocked. Luckily we have quite strict rights on network shares and a good backup, so there was no loss. But when will Sophos help?
Anna Brading
Hi Oliver, Sorry to hear that. Have you contacted Sophos Support? Details here: https://secure2.sophos.com/en-us/support/contact-support.aspx
They can help sort this for you.
Jim Doss
I got hit on 7/4. No ones fault but my own. I’m usually very careful, but let my guard down for a second and clicked on an attachment. Problem is, I was expecting one from a friend and, well, you know. The virus got to both of my internal HDDs and my NAS. I lost thousands of files and many thousands of photos. Photo loss added up to 15,556 files. Happily, I have almost 42,000 photo files that the virus didn’t get to.
I’ve since reformatted my SSD and installed two new HDDs in this computer. I’ll store the infected drives, hoping that some day a decryptor will become available.
Tom Slattery
Hi Thanks for all info above, still looking for the source of ours, but this is a pretty nasty ransom ware and it encrypted over 1 Million files in 2 hours before identified and stopped. Then came the huge cleanup. From experience the key with these is to identify the source machine running the .exe on your network, this one was harder and their was look on our side as the source machine was near me and the user had noticed desktop files renaming and so we investigating already when it was noticed on file server. Pulling network cable on source machine stops the encryption but lots damage done by then. The program .exe in our case was called Filermon.exe this is definitely the .exe so maybe this info will help another by going to processes on task manager and killing this if it running anywhere. or search for this, but mallwarebytes and mcafee already have this exe in their virus definitions, too late for us but may save many others, a lot of time and hassle.
Chainsaw
It sounds like you have to have a bunch of user-generated security holes to get this one (i.e. clicking on mystery links in documents, hiding extensions, enabling unknown macros, having the default action for script files “execute” instead of “edit). It’s not like it exploits a hole in jpeg decompression or something otherwise hard to defeat. Is this combination of bad security and user carelessness really that common in the corporate world? That’s sad.
Paul Ducklin
To be fair to the corporate world: some of these “user-generated security holes” are operating system defaults; and others have become part of the pattern of office life. (If you have to deal with dozens of invoices, contested invoices, payment demands, outgoing payments and so on every day, you probably open up any number of attachments from any number of sources, and in the vast majority of cases, nothing bad happens.)
That’s not an excuse, of course. Just an attempt to understand how procedures and practices evolve in the workplace.
henk
just got attacked today 20/7/2016. The current fee for the recovery key is !!!!! 2,5 bitcoin which is approx. 1500 euro !!!! . 6000 files infected which I can’t miss ! Does anyone thinks the price will go down after a while ??
Paul Ducklin
Hmmmmmmmmm…hard to say. Traditionally, the ransomware gangs put the price *up* after a while, assuming you are getting more desperate. Can’t advise you here, I’m afraid. Trying to second guess an extortionist is a tricky undertaking…sorry for your plight.
Mick
You’re lucky, we’ve been asked FOUR bitcoins.
Michelle
Got hit on Aug. 4 and asked for THREE bitcoins.
Alaska Saedelare
Been hit by Zepto last week but as far as I can tell, it DOESN’T at first contact a C&C site, but starts encryptioin immediately after D/L some additional .exe file. So no chance to catch the http communication to identify an infected machine. Can anyone confirm this? Is there a new variant of Zepto known to work like this? Thanks!
Loren Dorez
Has anyone see the weird hidden characters in the help file? Could this be used to jelp decrypt the files?
Paul Ducklin
I’m afraid not.
Loren Dorez
Darn. I have a customer who has this and it asking for 4 BC. The client was wanting to ignore my advice and pay the randsom until they found out the cost in USD. Luckily they have a backup for all but 1 External hard drive they plugged in and never include in the backup scheme :(
Martin
Governments should ban bit coin and any other way these crooks demand money until these company’s clean up their act. All the time there is a way to get cash without trace these scum low life will continue. Also about time Anti Virus companies got on top of it as these types of infections have been around a while customers pay for protection seems to me crooks both ends !
Paul Ducklin
Which “companies” are those? Are you seriously suggesting that Bitcoin (good luck with that!) would force the crooks to clean up their act? It would be easier to criminalise ransomware until the crooks cleaned up their act. Oh. We already did that.
Anonymous
The government cant do anything about it. Its not a company or located in any 1 country.
danish
my network is impacted with Zepto virus and i need to retrieve those files.please suggest
Paul Ducklin
You almost certainly have no way out except a backup (unless you are willing to pay).
danish
is it safe to pay crooks to get data . and is it like i have to pay for each file.
Paul Ducklin
They’re crooks. So if you pay there is no guarantee, no promise, no money back if it doesn’t work.
Generally speaking, you need to pay once for each computer that was infected, in order to recover (you hope) the files encrypted by that infection.
Should you pay? I am afraid that you are the only person who can make that decision. It’s a tough one. Do you have any backups anywhere you can use instead?
John Hart
Is it possible that one day we will be able to decrypt our infected Zepto files
John Hart
Paul Ducklin
Never say never. It has happened once or twice with other ransomware strains that decryption keys have been seized or leaked for free. But I suggest you work on the principle that it won’t happen in order to avoid disappointment. (This is not a “glass half empty/glass half full” situation. It’s more like “there’s a sip left at the bottom of the jug aand you may be able to drink it before it evaporates.”)
I guess you are really asking, “Is it worth backing up the scrambled Windows disks and keeping the backups disks for ever, just in case?” (It’s best to keep everything, as there may be cryptographic stuff outside the files, e.g. in the registry, that you will need as well.)
The answer to that question is, “I don’t know.”
My own inclination would be to wipe the disk clean, take a deep breath, and start over, on the rather unscientific grounds that the past can weigh you down. But I don’t know what’s at stake here. If I’d lost a bitcoin wallet with $10k of value in it, I would change my mind immediately, and I would definitely spend $50 on a backup disks that might end up being a complete waste, so I didn’t end up kicking myself if a decryption key were ever released :-)
jonathan flind
I never have opened any suspicious emails until one said ” Hi Jonathan I sent you an image”. I opened image and just got a blank page. 2 days later I found all my quotes and invoices all encrypted, all gone. I took my laptop to the computer repair man, he said it would have taken less than 20 seconds to corrupt my files by Zepto, and the only way to get them back was pay a ransom which is a no. Bad news is I haven’t backed anything up for a year, so make sure you back up and back up never pay any money to those crim’s.
Guy
I was contacted by a company to clean up and overhaul everything once they were hit with Zepto… it went through multiple machines and backup drives. I have one question… can it actually be reversed ? Their backup regime is what I would call non existent. Is there a way forward ?
Steven Crimmins
Guy, once ransomware encrypts a file it is as good as deleting it. Give them your money and you’ll still not get it back. Until someone decrypts the encryption, it is impossible to recover w/o some sort of surviving backup. I hear a shadow copy should still be good… that is if it was setup.
Paul Ducklin
If you pay, you may very well get your data back, though it may hurt to say so. The main ransomware crooks have made their “marketing pitch” by not running off with the money, so that word has got around that paying works. As for shadow copies, which are effectively local files, a lot of ransomware deliberately tries to wipe them first, so that door to recovery may well be closed.
t9p1
One of my clients just got hit, but it just left a bunch of zepto files and didn’t encrypt anything.
Fail. Lazy virus…
Jane Powell
I got the virus on my pc today – cant recall opening ANY dodgy email. I’ve saved a bunch of stuff on a stick – how can i be sure the virus isnt on the stick? Also does the virus infect Mac? We’ve scanned all the pc’s on the network but no sign it spread – how long is it on the pc before it acts?
cuffer
is there any knowledge / history of them using data they have encrypted, or do they just hope for ransom to be paid? what if you had some customer info that they encrypted? is there any history of them taking and using that info for other purposes than ransom?
Paul Ducklin
At the moment, at least, the trend is just to encrypt and go for the money, not to steal data as well. (That means the whole process is much faster because the crooks don’t need to upload anything.)
However, we have seen cases where people were hit with ransomware *because they were already infected* with some sort of zombie malware that included a “now install more malware” feature. If crooks turn a working zombie infection into a ransomware infection…who knows what they stole using the zombie before they implanted the ransomware?)
Dean Moncaster
I got hit yesterday with this virus ZEPTO….fully updated sophos and Sophos PureMessage.
Sophos is blissfully unaware of the virus….even though i have the virus file on my PC and in my email…
thanks sophos!
Anna Brading
So sorry to hear that Dean. Have you contacted Sophos Support? https://secure2.sophos.com/en-us/support/contact-support.aspx
Dean Moncaster
Hi Anna,
yes i submitted the virus to sophos just after it was received and it took about 30 hours to get an IDE. usually you guys are back within the hour! was it a toughy? I have cleaned up the network here and sent an advisory around, lets hope people dont do it again :D
Seretha
Is there any evidence that Zepto makes copies of your data elsewhere, or otherwise steals information? Or is it exclusively encryption?
markky
Is there any evidence that Zepto makes copies of your data elsewhere, or otherwise steals information? Or is it exclusively encryption?
Paul Ducklin
No version I am aware of also steals your data. We have seen ransomware that deliberately leaves behind a keylogger even after you’ve paid up and it has “cleaned” itself, so there is no rule, even amongst the crooks, that “ransomware should stick to its current business model” :-(
In fact, here’s a case of ransomware that deliberately left behind itself a password stealer that we wrote up back in June:
https://nakedsecurity.sophos.com/2016/06/20/ransomware-thats-100-pure-javascript-no-download-required/
cris
my computer was infected last Aug 25, 2016, 15:13
i used shadowexplorer to get my files that were infected but unfortunately i wasn’t able to get all the details of my files when it was infected. I got my files that is saved last Aug 24 of the same year.
Janette Dean
We were infected with this virus in August. Have decided to buy a new PC (have kept the hard drive in case a cure becomes available) Went to access Dropbox on my Samsung tablet after several months and the virus is in my Dropbox!!!!!!
Emre
You can rescue your DropBox files – you just need to mail their support the link of the “event” that changed your files and ask them to rollback the entire account to its state prior to that event. They will mail you to confirm you want this done – with a warning that any changes since that event will be lost – and once you confirm, your account will be as it was prior to encryption.
You can find details on how to do all of the above in their help sections.
Andy
So, given the likelihood of a business suffering from this why on earth wouldn’t people turn on versioning within their server? Ok I agree that it can be a ferocious beast to feed in terms of HDD space, but it should be pretty easy to turn everything back to a point in time shouldnt it? Im pretty sure server 2012 has this functionality built in