Thanks to Jagadeesh Chandraiah of SophosLabs for his work on this article.
Here’s another cautionary tale from Google Play.
The good news is that the malware in this story has now been removed by Google; the website it used to collect stolen data is offline; and a cautious user would probably have avoided the app in the first place.
The bad news, of course, is that the app fooled Google’s security checks, received Google’s imprimatur, and was accepted into the Play Store at all.
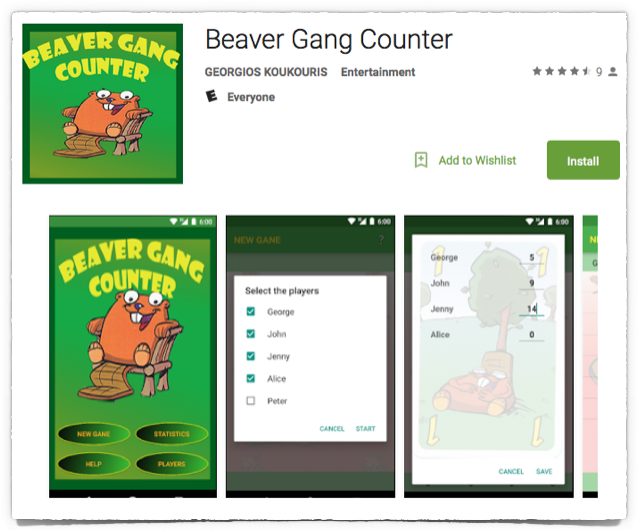
Here’s what you would have seen, back in May 2016 when no more than 10 people had tried the app, if you’d clicked on a link promoting it:
Image from 2016-05-12T23:22:16Z, recovered from the Googleusercontent cache
Beaver Gang Counter may sound an unlikely name for an app with an Entertainment – Everyone classification.
But if you are an avid post-modern gamer (by which we mean games of the board-and-card game sort that are quite deliberately played off-line and face-to-face), you might think it worth taking a look at.
Beaver Gang is a strategic card game for young and old, a contemporary spot of old-school gaming fun.
And fans of modern card and board games aren’t averse to apps that help them keep track of their gameplay, not only for fun but also to help them review the best strategies for the future.
What harm?
What harm to try out an apparently benign app that already has Google’s blessing?
When you run Beaver Gang Counter for the first time, you’ll probably spot the mistake that escaped the attention of reviewers from both Google and the cybercrooks:

There’s a spelling mistake right there in the main menu.
Even if you overlook that faux pas, and try to use the app, you’ll soon realise that you might as well not have bothered, because it doesn’t really do very much…
…so you’ll probably uninstall it and move on.
By then, however, it would be too late.
The Beaver Gang Counter malware explicitly targets users of Viber, a popular app that lets you make free calls, send free text messages, and more.
Like competing apps such as WhatsApp and Skype, you can make video calls, share images and join in multi-person chats.
According to Google Play, Viber currently has somewhere between 500 million and one billion installs, so there are plenty of Viber-equipped Android devices out there.
Once you load it, the Beaver Gang Counter malware raids your Viber directories and starts uploading your images to a website run by the crooks:
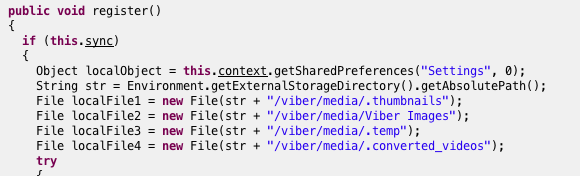
The malware raids your Viber directories and steals your images
Android apps can’t usually read each others’ data files, to prevent this sort of data-stealing malware from doing its dirty work.
But many apps store large files, such as videos, music and images, on your removable storage, usually an SD card.
That’s not only for convenience (so you can easily move them to other devices) but also to save space on the device itself (so you can install more apps).
Unfortunately, files on external storage aren’t locked down to specific apps by Android’s security subsystem.
Apps can read everything or nothing from your SD card, depending on whether they asked for the READ_EXTERNAL_STORAGE permission at install time.
If you’re wondering why Android doesn’t take as much trouble with SD card security, it’s because SD cards are supposed to be easy to remove and use in other devices, often to share data with completely different apps running on completely different operating systems. Locking individual files to specific apps on one device makes much less sense in that sort of environment.
What next?
We don’t think this malware seriously troubled anyone, and Google ejected it from the Play Store once its illicit “call home” behaviour became known.
Nevertheless, this story teaches us three things:
- Cybercrooks regularly manage to slip past Google Play’s up-front security checks.
- Apps can permanently harm your privacy, even if you only try them out briefly.
- External storage is less secure under Android than the storage in your device itself.
What to do?
- Avoid apps with a poor or non-existent reputation. Don’t trust an app about which no one yet seems to know anything.
- Stick to Google Play if you can. Despite this and other recent failures, it’s still safer than unregulated Android markets where anything goes.
- Consider using an Android anti-virus. The Sophos product is free, and protects you automatically from malicious and low-reputation apps.
- Avoid storing personal or private data onto your SD card. Android protects your data more strongly against malware when the data is stored on the device itself.

RavenKnowsBest
It’s good these things eventually get noticed & pulled from the Play Store.
Not long ago I outed a deliberately fraudulent app to Google. It purported to be an alternative client for LocalBitcoins.com. Upon opening the app for the first time, it tries to trick users into handing over the balance of their Bitcoin wallet on the site.
I researched the developer & discovered they were using freelance websites to solicit the development of this and other apps designed not to get filtered out for publication . They had several domains registered in different counties, all over the world.
All this added up to shady dealings & Google apparently agreed because I checked back shortly after reporting my findings & the app was gone from the Play Store.
Paul Ducklin
It may sound trite, but “if you see something, say something” is a good start.
OK, so Google screwed up. But if they can be persuaded to fix the mistake, that means the app vanishes – result!
Keiran
Good article, thanks for alerting. I remember Google saying we don’t need Antivirus, why didn’t they detect these now, ha ha
Paul Ducklin
Don’t laugh, but last year Google tried to define Android malware out of existence by introducing a new term for it: Potentially Harmful Applications. PHAs include categories such as: “spyware”, “backdoor”, “call_fraud”, “sms_fraud”, “phishing”, “DDoS” and “ransomware”. Or, as you and I might call it, “malware” :-)
https://nakedsecurity.sophos.com/2015/11/18/google-virustotal-now-with-autoanalysis-of-os-x-malware/
Dave
What if I don’t have an SD card? Is the security still the same for files created by e.g. Viber that it intends for the SD card, or are they secured from other applications because they didn’t actually go on an SD card?
Paul Ducklin
Errrrrrrrrr, I should know that answer, but I don’t. You still get an /sdcard directory on devices with no SD card, so that apps that insist on using it anyway don’t break. What I don’t remember is whether the Environment.getExternalStorageDirectory() you see in the malware code reports the fake SD card directory as if it were real external storage.
I’ll guess that Android writes files to your faux-external directory as if they were on a real SD card, i.e. without app-specific permissons. Anyone got a Nexus device with no SD card to test this? (My Nexus 7 has decided its battery no longer works.)
Bryan
Hate to post “me too” (like some brain-dead AOLer), but I’d be surprised if the delineation between mount point and actual directory impacts file permissions at all. Seems the distinction would be too uncommon to code for (albeit the Android flavor specific to that model could prove me wrong).
For clarification, I’ve not reviewed the malware code and assert that Android likely treats the directory no differently from how it would treat /dev/sd(b?)1 mounted at the same spot. When installing malware, YMMV :-)
sheryl
App looks crap, why does google play get so many more malware than ios ? What does iphone apps store do different from android ? or is it just because of popularity and huge number of android apps.