We’ve written about exploit kits on Naked Security many times before, because they’ve become a key part of the cybercriminal underworld.
As we explained at the start of 2016:
An exploit kit is a pre-packaged toolkit of malicious web pages that crooks can buy, license or lease for the purpose of distributing malware. […]
Instead of figuring out how to booby-trap … web pages so that visitors end up infected, [crooks use] pre-prepared attack code in an exploit kit to try out a series of known security holes, in the hope that one will succeed.
An exploit kit is usually delivered directly into a potential victim’s browser in the form of convoluted and hard-to-follow JavaScript, and automatically tries out a series of attacks, typically in the most likely sequence, until one of them works, or they’ve all failed.
Sadly, it’s not often we get to write about exploit kits fading away.
The last time we did that was at the end of 2013, when the infamous Blackhole exploit kit dropped rout of sight following the arrest of the crooks behind it.
However, it seems we do have a “good news” story for this week, given the apparent demise of the Angler exploit kit.
According to SophosLabs, Angler has been by far the most prevalent exploit kit this year…
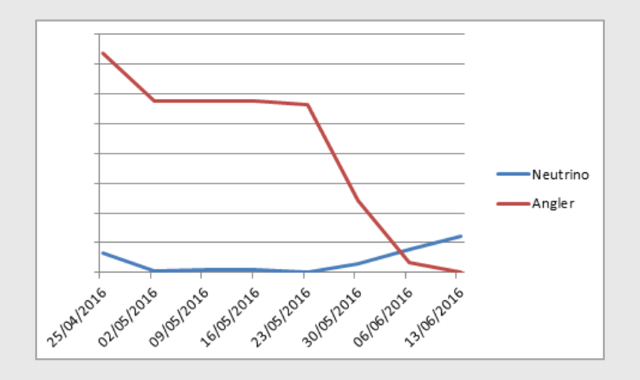
…at least until 2016-06-07T05:29:46Z, when our last hit for Angler was recorded.
Since then? Nothing!
The history of Angler
Angler first appeared in late 2013 as one of many exploit kits that sought to capture the market after Blackhole went offline.
Using a variety of obfuscation tricks to complicate detection, Angler launched its salvo of exploits at unpatched machines.
One of Angler’s favourite infection vehicles was the Adobe Flash browser plugin, including an attack using a zero-day exploit uncovered in the hack of hapless security company Hacking Team.
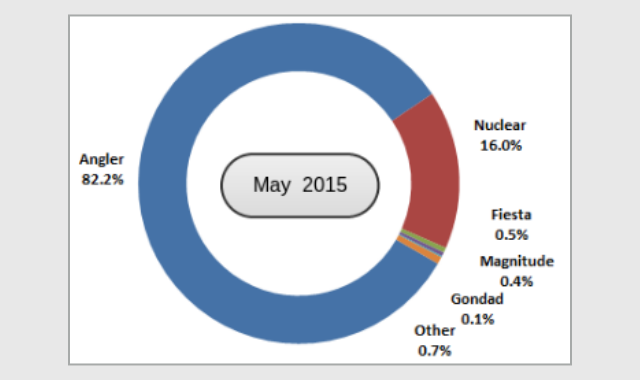
Angler grew in prevalence until it dominated the exploit landscape: in May 2015 Angler accounted for over 80% of exploit kit detections reported by SophosLabs.
For the past year, Angler has been delivering ransomware as its primary payload, infecting its unfortunate victims with data-scramblers such as TeslaCrypt and Locky.
At the start of 2016, we saw Angler’s prevalance dip dramatically, but back then we figured that the criminals behind Angler were simply taking a New Year’s vacation – prevalence levels soon went back up.
This time, Angler’s fall seems to be more permanent, accompanied by a rise in prevalence of a rival exploit kit called Neutrino (see graph above).
Apparently, the undergound price for spreading malware with Neutrino increased by about 20% at the same time, as you might expect if demand suddenly started to outstrip supply.
What happened?
What’s going on here?
Is this another case of a “change of heart”, as we saw when the crooks behind the TeslaCrypt ransomware revealed their master decryption key, so that the last wave of victims could decrypt their files for free?
We don’t think so.
We suspect that Angler’s disappearance is related to a recent, large-scale cybercrime crackdown in Russia, when Russia’s Federal Security Service (FSB) arrested 50 suspects suspected of being part of a criminal group that had stolen nearly $50 million by means of banking malware known as Lurk.
So, is Angler really dead?
Only time will tell.
After all, the fact that Angler dried up after the busts doesn’t prove that the busts were the reason.
And even if we never see Angler again, there are many other cybercrooks waiting to fill the void, a problem we’ve written about before.
What to do?
To boost your defences against exploit kits:
- Patch early, patch often. If you have already closed the holes that an exploit kit is programmed to try, all its alternatives will fail and the exploit kit will be useless.
- Remove unused browser plugins. If you don’t need Java (or Silverlight, or Flash) in your browser, uninstall the plugin. An exploit kit can’t attack a browser component that isn’t there.
- Use an active anti-virus and web filter. Good threat prevention tools will block the whole exploit kit, even if only one of its components (or associated web pages) is detected.

Tae
Last hit I got was on 6/3. Pretty steady till then.
Malcolm
Typo: “dominated the explpoit landscape” –> exploit (4th para in “The history of Angler”)
Anna Brading
Thanks, now fixed :-)