Sophos is aware of a widespread malicious email campaign sent out with subject lines like this:
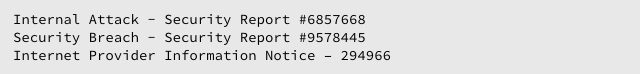
These emails claim to come from addresses such as:

Please note that this attack did not originate from Sophos, and there is no indication that we have been compromised in any way.
Unfortunately, the “From” address in an email is part of the email itself, just like the subject line or the message, so the email sender gets to choose whatever they want.
Cybercriminals often pick an official email address from a legitimate business that is somehow related to the subject line of their spam, or scam, or malware.
They do this in order to make their emails look more realistic at first sight.
As far as we can tell, most if not all of emails in this attack included malicious attachments with names such as:
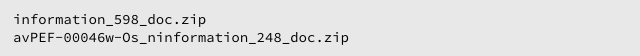
These infected ZIPs contained JavaScript files that would almost certainly try to infect you with ransomware if you were to open them.
Here’s our advice:
- The “From” address in emails is trivial to forge, a trick also known as “spoofing”. Sophos did not send these emails.
- For information on how to defend against ransomware, please see: How to stay protected against ransomware.
- To protect yourself against JavaScript attachments, please see: Ransomware in your inbox: the rise of malicious JavaScript attachment.
- Stay alert to unexpected emails, even if they appear to come from a reputable source, especially if they urge you to click a link or to open an attachment.
If you come across suspicious emails or attachments from this or any other malware attack and would like to report them to Sophos, please see our instructions on How to submit samples to Sophos.
Tom
What about sophos implementing SPF instead of us having to fo all the work for you guys???!!!