Passwords are supposed to keep our accounts secure, but many of us have lots of them and it’s difficult to remember them all.
So, naturally, people look for shortcuts, choosing simple-to-remember but also easy-to-crack passwords, making them essentially worthless.
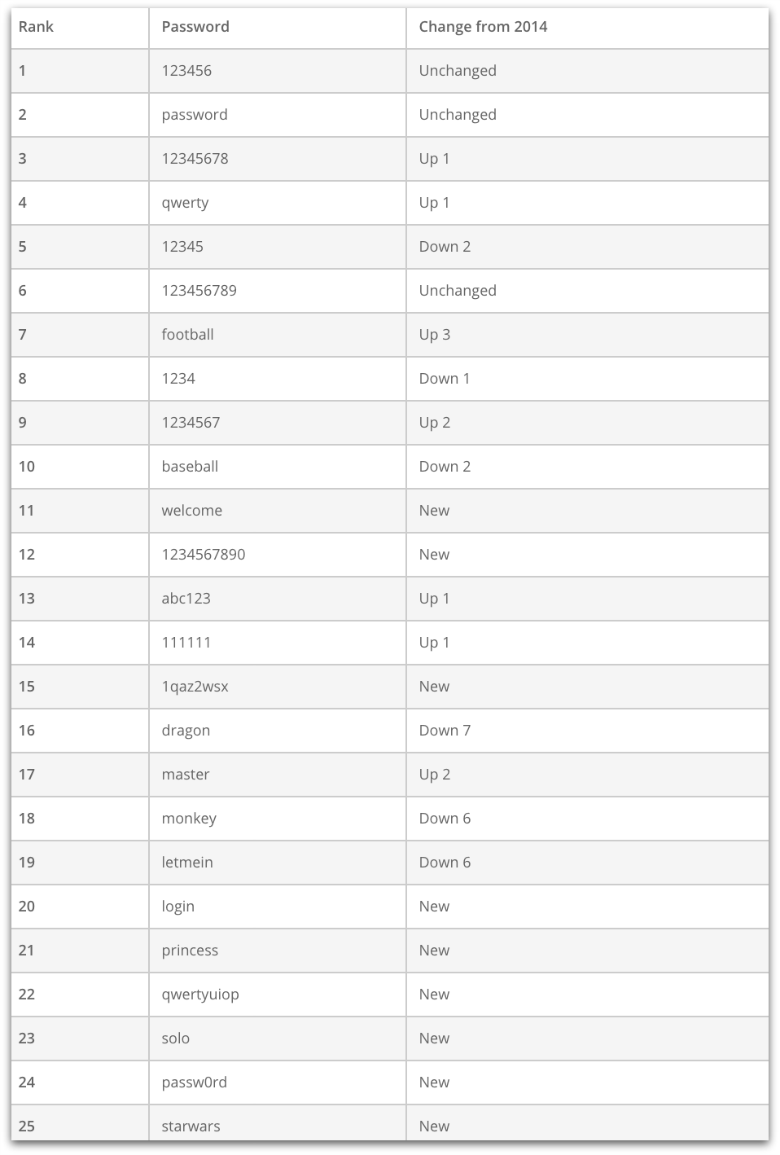
To demonstrate how bad people are at creating secure passwords, a password management company called SplashData has just released a list of the 25 worst passwords used in 2015, and it’s not pretty.
SplashData created its list of worst passwords by counting up the most common passwords out of over 2 million passwords leaked in the past year.*
And just like every year since 2011, when SplashData first released its list, the top two most common passwords (and therefore, the worst) are “123456” (#1) and “password” (#2).
Clearly, we’re still bad at creating secure passwords, despite all the warnings about data breaches and cybercriminals out to get us.
The list has remarkable consistency to last year’s: nine of the top 10 passwords from 2014 also made the top 10 for 2015 – “dragon” dropped from #9 to #16 – with some slight reordering (e.g., “12345” moved from #3 in 2014 to #5 on 2015’s list).
Others in the top 10 worst passwords of 2015 include “12345678” (#3), “qwerty” (#4), “football” (#7) and “baseball” (#10).
There are some new additions this year – “welcome” debuted at #11 on the list, and “1234567890” comes in at #12.
Other newcomers include “1qaz2wsx” (#15 – these characters come from the first two columns of the keyboard), and “qwertyuiop” (#22 – taken from the top row of letters on the keyboard from left to right).
Also new on the list are several passwords inspired by one of the year’s most popular cultural events – the release of the new “Star Wars” movie: “princess” (#21), “solo” (#23) and “starwars” (#25).
Some of the passwords on the 2015 list are longer than in past years – for example, the 10 characters in “1234567890.”
There could be a simple explanation for that – many websites now try to force us into creating stronger passwords through use of password strength meters and minimum character requirements.
But these methods fail too.
A 10-digit password has 1 million times more possible combinations than a four-digit password, but that’s not nearly complex enough to get in the way of password-cracking software.
As SplashData CEO Morgan Slain said, longer passwords based on simple patterns leave users just as vulnerable to hackers:
We have seen an effort by many people to be more secure by adding characters to passwords, but if these longer passwords are based on simple patterns they will put you in just as much risk of having your identity stolen by hackers.
So what can we do about the password problem?
Some technology companies, banks, websites and security researchers are trying to kill the password in favor of other forms of authentication, including biometric authentication by fingerprints, faces, irises, gestures and voices; and some weird-sounding ideas like using our thoughts or the unique patterns of our brain activity for authentication.
In the meantime, passwords are an unfortunate necessity, so we need to continue encouraging our friends and family to follow some pretty simple advice on how to create better, more secure passwords.
Tips for creating more secure passwords
1. Make your passwords hard to guess.
Avoid using things like your name, birthday, pet’s name, etc., that would be easy for another person to figure out. And don’t use those easy-to-guess words/numbers with trivial modifications, such as changing “a” to “@” and so on.
2. Make them as long and complex as you can.
Use at least 14 characters, mixing letters, numbers and special characters in hard-to-guess patterns. Another popular method is to combine several unrelated words or phrases, like the famous XKCD password correcthorsebatterystaple.
3. Consider using a password manager.
Password managers can generate long, complex and random passwords, and remember them for you. Just make sure to create a really strong password for the password manager itself (and consider using two-factor authentication if you can), so a crook can’t grab all your passwords at once.
4. One account, one password.
Criminals who get a hold of one of your passwords will try it out on multiple accounts. Don’t reuse passwords – each of your accounts should have a unique password.
Here is a short and straight-talking video that not only shows you how to pick a proper password, but also explains why you should bother.
(No video? Watch on YouTube. No audio? Click on the [CC] icon for subtitles.)
*The 2 million passwords used to compile the worst passwords list come from published lists of leaked passwords, representing a wide variety of sites, with no single leak representing a large portion of the sample. However, a SplashData spokesman said the company tries to exclude passwords from adult websites, “since those tend to be over-weighted in leaks, and the kinds of passwords people use on adult sites tend to be different from passwords they use on other sites (i.e., a lot more naughty!).”
Image of facepalm courtesy of Shutterstock.com.

wisekal
It’s a shame people still do this! It’s not hard to use one of the many great services out there like LastPass (which is also free) or 1Password. A good rule to live by when it comes to passwords (and it’s a simple one) – if you cannot remember it, chances are, it’s a decent password! Your privacy is important, so protect it that way!
GS
I have a couple of questions about this.
Firstly, how many of those passwords are just testers and throwaway passwords that people use for 5 minute access for a specific reason?
Secondly, you spoke of “One Account – One Password”. What about the likes of Google for example using one password across all related systems? i,e. Mail, YouTube, Maps, Ads, Business etc.
Paul Ducklin
Firstly, be wary of falling into the “5 minute access” trap. It’s still *your* account, and therefore it still has a legalistic and technical connection *to you* if it gets compromised. So unless you remember to go back and remove the account after the 5 minutes are up (assuming that’s even possible!), then it’s a “longer than 5 minutes, heck, could even be forever” account.
Secondly, I am not personally a big fan of what’s often called Single Sign On…precisely because it seems to violate the “one account – one password” rule. Having said that, using one password across Google, a different one across Facebook, and so on` is hugely different from having, say, the same password for your webmail service as for the local cricket club website.
GS
So where would you stand exactly on the Google password system for or against? As it does as you’ve stated violate the ‘One and One’ rule.
Also on a side note (completely unrelated) why does a security site / blog only use partial encryption? Ok it may only be the images but surely that’s still an access point for malvertising and / or eventual phishing?
Paul Ducklin
I think my answer speaks for itself. You can argue that Google’s password system is “one account, one password,” because the accounts are treated as parts of a whole. Or not, if you would prefer them separate – that’s a choice you’ll need to make. Outlook.com does soemthing similar for Outlook webmail and OneDrive storage. I think I’m ok with that.
As for our use of “partial encryption” – I haven’t noticed that myself . IIRC, when I browse with Firefox, I always see a green padlock in the address bar. Where and how are you seeing mixed content? (I’m not saying there isnt any…just that I can’t find any, at least right now. Perhaps I don’t know where, or how, to look? Would you mind sending a bit more info to tips@sophos.com?)
GS
Email sent.
Anonymous
Fortunately, the number of sites that make you register and choose a password for stupid reasons has gone down in recent years. There are fewer “must register to read this” sites, and a lot of online shopping sites now allow you to “check out as guest” without creating an account. I didn’t even have to set up a password to post this comment.
mattfast1
The fact that there are several different services under the same account (a la Google) isn’t relevant. It’s still one account that includes access to all of Google’s services.
The tricky part is when you use Google’s authentication to access 3rd party services via OpenID. That’s where you start to blur the line of One Account, One Password, even though you technically have a different password for the 3rd party site (your OAuth token), you don’t really have a different password since breaking your Google account allows access to all 3rd party sites using their OAuth services.
Anonymous
Well, since these are a list of leaked passwords, so these passwords are still active and have not been deleted by their creators. That “5-minute” password still probably has your name on it, so I’d be wary of making them with insecure passwords – even if you want to delete it minutes later. If you only need it for 5 minutes, mash on the keyboard in a text document, take 10 random-looking characters out of the mess, and paste it into the signup form and the login form. Then your “forever unused” account is at least hard to get into if you are unable to delete it.
As far as Google, it’s not really “one password many sites”. The real exposure of that is if one site is compromised and your password leaks, and someone can then use that password to try other sites you log into.
When you log in via Google, your actual password is not revealed to the third party. The third party receives confirmation direct from Google that you are who you say you are.
So it’s more akin to holding a LastPass account than it is using the same password across multiple sites – if ThisRandomSite uses Google for authentication and ThisRandomSite is breached, there is no useful information about your Google password at ThisRandomSite, nor is there any information about any passwords at any other sites. Your data at ThisRandomSite may be accessible to the hacker, but that’s it.
jkwilborn
When will they realize that they can’t force security down peoples throat. When I worked at a large financial company, they required all users to change their passwords every 30 days. This ended up with passwords like “mikejan”, “mikefeb” etc., since they kept them for a year. It was a disaster.
I’ve found sites, such as eBay that won’t let you use a password manager, i.e. can’t paste into the password field for login. I spoke to someone there and they stated something like ‘a more secure entry by requiring manual entry’. I advised them this an was ancient and poor security implementation. I’m sure this came from browsers automatically entering the login information. Also that I will not use their site until they update and conform to newer procedures. Did not hear anything back, can’t log in, so can’t delete my account!
Bryan
Can’t you open your password manager, read the ebay passwd, type it manually?
TryingtoStaySafe
Unfortunately, many people simply do not care about security. I have a relative who uses the same password for every account, simply because it is convenient. The response I get from most people about security and privacy is that it is a waste of time to worry about it, your information is all out there and easily accessible anyway. My concerns about passwords and keeping your own accounts and files secure are usually laughed off as paranoia. Everyone is too wrapped up in our high tech “instant gratification” lifestyle to give strong passwords a second thought!
Anonymous
Seems to me the inconvenience of creating a strong password is trivial compared to the massive inconvenience of having one’s identity stolen.
roy jones jr
Exactly what Anonymous said. Those that are being lazy with their passwords won’t be so lazy when they have to go on the long hard journey for identity theft recovery.
ultrajoesewell
Password managers don’t help when you have multiple devices and don’t have access to your password manager. For example, a password manager kept on my cell phone won’t help me at work where I am not allowed access to my cell phone, and the site is blocked.
The solution isn’t to make ludicrous demands on password content. That just makes the need to request resets that much greater. Making them random letters, as many password generators do, makes that worse. A complete move away from passwords needs to happen.
Paul Ducklin
Many, if not most, password managers need neither cloud nor mobile phone access. They can run right on your laptop, alongside your browser, but separate from it. (Apple’s KeyChain App is an example.)
Meaple
I think we need to move away from passwords and use more of tokens or security keys. Personally, I use LastPass but I’m not a heavy user for it. I always have a Yubikey setup with 2FA for services like LastPass and Google. I certainly would prefer it if I use a security token/key to log in rather than using a password. It’s a slight inconvenience but keeps a hacker out as they cannot have the same thing as me.
Ronny Vasquez
Well, let the users put their passwords without a policy, is like give a child the responsibility of the keys of your house lol.
Emma Rosemarry
We all know about setting strong passwords but we do not follow such trends generally to avoid confusions or being lazy in remembering long passwords. The blog shares accustomed approach towards setting a strong password. A strong password not only prevents the password from being hacked but also minimizes the risk of data breaches.
A password with only alphabetical characters from Uppercase (A-Z), or the lower case (a-z) counts a total number of 52 alphabets. A combination of only alphanumeric characters accounts for 62 characters including 0-9 from the above mentioned uppercase and lowercase characters. When this combination of alphanumeric and special characters (11) the count increases to 73 characters.
A strong password should not be less than 10 characters and the maximum limit should not be less than 128 characters. For a hacker to crack the password the probability of a 10-character password is 62% less than hacking a 4-character password. We should also not use repetitive characters as it increases the probability of the password being hacked. We should also refrain from the automatic and social logins for preventing the password from being hacked. We can also add multiple challenge responses for adding more security. We should often change passwords with a period not more than 90 days.
“Treat your password like your toothbrush. Don’t let anybody else use it, and get a new one every three months”.
I have put forward my thoughts as a reader to enhance the knowledge of the readers to help empower all of us to protect ourselves online.