Thanks to James Wyke of SophosLabs for doing the hard parts of this article.
Making malware predictions is a popular but often frustrating pastime.
It sometimes feels as if saying “X will happen” simultaneously makes it true and untrue.
As though some crooks figure, “Well, if that’s where you’re focusing your attention, I shall go elsewhere,” while others say, “What a jolly good idea, I must try it at once.”
But there’s one malware delivery mechanism that we think will be in the news fairly regularly throughout 2016, not perhaps as the most likely vehicle for crooks to infect your computer, but as one of the most frustrating.
We’re talking about malvertising, short for malicious online advertising, which is where usually-trustworthy sites temporarily go rogue because one of the ads they display turns out to be booby-trapped, and tries to foist malware or potentially unwanted content on your computer.
WHERE MALVERTS COME FROM
It’s not hard to see how malverts can happen, even if almost everyone in the advertising chain is trying to play by the rules.
Forbes, for example, was a recent high-profile victim of a poisoned-ad attack – a two-sided attack, really, because Forbes ended up being both victim and perpetrator.
The publication’s website, and brand, was hijacked and embarrassed by the crooks; at the same time, the Forbes website became a potential infection vector for cybercrooks.
Remember that when we talk about malvertising, we’re not just talking about scammy diet ads with improbable weight loss claims.
We’re not even talking about those free gift cards you’ve been “awarded”.
We’re talking about a sequence like this:
- Crook hacks an ad delivery server, or signs a fraudulent contract with no intention of complying with the rules.
- Crook uploads an ad with malicious content, such as booby-trapped JavaScript or Flash.
- Ad network accepts the ad and inserts it into the database of options to serve for various customers.
- Ad network customers’ websites occasionally pull and display the malicious ad instead of a legitimate one.
- Users visiting any of the websites using the affected ad network at the time are placed in danger.
Of course, what you see as a user is that you visit a site you trust, yet your anti-virus goes off. (Or not.)
So the “crook” or “hacker,” as far as you are concerned, is company whose URL is in the address bar and whose logo appears proudly at the top of the screen.
Interestingly, when we went looking for screenshots to illustrate the abovementioned poisoned ad problem on Forbes, we found that the “foistware” offered up in the story wasn’t actually malware, but was a risky proposition nevertheless:
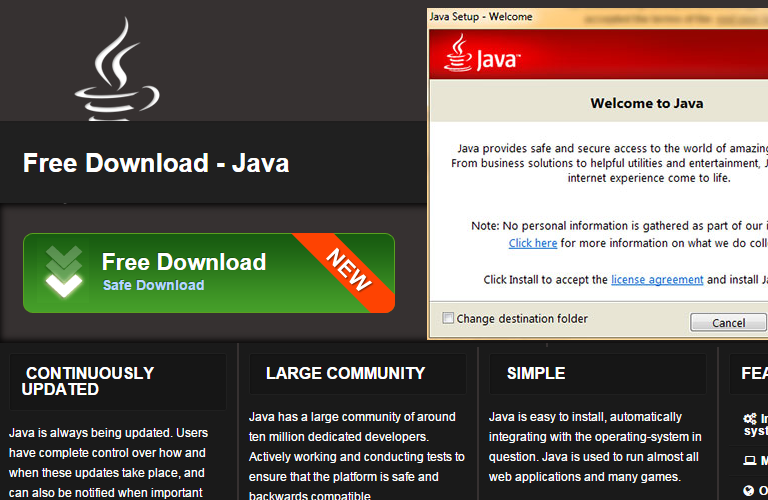
The website promised us a Safe Download, and pretended to be a legitimate installer (the Java Setup window in the screenshot above, however, is just an image inside the web page) and we ended up, to our surprise, with a byte-for-byte perfect copy of the Java Runtime Environment installer.
However, this installer delivered Oracle’s official security update from October 2014, which was already superseded back in January 2015.
By applying the “update” we’d have downgraded ourselves by more than a year’s worth of Java patches – even regressing to the POODLE bug – and perhaps that’s what the site had in mind, hoping that computers that had once been patched would unintentionally rewind their security and thus be more vulnerable to other attacks.
WHY CROOKS LOVE MALVERTS
As you can imagine, crooks love this sort of malware delivery mechanism for a number of reasons:
- One poisoned ad template on one insecure ad server could end up being distributed via hundreds or thousands of websites that use the ad network concerned.
- Popular sites typically use dozens of different ad networks, and only one ad network needs to be compromised at any time to put the entire user community at risk.
- Users won’t see the poisoned ads predictably, because ad networks vary content by time, visitor, location and more, so that identifying the source of the problem is harder.
- Threat researchers won’t necessarily get matching results when investigating malvertising reports, so that taking down the offending content is harder.
- Malverts typically poison legitimate, trusted, high-traffic sites, yet with no need to hack into the main site itself.
- Someone else pays for the bandwidth.
That’s why a lot of people use adblockers.
Sure, lots of people run adblockers mainly because they don’t like ads and consider them annoying, trite or even insulting.
But adblockers also improve security.
The logic is simple: malverts are a subset of adverts; adblockers block adverts; ergo, adblockers block malware, too.
And why not?
THE COST OF FREE
The irony is that companies that rely on ad networks for revenue dislike adblockers as much as you dislike ads, so as a community we are at an impasse.
The theory is that free content, subsidised by ads, will start to become less and less common if we block ads, because there won’t be any money left in “free” any more.
That would be a reasonable point, were it not for the fact that in the abovementioned Forbes case…
…the reporter claims that the malvertising came immediately after Forbes’s plea to turn off adblocking, to protect its “free content” revenue stream.
But tests run by SophosLabs very quickly revealed well over 100 different ad-serving domains that Forbes uses on repeat visits, so that turning off your adblocker is a much riskier proposition than you might at first think.
In a world that works this way, telling users to turn off adblocking because “it’s better for everyone” is a bit like telling them to turn off their anti-virus in case it gets in the way of forthcoming software installs. (Don’t do this! Find another product instead that takes security more seriously!)
The problem with security loopholes is that crooks quickly learn to leap through them.

Feorlen
I wrote my own post on this subject just yesterday, because so many people don’t recognize the problem. “It’s just an ad” these days is in the same category of “I don’t have anything to hide” is about privacy, seemingly innocuous things that actually have the potential to cause great damage.
The one thing I’m not seeing as many of us security-aware folks saying in clear words is what, exactly, those bad effects might be. Sure, if you hunt around you can find reports of some kit in use, but mostly what I see is “Ewww Malware Bad, RUN!” (Not that that’s a reaction to be discouraged, honestly.)
Your post is an excellent non-expert discussion of why more people should consider ad blockers even if they don’t care whether or not they see ads. Do you have any similarly general posts you could reference about what could happen as a result? I found one about ransomware, it would be nice to have a few others.
Paul Ducklin
Angler exploit kit…that would be the sort of content you probably wouldn’t want in a poisoned ad…
https://nakedsecurity.sophos.com/2015/07/21/beyond-the-breaches-understanding-the-angler-exploit-kit/
feorlen
That post has some excellent links to real-world malware badness more people should know about. Trying to wrap my head around it is what started me blogging about security. Thanks!
bob
Always enjoy your articles, Paul.
As a security measure, I treat web page ads the same as email links: Never click! And forcing a visitor to turn off his ad blocker is self-defeating. The old adage: “You can lead a horse to water but you can’t make him drink” applies here. Sites can make us display ads but they can’t make us look at them. And visitors forced to display ads will make a special effort to NOT look and certainly not click on one. And maybe even resent and avoid the company being promoted.
I’ve encountered sites that won’t run if ad blockers are on. I first try to find a different source for my subject mater. Failing in that, I turn off the ad blocker, avoid looking at the ads and when I’m done with that site, I close the browser and delete cookies. I won’t be forced to shop or leave a trail. The site may get paid for displaying the ad to me, but the advertiser has wasted his money. ( I also immediately leave a site that blocks content a second after opening with a “Please sign up” or “”provide feedback” banner.)
Greenaum
Yup, if an advertiser goes out of their way to annoy me, they’re even less likely to get a sale. Actually I’ve been on the Internet 20 years, and never bought anything from an online ad, ever.
But there’s plenty of stupid people on the net too, and ads are often aimed at them. In that case, being annoying might work.
For the issue of sites that grey-out, with some annoying banner popping up in front, in Firefox you can right-click, “inspect element”, and select the layers in question. You can then delete them from the page’s source code, and read the page normally. Works nearly every time. Even if you’re not an expert, you can figure it out with a bit of experimenting. Adblock Plus even lets you hide particular elements like that, since deleting by hand isn’t permanent, only affects the page as long as it’s loaded.
But still, makes things easier.
ejhonda
I’ve stopped engaging Forbes – both their website and their Twitter feed – due to their adblocker stance. Even when I whitelisted Forbes’ pages, it would still not let me on the site until I totally disabled AdBlock Plus. So, I walked away, and will from any other site that doesn’t let me control the security of my endpoint.
Not a moocher
So in other words you expect companies to give you everything for free. Because clearly these companies have found free employees, free insurance, free servers, free electricity, free business licences etc etc just so you can continue accessing their content for free.
That attitude really irks me. This attitude amongst a set of internet users who truly believe the internet is there to give the everything for free. When those same people work for free – then they can gripe. Until then they are nothing more than moochers.
ejhonda
Yeah, that’s exactly what I said, Mr. Forbes.
Paul Ducklin
To be fair to the OP, he explicitly stated security as his concern here. He didn’t say or imply that he expected to be given everything (or even anything) for free, nor did he say that he resented having to “pay in kind” for free content.
In fact, he said that he was willing to allow Forbes to send him ads -and he even tried allowlisting the site. He just wasn’t ready to turn off his adblocker *altogether*, which is what he said Forbes expected him to do.
Billy Reuben
No, we don’t expect companies to give us everything for free. But neither should companies expect us to sacrifice our safety for their product. It’s a risk evaluation. And if what you’re offering is, in my estimation not worth the price, down the road I go. As long as there are choices, people will avail themselves of them. Build a better mousetrap, Comrade.
Mark
The attitude that irks me is that anyone providing web content is entitled to be lazy, sling banners from an ad network all over their site, and then rack up the cash. If you can’t be bothered to curate your ad content, and serve your ads in a format that doesn’t irritate users or, at worse, risk their online security, then no, you aren’t automatically entitled to an income. If you can’t find a better way to monetise your content, then frankly, you deserve to go out of business and the internet will not miss you.
My website makes an income from affiliate links, but I actually bother to place those myself. No ad blocker will ever trouble me, because I’m not serving ad network garbage, and my links are to services my visitors actually want.
meru
Curious…I wonder if Forbes’ site was unable to detect the whitelisting? That seems more likely than that they really wanted you to disable Adblock. After all, your blocking ads on their competitors’ pages is to their advantage. Anyone know how the signals from Adblock work? Can a site detect that it’s been whitelisted?
Mark
The adblock doesn’t send any signal to a site that it’s been whitelisted, it just doesn’t block the ads on that site. Websites can’t detect that an adblocker is installed, they can only detect when the ads on their site have been tampered with.
Greenaum
WTF kind of site allows Javascript in it’s ads? A not very good one, obviously. This is essentially a cross-site script attack, in nature if not execution. The fault is of the website owner, who accepts code from third parties without checking it.
A company should be held responsible for it’s Internet presence. Legally in particular. So if a company are too lazy or stupid to encrypt customer account details, or don’t even bother controlling access to that data (the Weev / Apple case), then THEY should be punished, heavily, for any losses anyone suffers.
If that was the case, they’d clean this shit up quickly. Diktats would be sent out, and compliance would occur. It wouldn’t be left as some boring issue that only the nerds in IT care about.
You get companies to act through threatening their profits. In this case, people are suffering. Why is it always that companies get away with the most lax behaviour? If a bank didn’t bother locking their safe, they’d get into trouble with the law, and be held liable for their customers’ losses. Should be the same with computers. It’s about time there was a computer law that actually helps the public.
Andrew Robinson
If the world wanted to, they could easily resolve this problem, but the world allows Big Business and greed to get in the way of fixing this. What is the resolution? Make all ads the same, restricting them all to an x-pixel wide by y-pixel high animated gif. No JavaScript or Flash or Java — no code of any kind — would be allowed or needed. It wouldn’t hurt advertisers revenue whatsoever and we would be protected from harm instead of being exposed to it.
Jim
I’m not sure you can go that far. The world of advertising is sophisticated and cutthroat. They need to stay ahead of the competition.
I’m in line with your sentiment, I’m just not sure I can fully support it.
Sammie
A shame that ISPs do not provide ‘ad blocking’ as a service as I would love to be able to avail of this service. Also it would save plenty on the bandwidth and prevent malicious content from being downloaded onto the local machine.
Paul Ducklin
Some ISPs and cloud security providers (including Sophos, as it happens :-) have cloud-based web filtering solutions, where we do the filtering for you before it reaches your network. You get to tune the filtering to suit yourself, so you can block or not block whatever you choose.
Some people prefer to do the filtering at the edge of their own network, for privacy and control (it means that what’s getting filtered is your own business); others prefer the cloud approach of filtering before the traffic reaches their network at all, for safety and efficiency (it means that you don’t need to receive traffic only to discard it, and it gets rid of obviously risky content earlier on, as you say).
For example: https://secure2.sophos.com/en-us/products/cloud.aspx
(Click on the square tagged “Web Gateway”.)
Klaatu
Why is it I sometimes see that dam AdChoice on some web sites and not others ?
It’s a real pain
Martin
It’s time for a new business model.
Access for free for those who don’t use an adblocker; access by subscription only for those who do.
It’s a variation on displaying the first paragraph or two for free, as a teaser, and requiring access by subscription only for the balance of the article.
The two models could be combined.
Paul Ducklin
There are sites that do that already. Only time will tell how many adblocker users will routinely pay for what they used to get for free…
David Pottage
@Martin: The business model of requiring site visitors who use an ad-blocker to buy a subscription has been tried with only limited success. I think that if it becomes widespread it will just lead to the development of better ad-blockers that are able to pretend that an ad has been shown, when it was in fact hidden from the user.
I think a better business model to pursue would be an ad-network that better curates the content on it to keep users safe. If such an network existed, then I would happily white-list them, and I would encourage the major ad-blockers to white-list them by default.
The sort of curation I am thinking of, is only allowing limited html and static content such as images and video. The only JavaScript allowed would be written or approved by the network to do simple things like starting video playback when the user clicks.
Jim
I’m not sure ad-blockers are the RIGHT solution to this problem. I would think that advertisements could submit to some certification authority. Then, ad-blocking companies’ offerings could verify the certs, and only allow certified ads to show (as another option for the users).
Problem is that the certification authority better be doing their job, and doing it well. But, if they did, the whole security argument could disappear (except for day-zero malware, but we’re all vulnerable to those no matter what we do).
roy jones jr
I get that “marketing and sales” has a place in the world. But holy crap man, its really out of control online.
Anonymous
I think there’s two issues to consider here. One is the stated issue of malvertising. The other issue is site usability. Some sites are so packed full of ads, they are distracting. I don’t even go on CNN’s website anymore because much of their news articles are now video enabled–by default. I just wanted to read the article attached, not watch a video segment, and not have to try and catch the video–or ad–before it plays.
Jared Heath
There is no debate that advertising causes malware…specifically crypto locker events. We have had more than one that happened via web ads without any question (I am on the security team). Forbes, Wired, and anybody else who wants to turn away people can go ahead and sing kum-b-ya for all I care.
Adblocking stays ‘on’ for me until ads flow through the site hosting them, compromising THEM as well. Also, it would be nice if the ad networks with stop running scripts.