Ransomware has become one of the most widespread and damaging threats that Internet users face. Since the infamous CryptoLocker first appeared in 2013, we’ve seen a new era of file-encrypting ransomware variants delivered through spam messages and exploit kits, extorting money from home users and businesses alike.
The current wave of ransomware families can have their roots traced back to the early days of fake antivirus, through Locker variants and finally to the file-encrypting variants that are prevalent today. Each distinct category of malware has shared a common goal – to extort money from victims through social engineering and outright intimidation.
SophosLabs has published new research examining the recent evolution in file-encrypting ransomware, in our paper titled The Current State of Ransomware. We look at the most prevalent variants including CryptoWall, TorrentLocker, CTB-Locker and TeslaCrypt – as well more obscure variants that employ novel or interesting techniques. In this blog post, the first in a series about ransomware, we take an in-depth look at CryptoWall.
CryptoWall
CryptoWall is a family of file-encrypting Ransomware that first appeared in early 2014. It is notable for its use of unbreakable AES encryption, unique CHM infection mechanism, and robust C2 activity over the Tor anonymous network. The miscreants running the CryptoWall operation also provide a free single-use decryption service to prove they hold the keys necessary to restore the hijacked files.
CryptoWall gained notoriety after the downfall of the infamous CryptoLocker, which was later taken down by Operation Tovar. It used to appear under different names such as Cryptorbit, CryptoDefense, CryptoWall 2.0 and CryptoWall 3.0, among others.
It is widely distributed using various exploit kits, spam campaigns and malvertising techniques. Initial variants used an RSA public key, generated on the command and control server, for file encryption. Later variants, however, including CryptoWall 3.0, use an AES key for file encryption and further encrypt the AES key using a unique public key generated on the server – making it impossible to get to the actual key needed to decrypt the files.
CryptoWall 3.0 uses I2P network proxies for communicating with the live command and control server and Tor network for payments using Bitcoins, which makes it even harder for antivirus to trace back the malware author, as I2P uses anonymity networks.
Infection Vectors
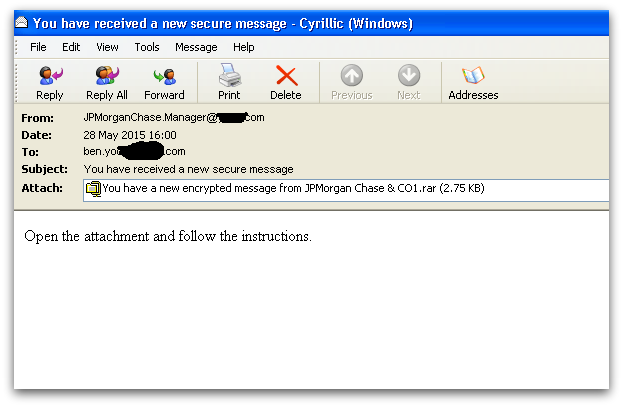
Earlier CryptoWall infections were almost always distributed via exploit kits. Another recent infection vector is a spam attachment that contains a CHM file which links to the CryptoWall payload.
The RAR attachment contains a CHM file which, upon opening, downloads the CryptoWall binary and copies itself into the %temp% folder. The CHM file type is basically an interactive html file that is compressed inside a CHM container. It can also hold many other files inside it such javascript or image files, etc.
Figure 1 shows one example of a spam email that contains a CHM file inside a RAR attachment. The user is often fooled into opening the attachment, assuming it’s from a legitimate financial institution. However, in actual fact, downloading the attachment causes malware to download in the background, as shown in Figure 2.
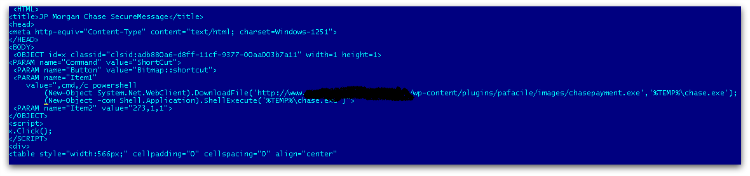
Execution
On disk, the CryptoWall binary is usually compressed or encoded with lots of useless instructions and anti-emulation tricks which are inserted deliberately to break AV engine protection.
On execution, it first launches a new instance of the explorer.exe process, injects its unpacked CryptoWall binary and executes the injected code. The original process exits by itself after launching the injected explorer process.
Next, it makes sure there is no way to recover encrypted files by deleting volume shadow copies using the vssadmin.exe tool.
vssadmin.exe Delete Shadows /All /Quiet
The original binary is copied into various locations in the system, such as:
<%appdata%>, <%startup%> and <%rootdrive%>/random_folder/
These copies are then added in the auto start key, which makes them persistent even after the machine is rebooted.
Next, it launches a new legitimate svchost.exe process with user privilege (not system privilege which could be launched and runs as a child process under services.exe) and injects its malicious binary code into the newly launched svchost process.
It tries to connects to the I2P proxies to find a live command and control server using a hash value that is created by taking a randomly generated number followed by a unique identification value. This is generated using system-specific information such as computer name, OS version, processor type, volume serial number, etc.
Once the server replies with the public key, generated specifically for the infected computer, it displays ransom notes in the language based on the geolocation of the machine IP address.
Once the public key is granted, it starts the file encryption thread – dropping ransom notes in all the directories where the user files have been encrypted.
Finally, it launches Internet Explorer to show the ransom notes, before the hollowed svchost process gets killed by itself.
Encryption
CryptoWall has a big list of file extension types for encryption, examples of which are listed below:
xls, wpd, wb2, txt, tex, swf, sql, rtf, RAW, ppt, png, pem, pdf, pdb, PAS, odt, obj, msg, mpg, mp3, lua, key, jpg, hpp, gif, eps, DTD, doc, der, crt, cpp, cer, bmp, bay, avi, ava, ass, asp, js, py, pl, db, c, h, ps, cs, m, rm.
CryptoWall 3.0 file encryption is slightly different from in the 2.0 version. In 2.0, the user files are encrypted directly using public key but in 3.0 a local symmetric AES 256 key is used for file encryption. This key is further encrypted using the public key in order to avoid revealing the AES key – encrypting in this way makes the process much faster and more efficient.
For every file encryption, CryptoWall 3.0 first copies the same file with an additional random character, encrypts the file content and writes it back, before deleting the original file.
Every encrypted file starts with a hash value of the public key received from the server, followed by an AES 256 encrypted key using the public key.
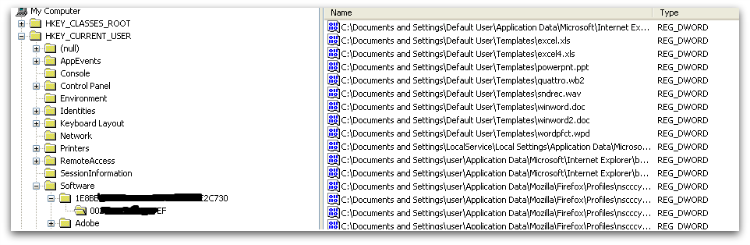
It also saves all the encrypted filenames under the below registry key:
HKCU\Software\<unique Identifier>\ as shown in Figure 3.
Network Communication
CryptoWall 3.0 uses I2P network proxies and hardcoded URLs to connect to its live command and control server, making multiple connections to the command and control server before and after the file encryption.
proxy1-1-1.i2p
proxy2-2-2.i2p
proxy3-3-3.i2p
proxy4-4-4.i2p
proxy5-5-5.i2p
It first sends user-specific identifier information and registers the infected machine, before fetching the public key and storing it in the registry after importing it. Based on the public key, CryptoWall 3.0 generates a unique ID for the infected user so they can be identified (when they pay, for example).
Unlike CryptoWall 3.0, older variants use hardcoded domains in the binary to receive the public key from the command and control server.
Ransom Demand
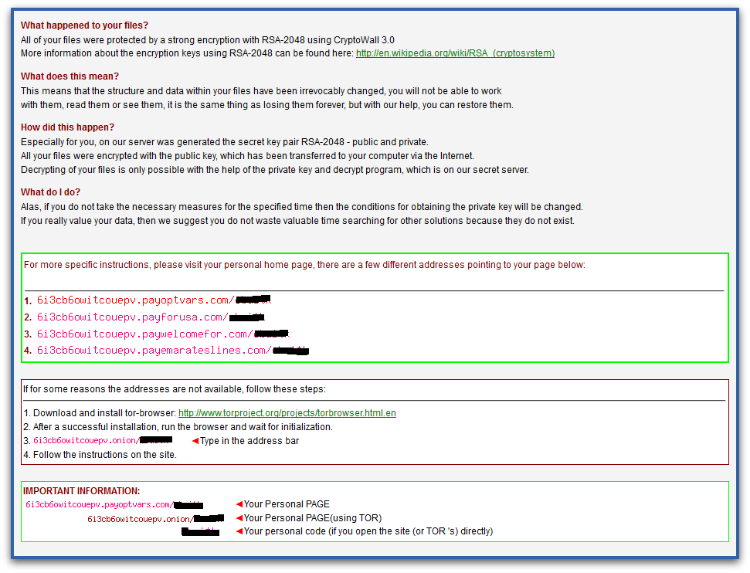
Once all the files are encrypted, CryptoWall 3.0 displays ransom notes which give instructions about how to make payment. The text content is hardcoded in the binary itself and adds generated Tor links and user-specific ID to it. As mentioned previously, the identifier generated by the command and control server is unique to the infected user, in order to identify the user machine.
The same ransom demand text is written into several files with “DECRYPT_INSTRUCTIONS” in their file names, and is displayed in three different applications – the web browser, a text file and a png in the image viewer, as shown in Figures 4 and 5.
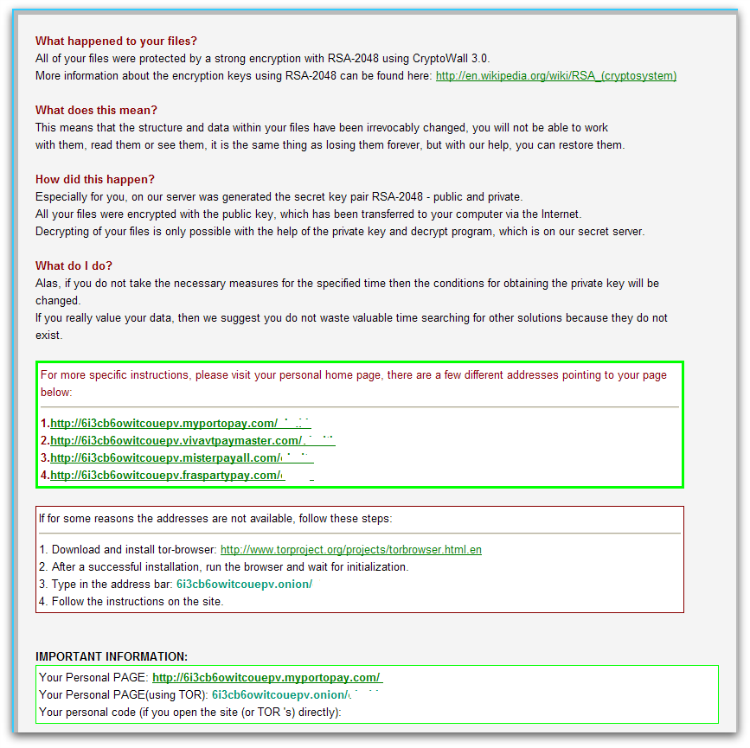
Ransom Payment
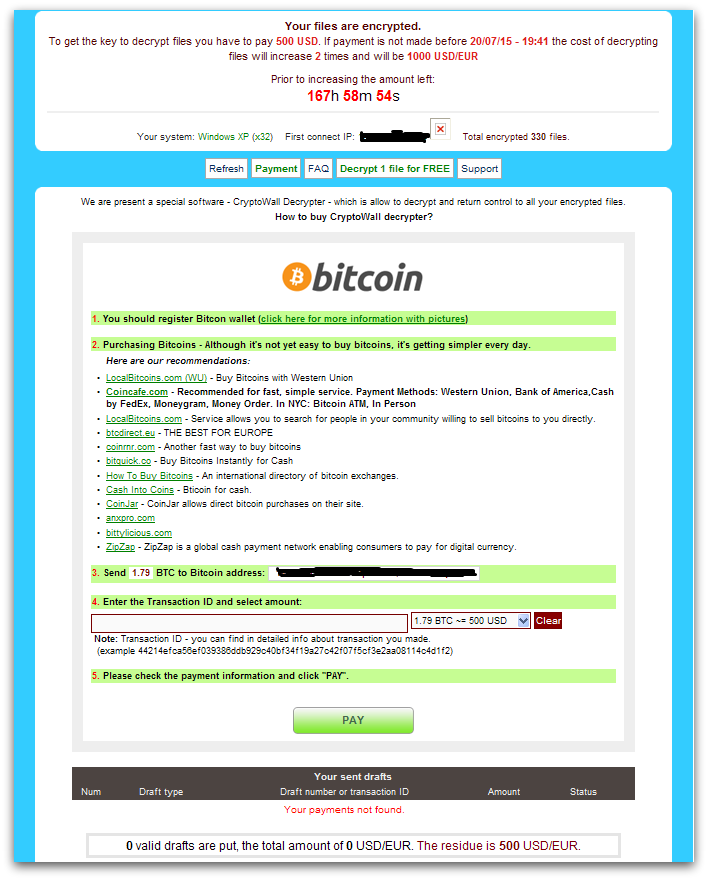
As with most Ransomware, payment is made with Bitcoins as shown in Figure 6 and the instructions are accessed through Tor. Since the actual AES key is encrypted further by a public key, it is impossible to decrypt without the private key.
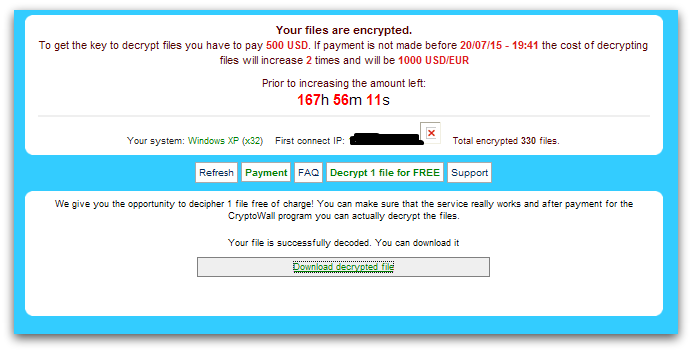
The CryptoWall author provides a free decryption service as shown in Figure 7, in order to convince the infected user to believe that they have the key to decrypt. The victim can then upload one encrypted file to their given link in order to get a decrypted version of the file back.
Below is the screenshot of a “free decryption service” webpage.
Statistics
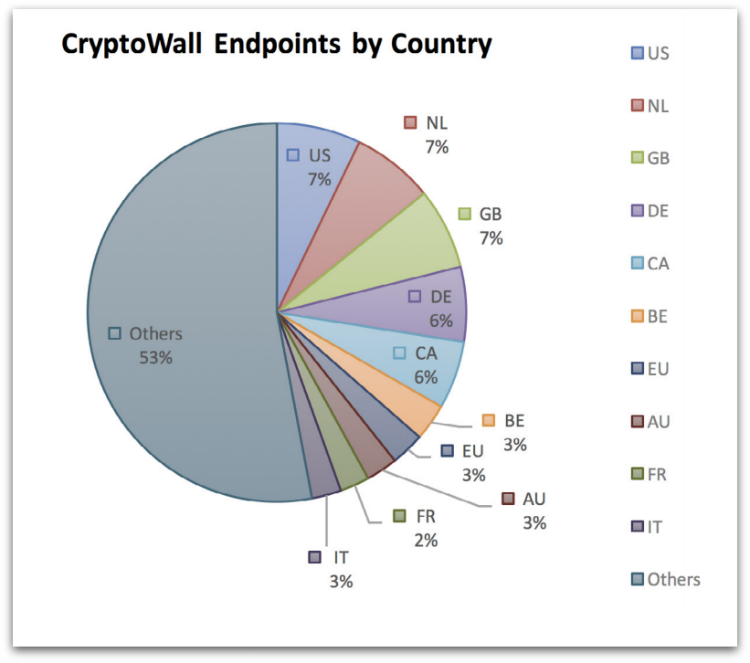
CryptoWall infections are seen all around the world due to its widespread infection mechanisms. North America is most affected, with the US and Canada making up 13% of infections. Great Britain, the Netherlands and Germany also feature with 7%, 7% and 6% respectively.
Protection
Sophos protects against CryptoWall at runtime using HIPS technology with HPmal/Ransom-I, HPmal/Ransom-O, HPmal/Ransom-R and statically with a variety of detection names including: Mal/Ransom-* and Troj/Ransom-*.
These HIPS signatures often don’t require any updates as they detects on the unpacked memory code irrespective of files on disk that are either packed, obfuscated or encrypted.
Hence having Sophos HIPS technology enabled is strongly recommended to block ransomware proactively.
If you suspect you’ve been compromised by ransomware, you can remove the malware using our Free Virus Removal Tool. Sadly, there’s not much you can do to get your files back yourself as the encryption is often too strong to crack, so it’s your decision about whether or not you want to pay to retrieve them.
Apart from having your antivirus up to date, there are additional system changes to help prevent or disarm ransomware infections that a user can apply.
1. Back up your files.
The best way to ensure you do not lose your files to ransomware is to back them up regularly. Storing your backup separately is also key – as discussed, some ransomware variants delete Windows shadow copies of files as a further tactic to prevent your recovery, so you need to store your backup offline.
2. Apply windows and other software updates regularly.
Keep your system and applications up to date. This gives you the best chance to avoid your system being exploited using drive-by download attacks and software (particularly Adobe Flash, Microsoft Silverlight, Web Browser, etc.) vulnerabilities which are known for installing ransomware.
3. Avoid clicking untrusted email links or opening unsolicited email attachments.
Most ransomware arrives via spam email either by clicking the links or as attachments. Having a good email anti-virus scanner would also proactively block compromised or malicious website links or binary attachments that lead to ransomware.
4. Disable ActiveX content in Microsoft Office applications such as Word, Excel, etc.
We’ve seen many malicious documents that contain macros which can further download ransomware silently in the background.
5. Install a firewall, block Tor and I2P, and restrict to specific ports.
Preventing the malware from reaching its call-home server via the network can disarm an active ransomware variant. As such, blocking connections to I2P or Tor servers via a firewall is an effective measure.
6. Disable remote desktop connections.
Disable remote desktop connections if they are not required in your environment, so that malicious authors cannot access your machine remotely.
7. Block binaries running from %APPDATA% and %TEMP% paths.
Most of the ransomware files are dropped and executed from these locations, so blocking execution would prevent the ransomware from running.
Tamas Feher
Hello, why doesn’t Microsoft disable the /all/quiet deletion method of Shadow Copies with an extra-ordinary Windows patch?
Pierre
That would be a good prevent!
As we can only restore files with our Sprotect backup…
Anonymous
cuz they want us to store Our data on cloud (a.k.a own all Our private data)
Renato
If the following is true “For every file encryption, CryptoWall 3.0 first copies the same file with an additional random character, encrypts the file content and writes it back, before deleting the original file.”, is it possible to recover original deleted files using Recuva or similar programs?
Muhammed Shahzad
I was ready to pay the ransom but first wanted to check if the two free files would decrypt. But it didnt work. I was attacked almost 9 months ago. You guys think there is a time limit after which they shut down the entire trace path so they cant get tracked? I dont want to pay ransom and find out that nobody is going to send me the decryption.
Andrew Poole
Hi Muhammed,
I work in the IT industry and have had several of my clients get hit by this. Fortunately, most of them have a backup of all of their systems that I manage so I can usually just restore the files to right before the infection hit and then have very minimal data loss. Unfortunately, if you don’t have a backup, you only have 2 options. You can either format your system and reload it – starting from scratch, or you can pay the ransom. I will tell you that I have had some of my clients actually pay the ransom and then the files were unlocked. However, variation of this Ransom Ware that I’ve seen has required payment within 7 days or the files are locked forever. Depending on your variation of the virus, you may or not because to unlock the files. There’s really no sure-shot way to answer your question. All you can do now is make an educated guess based on the information I’ve provided. My advice for you would be to cut your losses and not pay the ransom. My best guess is that after 9 months your “token” has expired and if you pay the ransom, there very well may not be anybody on the other side. Good luck, I hope this has helped.
Thanks,
Andrew
JD Payne
How does vssadmin.exe run if the user that was infected doesnt have admin rights and is restricted by GPO from installing anything. i tried to run vssadmin manually form one of these computers and it would not execute without admin credz. Alas, one share in my organization got hammered by this but NONE of the client desktops? any ideas?
Andrew Poole
Hi JD Payne,
Is it possible that someone within the organization had a personal computer with a mapped network drive to the effected share? I’m sure that if someone in your organization obtained the virus on a work PC then you would have heard of it because of personal documents or files being locked.
JD Payne
Ive checked with the guy who usually does their IT support and he says highly unlikely. the share is protected by NT authentication and they would have no way to add the device to the network. Really, its a small office and only one guy brings in a laptop but he only has access to the guest wifi and cant get on the internal network. Fortunately none of the affected files were important. But i really would love to figure out how it happened so we can avoid it in the future. Their IT guy is coordinating now with Sophos to install Cloud Endpoint and UTM so hopefully that will help. They were previously only using the standard Microsoft stuff. But it has served them well, until now. Also, we tried to restore files and got about 300K+ but none were the attacked files.
STG
Hey there. Is it possible for someone to install ransomware on my machine if they get access to my home network? Or if I am on a shared public network? Thanks.
Paul Ducklin
If they can logon *to your computer*, then they can pretty much install or run any software (and read, write or delete any file) that you can. In that case, the clear answer is, “Yes.”
If all they can do is get onto the same network as you, whether that’s at home or at the coffee shop, the answer is, “It depends,” and the question really boils down to, “How safe is my own computer against any sort of hack or intrusion from the network.” You can boost your resistance against across-the-network hacks in a number of ways, such as:
Install an active (on-access, a.k.a. real time) virus blocker and keep it up to date. This helps prevent untrusted programs from sneaking in.
Install operating system and application patches promptly to close known security holes. Crooks can scan automatically for unpatched and vulnerable computers.
Turn on your operating system’s firewall and block incoming connection requests. This adds an extra shield against probes and attempted hacks.
On your home network, turn off Universal Plug-and-Play (UPnP) in your home router. This “feature” is designed to make connectivity from outside easier, and therefore comes rather obvious risks.
Consider using a Virtual Private Network (VPN) when you are connecting over public networks. This shields your traffic from eavesdropping in an untrusted environment.
For a jargon-free explanation of VPNs:
https://blogs.sophos.com/what-is/a-vpn/
For a free VPN you can set up at home to use while you are out and about (some technical skills required):
https://secure2.sophos.com/en-us/products/free-tools/sophos-utm-home-edition/download.aspx
HtH.
Anonymous
Hi! I got infected by Cryptowall. Is it possible, that after the infection even though a file is not encrypted and doesn’t seem infected, it still is? Just because I see a lot of files that are already unaccessible due the encryption, their extension is already modified, but some files seem untouched. Or at least are still accessible and are not yet encrypted. As I understood from the things I read about this ransom, the encrypted files are not infectious, only there is program that runs in the background and scans all the files on all drives, makes a copy of them, encrypts the copy and deletes the originals with the shadow files etc. But this one thing I asked is still not clear.
senthil
hi i got infected with crpyt ransomeware and my files was been encrpyted to decrpt they asked 1.2 bit coins (500$) so i have made payment to them via bitcoins even after payment i didnt see link to download decrypt tool, is there any other way to get the decryptor.
araykha
if your files became .ccc or .vvv extension, i can help you to restore them.
jon guenther
is it possible for it to invade thru a dormant (not activie) ftp port?