
There’s now yet more mystery in the recent TalkTalk “breach” case.
TalkTalk is a UK communications company that admitted, about a week ago, that its website had suffered a “significant and sustained cyber attack.”
Unfortunately, if all you know is that Something Bad Happened, it’s often very hard to pin down exactly what that Something was.
Did the attackers want only to knock you off the air?
If so, was it revenge for a perceived grievance?
Was it to soften you up for blackmail, where the crooks contact you and say, “Pay protection money, or next time will be worse?”
Was it a smokescreen for other criminal activity, with a Denial of Service (DoS) attack used to divert attention from a more targeted break-in?
Or was it maybe, just maybe, to give the attackers some disturbingly perverse fun – “for the lulz,” as they say?
The arrests so far
On Monday this week, UK police announced that a suspect in the attack had been arrested: a 15-year-old boy from Northern Ireland.
Now, according to the BBC, a 16-year-old male from London is the second suspect to have his collar felt.
Both suspects are now out on bail. (We can’t tell you who they are on account of their ages.)
What happened?
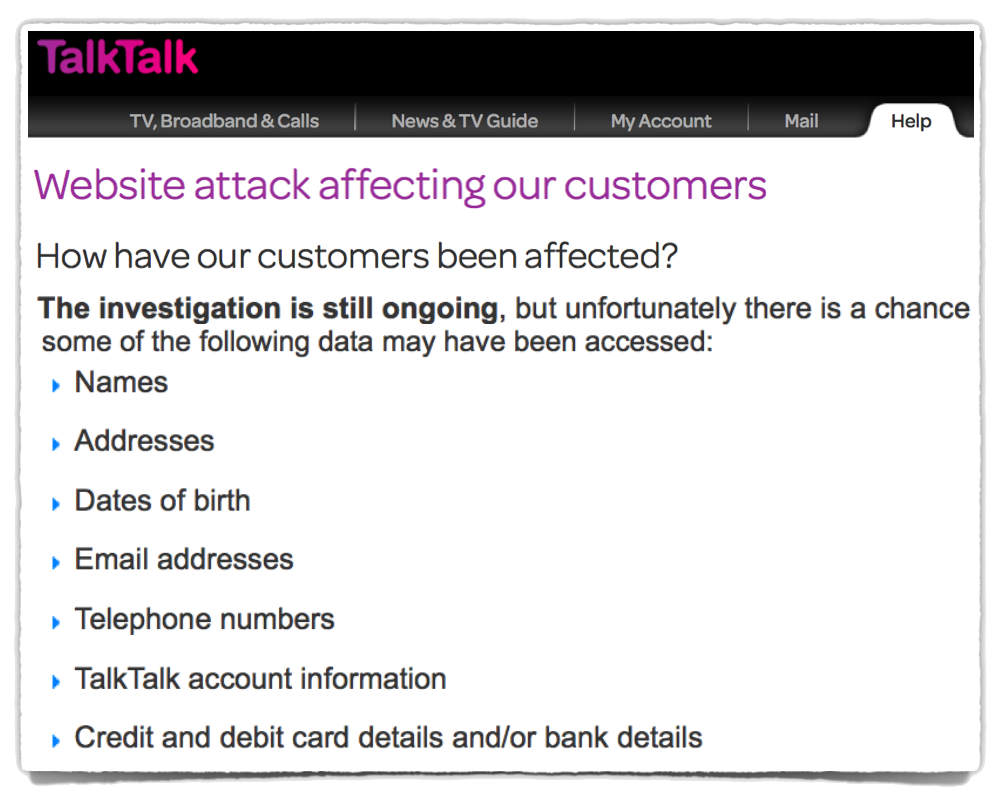
TalkTalk’s website confirms that the company is still [2015-10-30T12:00Z] trying “to establish exactly what happened and whether any of your individual information has been accessed.”
So it’s possible that this attack, even though it has already widely been reported as a breach, might turn out to be no such thing, with no personal information accessed illegally at all.
But there is also a chance, as TalkTalk is openly admitting, that:
Some of the following data may have been accessed: * Names * Addresses * Dates of birth * Email addresses * Telephone numbers * TalkTalk account information * Credit and debit card details and/or bank details
TalkTalk says that credit or debit card numbers were stored with six of their 16 digits blocked out, which makes the data as good as useless to crooks.
But the company isn’t saying how it stores your bank details, if you provided them, although it did tell a reporter at The Register that it doesn’t bother with encryption.
Encryption alone might not have helped on this case, for example if data was stolen by interrogating an insecure database server that was set up to be able to decrypt that data on demand.
But the complete absence of encryption, whether allowable from a legalistic point of view or not, represents what one Naked Security commenter called “a pattern of disinterest in securing entry points.”
What next?
It’s tempting to assume, given that the arrests so far are of under-age youngsters, that this will end up being a case of “we did it for the lulz” rather than “we were after the money.”
But numerous youngsters were snared recently in the UK on suspicion of buying Denial of Service (DoS) tools online using Bitcoin.
They allegedly went on to attack a leading national newspaper, a school, gaming companies and a number of online retailers.
That certainly sounds a like a lot more than “for the lulz”…
…but even it it were, it’s far away from amusing.

John
The pastebin examples, if genuine, show bank details in plaintext, but with the actual account number supposedly redacted by the hacker, sortcodes etc though are shown.
Stoat
The Pastebin examples are just that – examples.
It’s highly likely that much more data was taken than TT is admitting (their systems are fundamentally insecure, as anyone who’s had to deal with the call centres should have realised by now)
It’s also highly likely that the UK arrests are mules and the brains behind the outfit is elsewhere.
Anyone whose data has been compromised in the TT hack has a legal right of redress against the company (right of private action is enshrined in the DPA) and a recent Appeal Court decision allows claims for distress as well as actual monetary loss.
TT may be facing ICO fines, but those are chickenfeed compared to its potential liabilities if enough individuals file claims. The potential for a death of 1,000,000 paper cuts should be enough to make any company sit up and take notice when it comes to data protection, but it will probably take a very public death for this to actually occur.
TT’s public statements have been worded in such a way as to make most people think they haven’t got a hope of winning an action (the infamous “No legal requirements” release, etc), but this is a very risky bluff which has probably resulted in even more attention being given by the regulators.