 The Gameover Zeus and Shylock botnets were destroyed by law enforcement takedowns last year, in two of the most successful actions against financial malware. And yet malware families like Dridex, Dyreza and Vawtrak continue to prey on users of online banking around the world.
The Gameover Zeus and Shylock botnets were destroyed by law enforcement takedowns last year, in two of the most successful actions against financial malware. And yet malware families like Dridex, Dyreza and Vawtrak continue to prey on users of online banking around the world.
Clearly, the fight against cyberthreats isn’t easy, but SophosLabs is developing technologies that improve our ability to understand and respond to threats more efficiently and effectively.
SophosLabs Senior Threat Researcher James Wyke, in a new research paper presented at the Virus Bulletin International Conference, gives us a behind-the-scenes look at an automated system for extracting valuable information from banking malware families.
As James explains in his paper, titled Breaking the Bank(er): Automated Configuration Data Extraction from Banking Malware, data extraction is a time-consuming and repetitive task that is better left to systems, freeing up analysts to concentrate on the hard part of analysis.
Automated data extraction also helps us learn information about malware families and malware authors that we can use to detect future variants and build more robust protection.
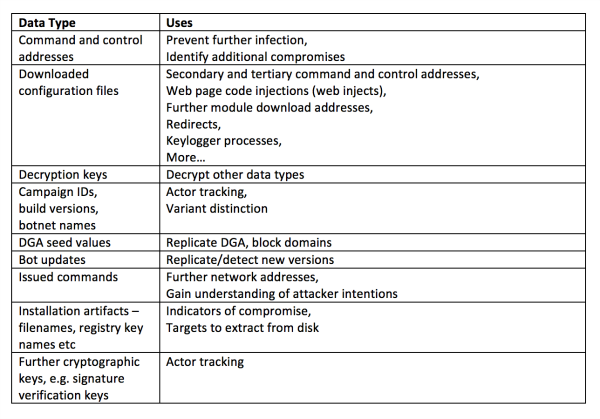
The data extracted from malware can be used in multiple ways, which are described in James’s table below.
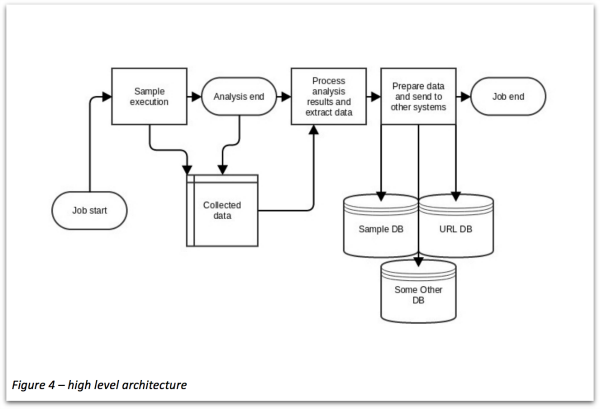
James describes our automated system, built on a sandboxing program called Cuckoo, and how it extracts and processes data before sending it on to other systems for analysis (see figure below).
James goes on to describe how this sandbox system was developed and how it works, and gives us examples of how it’s used to extract data from samples of Vawtrak – a banking malware family James has studied extensively.
While a lot of valuable security research describes how malware is developed from the attacker’s side, James’s paper provides a lot of insight into how our security researchers do their jobs to better protect us from threats.
It’s well worth a read.