
Apple iOS 9 is out.
As usual when the left-most number changes, as here from version 8 to version 9, the download is bigger than your typical point release.
For example, when we recently updated to 8.4.1, the download was about 50MB; this time, the over-the-air (OTA) update we were offered was 1.2GB.
→ Because it’s a left-most-number update, this time we used the IPSW route, which involves downloading the full firmware image from Apple and installing it via iTunes. That way, we’ve got the firmware handy for reinstalls. We’re not going to give a how-to here, but the IPSW download is just a shade over 2GB. IPSW, as you may have guessed, comes from .ipsw, Apple’s file extension for iPhone/iPad software.
As usual, Apple’s landing page for the new release is gorgeously laid out, and filled with glowing positive comparatives: faster performance, even more productive, even more helpful (that’s Siri they’re talking about), longer battery life…
…and, most important of all from our point of view, tighter security.
That’s the reason we did the early adopter thing and updated manually without waiting for our turn in the OTA queue, which Apple typically stretches over several days to spread the load on its content delivery network.
New security features
We’ve already written about some of the changes and new features that are part of iOS 9’s tighter security:
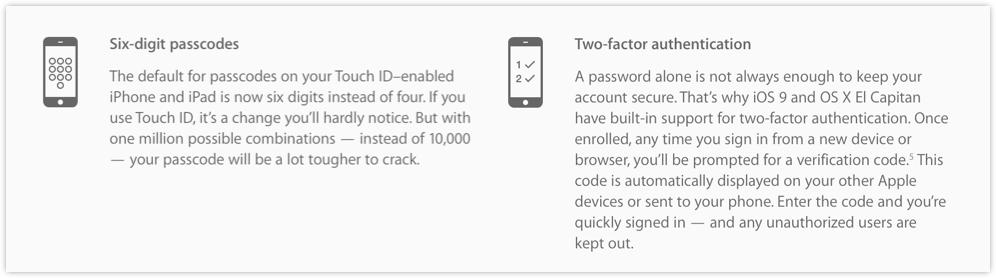
- Default passcodes bumped from 4 digit to 6 digit PINs
- Built-in two-factor authentication (2FA).
- Changes to stop unscrupulous app vendors from finding out which competing products you are using to bombard you with crossgrade ads.
- A feature allowing extensions for mobile Safari that can do ad-blocking.
Apple itself has called out the first two of these on its own iOS 9 landing page:
Going to a 6-digit PIN doesn’t sound like much, but if you’re the sort of user who has been happy with a 4-digit PIN (we know Naked Security readers live at higher security standards – that’s only hypothetical!), the change will do no harm.
You can’t really moan at Apple for suddenly making your lock code too hard, yet a passcode 50% longer than your previous one (6 digits instead of 4) is 10,000% stronger.
→ The PIN code goes from 4 to 6 digits. Because 6 = 4 x 1.5, and 1.5 = 150%, that’s an increase of 50%. The number of combinations goes from 10,000 (104) to 1,000,000 (106). That’s 100 times as many choices, and 100 = 10,000%.
So the PIN code change is a gentle nudge in the right direction for the happy-go-lucky amongst us.
The 2FA feature is a great idea, but it’s probably a bit early for Apple to be talking about it in the present tense.
Firstly, it’s only available if every device where you use your Apple ID supports the feature, so if you are an Apple fan and have a Mac to go with your iDevice, you’re out of luck.
2FA on your Mac needs El Capitan (OS X 10.11), which isn’t available in public release yet.
Secondly, “other criteria will also be used to determine availability,” meaning that the rollout will be gradual.
Apparently, if you don’t get offered it during the post-update setup process (we weren’t), you aren’t on the list yet.
The important parts
But the really important parts of the tighter security are the ones that are as good as invisible unless you visit Apple’s HT201222 Security Updates page.
Annoyingly, when we wrote this [2015-09-17T11:00Z], that page still didn’t have product links more recent than 20 August 2015, so you need to know that the iOS 9 patches are at HT205212.
As usual, there are all sorts of vulnerabilities that have been patched, including:
- Remote Code Execution. At least 30 separate potentially exploitable memory corruption bugs in WebKit and the JavaScript core.
- Information leakage. Access to kernel memory and memory layout from a regular app.
- Security bypass. Reset the “failed password attempts” counter to prolong passcode guessing.
- Denial of Service. Deliberately disrupt network connections belonging to other apps.
- Phishing. Send a bogus email that appears to come from a contact in the address book.
- Sniffing. Eavesdrop on TLS (secure) connections due to a certificate handling bug.
- Spoofing. Make a bogus website show up with the URL of a legitimate one.
Our favourite bug patched in the iOS 9 update was this one, nestled quietly amongst the 67 entries in the HT205212 security bug-fix list:
CoreCrypto Impact: An attacker may be able to determine a private key Description: By observing many signing or decryption attempts, an attacker may have been able to determine the RSA private key. This issue was addressed using improved encryption algorithms.
“Improved algorithms,” indeed!
Update early, update often
As usual, we recommend updating as soon as you can, for the fixes much more than the features.
And when you do the update, take the opportunity to review your security settings in general.
For example, we made sure that location services were turned off, as we wanted; and that the auto-sync features of iCloud were disabled, especially the one that pushed photos and screenshots to the cloud automatically.
Those may not be your preferences, of course, but do take the opportunity to check that your settings reflect your choices, and that you don’t finish the update with a bunch of unwanted security changes.
For advice on where to start when you review your phone’s security settings, please take a look at our popular article, Privacy and Security on Your Phone.
– Phone v. Phone courtesy of Shutterstock –

Anonymous
If you’re reading this and are still somehow happy with a 4-digit PIN, all you have to do to make it a 6-digit PIN is think of a favorite 2-digit number and add it to the start or end (or heck, the middle) of your 4-digit PIN. Not as big a problem as you might think.
Anonymous
Just don’t – please! – use your birthday. Nor any other date people are likely to know about you. Not even if you “encrypt” it as MMDDYY, YYMMDD and so on. A crook with 10 guesses is surely going to try a birthday-related passcode as one of them…
Andrew Ludgate
Also please don’t use the following PINs:
123456
111111
222222 (you get the idea)
However, padding a 4-digit pin that’s fairly easy to guess with unique start and end digits is actually pretty secure as things go.
Gavin
It always bugs me that Bluetooth is automatically re-enabled after every big update. What’s up with that? But to give Apple its due, very little else seems to change across major upgrades.
But yes, it is excellent advice to go through the phone and make sure everything is locked down per your wishes once the upgrade is complete. The new features and apps generally start out totally open (which is understandable), but it only takes a moment to deny them location services, add them to restrictions and so on.
One final note, you don’t have to put in your Apple ID to get through the setup screens. After pressing “I forgot my ID” there’s an option to “Set it up later” (or not at all).
Great article as always!
Gavin
Paul Ducklin
Ha! Great to know about that “I forgot my ID” trick. I was worried that if I went down that path I’d be in a rabbit hole where I was forced into a reset that I didn’t want to do.
My Bluetooth was back on, too. I wasn’t sure if that was a finger-fumble on my part or “just because.” Sounds like it is “just because,” and I consider that plain wrong if so. I also decry the way that Apple (the other vendors do it to) tries so hard to get you to turn location services on, as though you must have made a mistake by turning them off before.
MossyRock
Every time I’ve ever applied an iOS update on my iPad, my Bluetooth gets turned back on. I have no idea why Apple insists on doing this. Just leave the setting as it was.
tartanrose
Thankyou for your information on this update………As always explains all I need to know.
I did the update on my iPad late last night…..,.took quite a while BUT so happy with the end results.
I have been operating with a six digit pin for a long time so no worries there. but it feels good to know there are more secure features onboard now!
it’s beautifully laid out and I love the new keyboard. For some reason the layout makes my screen look bigger! Today new hints have been released on the iPad which helps with oldies like me!
Have a lovely day…….and………….Thankyou
MossyRock
Not security-related, but it appears now, with iOS 9, that Apple is forcing you to use iCloud Drive instead of the legacy iCloud storage for iWork documents (Numbers, Pages, etc.) stored in their cloud.
When you try to open a cloud document or spreadsheet the iCloud option now points to iCloud Drive, not their legacy iCloud.
I can’t access any of my Numbers spreadsheets. Now I have to migrate everything over to iCloud Drive to see if this fixes the problem.
Evolutionary change is a fact of life and is expected, but I’m not ok with a functional change like this with no warning. Thank goodness I caught this before I updated all of our employees’ iPads who rely on Numbers.