In the early 1990s, there simply weren’t that many viruses, and there weren’t that many known ways they worked.
And, on IBM PCs, with less than 640KB to work with (because, as Bill Gates probably never actually said, “640KB ought to be enough for anybody”), there weren’t that many places viruses could hide.
In an emergency, IT support staff could usefully go looking for malware by hand, if only they knew where to look – something a malware description could help with.
Describing what 1990s malware might do was usually a lot easier than it is today, because viruses almost always spread in a self-contained fashion, so they could work without a network connection.
Once you got hold of a sample of the virus, you probably had all you needed to decompile it entirely.
That wasn’t necessarily easy, but at least it was possible, which isn’t the case with a lot of malware today.
These days, a lot of malware only grabs its “damage routines” at the last moment, so they can be changed at will by the crooks who are in control.
Additionally most zombie malware includes functions for self-updating, as well as for downloading additional, as-yet-unknown malware.
So you often can’t predict exactly how an infected computer might behave.
Anyway, that wasn’t the case in the early 1990s, so a group of malware researchers tried to come up with a standardised, if stilted, way of denoting the characteristics of the most common viruses of the day.
And, by way of contributing to #SophosRetroWeek, here’s what a malware description from that era looked like, courtesy of Yours Truly.
By the way, in case you’re wondering why Tequila avoided infecting filenames that contained either “SC” or “V” (see below)…
…it’s because that was a quick-and-dirty way to spot many security programs, such as SCAN from McAfee and VACCINE from Sophos.
Security programs often included self-verification code to check if they’d been tampered with.
So a virus writer either had to figure out how to bypass the self-checking part when infecting tamper-resistant files, or to avoid them in the first place.
I never found out what the initial “T” stood for in the author’s name, but for some reason I have always thought of them as Trevor Tequila.
Here’s the overview of his magnum opus:
| TEQUILA VIRUS | |
| Class: | EXE infector Master Boot Record infector |
| Length: | 3 Kilobytes (2468 bytes added to files) |
| OS: | MS-DOS |
| Are-you-there (memory): | INT 21h/AX=FE02h -> AX=01FDh |
| Are-you-there (disk): | FILE[12h..13h] (EXE checksum) has 1 of 32 possible values |
| Infection trigger: | FindFirstFCB FindNextFCB |
| Infection criteria: | Filetype = EXE EXEloadSize == EXEfileSize “SC” not in filename “V” not in filename |
| Interrupts hooked: | INT 13h (sector-level disk I/O) INT 1Ch (timer tick) INT 21h/AH=11h (find first file) INT 21h/AH=12h (find next file) INT 21h/AH=FE02h (are-you-there) INT 21h/AH=FE03h (display message) |
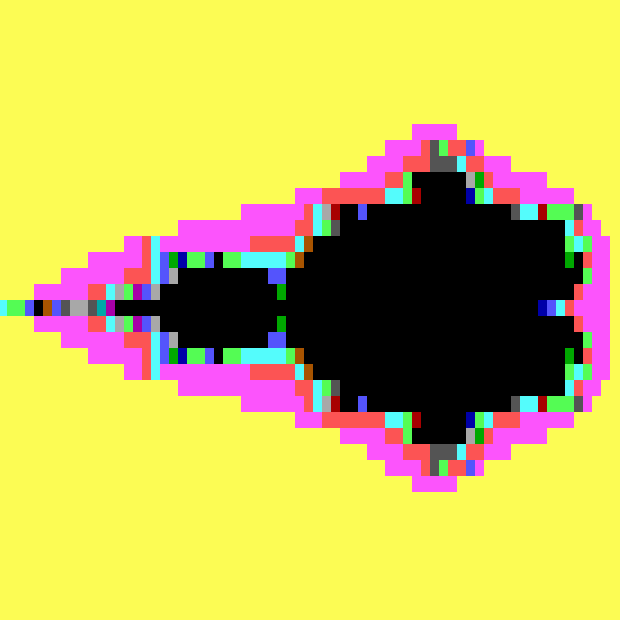
| Damage: | Low-res fractal displayed on screen Text message from author displayed |
| Damage trigger: | Infected program run on same day of month as when infection occurred, 3 or more months later. |
| OUTPUT |
Execute: mov ax, FE03 / int 21. Key to go on! Welcome to T.TEQUILA's latest production. Contact T.TEQUILA/P.o.Box 543/6312 St'hausen/Switzerland Loving thoughts to L.I.N.D.A BEER and TEQUILA forever ! |
| NOTES BY ANALYST (PAUL DUCKLIN) |
|
Tequila might be described as action-packed for the anti-virus researcher. It’s got plenty of “features”. Tequila has mild armouring: the decryption code is also the decryption key. Setting a breakpoint outside the decryptor fails because the breakpoint instruction gets altered; setting one inside the decryptor before control is returned to the decrypted code causes errors in the decryption. It’s bipartite, infecting the MBR and .EXE files. It uses tracing to find the INT 13h entry point; it has stealth, to hide both the infected partition record and the increase in size of infected .EXEs; it is polymorphic when infecting files (though not polymorphic in the MBR). One of its damage routines is to compute and display a low-resolution fractal. The fractal display is enabled when an infected program is run more than three months after it was infected and on the same day of the month as it was hit. Three programs later, the fractal appears on program termination. Files with “SC” or “V” in their name are left alone; files treated with a certain integrity self-checkroutine (apparently) have the self-check trashed. When infecting the MBR, Tequila searches the MBR partition table for the first DOS partition. The size of this partition is shrunk by 6 sectors, and these 6 sectors are used as a hiding place by thevirus. Anything previouly in those sectors is lost forever. Tequila marks the timestamp of infected files with a value of 62 in the seconds field. This is used by its stealth routines to decide, during directory searches with FindFirstFCB and FindNextFCB, when to subtract 2468 bytes from the reported file size. No stealthing of actual file access is performed, however. Anything else? Ah yes – the virus even provides an interrupt call which will instruct it to describe itself. Issuing INT 21h, AX=FF03h will produce the “T.TEQUILA” message above. The author or authors must have been relatively young. *No-one* can drink Beer and Tequila forever! |