– Image from the research paper below –
We’ve written about unintentional information disclosure thanks both to stray sounds and to power usage.
Now it’s time to crack cryptographic codes electromagnetically.
A team of Israeli security researchers at Tel Aviv University have developed a novel way to steal encryption keys using a cheap radio sniffer and a piece of pita bread.
While the risk posed by the tempting snack is nothing new, the cost and size of the required equipment is significantly smaller than that of the previously required laboratory equipment.
Instead of thousands of pounds and a large room, a would-be pita bread hacker would probably get enough change from a hundred pounds to pop out and buy a whole pack of unleavened bread and a lunchbox to store everything in.
When fully assembled, the device works by listening to radio signals emitted by a computer’s CPU when it’s crunching data.
Researchers Daniel Genkin, Lev Pachmanov, Itamar Pipman and Eran Tromer discovered that a range of operations emitted differing radio frequencies, allowing them to determine when the various laptops they tested were idle, playing a game or decrypting data.
By monitoring the signals given off when the machine was decrypting an email message, through signal processing and cryptanalysis, the researchers were able to deduce the encryption key being used.
Pita
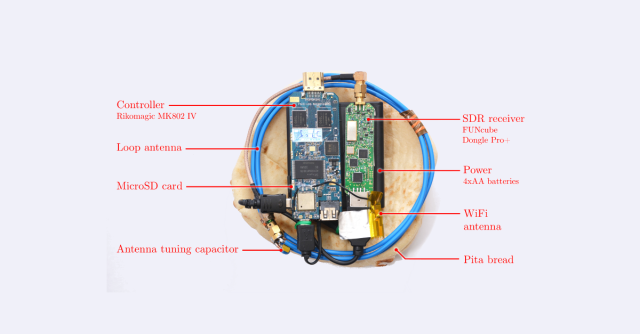
After proving the attack worked under laboratory conditions, the researchers rolled out a mobile version using a FUNcube Dongle Pro+ software-defined radio, an Android-based Rikomagic mini-computer to control the dongle and an AM radio antenna.
Dubbing the machine Portable Instrument for Trace Acquisition (PITA), I guess they really had dough choice about what to conceal it in.
– Image from the research paper –
The researchers said:
The setup is compact and can operate untethered; it can be easily concealed, eg, inside pita bread. Common laptops, and popular implementations of RSA and ElGamal encryptions, are vulnerable to this attack, including those that implement the decryption using modern exponentiation algorithms such as sliding-window, or even its side-channel resistant variant, fixed-window (m-ary) exponentiation.
Operating at a frequency of 1.7Mhz, the antenna picks up signals leaked from the computer and records them onto an internal microSD card. When back into the hands of the researchers (or retrieved via Wi-Fi), those signals could, they said, be analysed in a matter of seconds:
We successfully extracted keys from laptops of various models running GnuPG (popular open source encryption software, implementing the OpenPGP standard), within a few seconds. The attack sends a few carefully-crafted ciphertexts, and when these are decrypted by the target computer, they trigger the occurrence of specially-structured values inside the decryption software. These special values cause observable fluctuations in the electromagnetic field surrounding the laptop, in a way that depends on the pattern of key bits (specifically, the key-bits window in the exponentiation routine).
Mixed results
The researchers also tried to replicate their results using smartphones and consumer-grade radio receivers. They noted mixed results, discovering that the best match up came from using a consumer radio called “Road Master” connected to the microphone jack of an HTC EVO 4G smartphone, sampling at 48 kHz.
They noted, however, that the range of all the mobile devices they tested was limited to around 50cm unless better amplifiers, antennas and digitisers were used.
So, for now at yeast, remote pita bread attacks seem unlikely.
At closer range, however, the chances of mitigating this type of hack are far slimmer, according to the researchers.
They suggested one solution was to put a vulnerable device inside a Faraday cage – which hardly sounds like an ideal solution. The researchers added that:
Inexpensive protection of consumer-grade PCs appears difficult.
The only other countermeasure put forward by the research team revolves around the cryptography itself:
Alternatively, the cryptographic software can be changed, and algorithmic techniques employed to render the emanations less useful to the attacker. These techniques ensure that the rough-scale behavior of the algorithm is independent of the inputs it receives; they usually carry some performance penalty, but are often used in any case to thwart other side-channel attacks.
But with this type of attack being more theoretical than practical, I suspect we won’t be seeing appropriate security measures baked in any time soon.
The researchers plan to demonstrate their work at the Workshop on Cryptographic Hardware and Embedded Systems conference in September 2015.