 United Airlines is offering up to 1 million free air miles in a new bug bounty program that rewards hackers who discover security flaws in the airline’s websites, apps and databases.
United Airlines is offering up to 1 million free air miles in a new bug bounty program that rewards hackers who discover security flaws in the airline’s websites, apps and databases.
The program is the “first of its kind within the airline industry,” United proclaims on its website.
Bug bounties, which reward security researchers for responsible disclosure of vulnerabilities, are offered by many tech companies such as Facebook, Google and Microsoft.
The bounties usually come in the form of cash: Google even offers up to “infinity dollars” in its program, although most bounties are far less.
United’s bug bounty program, however, offers rewards in the form of air miles – ranging from 50,000 free miles for low-level bugs (cross-site request forgery, bugs in third party software affecting United), to 1 million miles for the highest level kind of bug – remote code execution.
To qualify for a reward, hackers need to be signed up as members of the airline’s MileagePlus reward program – and they need to comply with a strict set of eligibility rules.
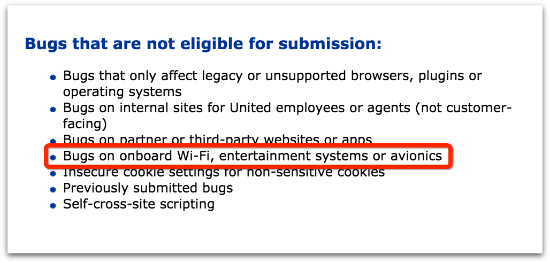
Some security flaws that aren’t permissible include tampering with aircraft systems such as in-flight Wi-Fi or entertainment.
 Hackers could end up in a heap of trouble for trying certain types of attacks, United warns, resulting “possible criminal and/or legal investigation.”
Hackers could end up in a heap of trouble for trying certain types of attacks, United warns, resulting “possible criminal and/or legal investigation.”
Do not attempt:
Attempting any of the following will result in permanent disqualification from the bug bounty program and possible criminal and/or legal investigation.
* Brute-force attacks
* Code injection on live systems
* Disruption or denial-of-service attacks
* The compromise or testing of MileagePlus accounts that are not your own
* Any testing on aircraft or aircraft systems such as inflight entertainment or inflight Wi-Fi
* Any threats, attempts at coercion or extortion of United employees, Star Alliance member airline employees, other partner airline employees, or customers
* Physical attacks against United employees, Star Alliance member airline employees, other partner airline employees, or customers
* Vulnerability scans or automated scans on United servers
Maybe United has had this in the works for a while, but the announcement of the bug bounty program comes just a few weeks after the airline banned a security researcher from flying on United after he tweeted that he could hack onboard systems to deploy oxygen masks.
United cited its existing policies in banning the researcher, Chris Roberts, and preventing him from boarding his United flight from Colorado to San Francisco (where he was scheduled to speak at the RSA Conference about security vulnerabilities in transportation).
Recently, US government agencies have launched investigations into the security of systems such as avionics (onboard computers that control communication and navigation), and the antiquated air traffic control system that directs millions of flights annually across the US.
The findings of a US Government Accountability Office (GAO) report has raised the level of scrutiny on airlines by lawmakers, regulators, the media and general public.
Despite all of this attention on aircraft security, and presumably for reasons of aircraft safety, the United bug bounty program is limited to the security of its websites.
United, who has previously struggled to keep customer data secure, is stepping up its website security in other ways, too – just last week the airline announced the beta launch of a brand new united.com.
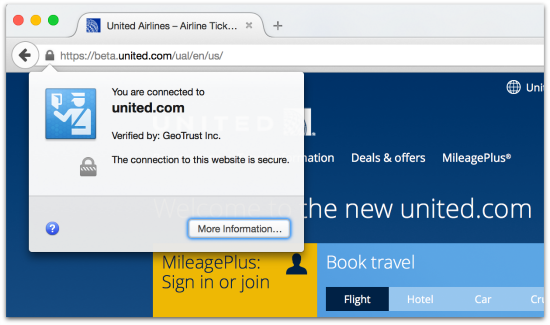
While United is touting upgrades to its website design like easier search and filtering of flight information, one unsung feature is the switch to default SSL encryption across the entire website (shown by the “HTTPS” part of the web address).
You can see on the homepage of the beta.united.com site that it has a security certificate telling you that this is really United’s website, as vouched for by the certificate authority GeoTrust.
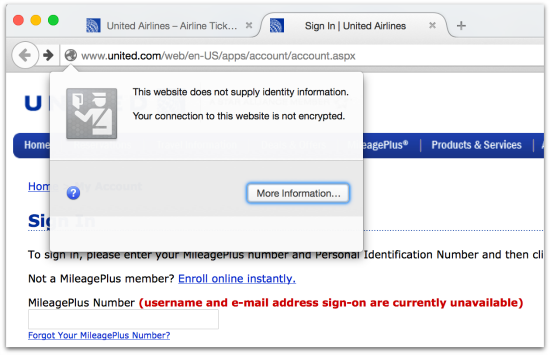
The current united.com website doesn’t have that extra layer of security.
Let’s hope the other airlines follow United in taking proactive steps to protect customer data.
Image of plane over New York courtesy of Shutterstock.com
