Thanks to Anand Ajjan of SophosLabs for the behind-the-scenes research that was the basis for this article.
 An aggressive new ransomware called TeslaCrypt is targeting Windows users, and it breaks new ground by expanding on a familiar yet successful formula.
An aggressive new ransomware called TeslaCrypt is targeting Windows users, and it breaks new ground by expanding on a familiar yet successful formula.
As you may already know, ransomware is about the bluntest sort of malicious software you are likely to experience.
Ransomware shoves itself unavoidably right in your face.
It deliberately locks you out of your computer or your files, and then demands money to let you back in.
TeslaCrypt, first detected by SophosLabs in January 2015, goes for your files, much like CryptoLocker and CryptoWall, but it holds even more types of file to ransom.
Just like CryptoLocker and CryptoWall, TeslaCrypt seeks out valuable data on your computer by searching for file types such as photos, financial spreadsheets and Office documents.
Yet in an interesting new twist, TeslaCrypt also seeks out files related to dozens of games, including saved games, configurations, maps and replays.
TeslaCrypt targets some well-known games including Call of Duty, World of Warcraft, DayZ, Minecraft, Fallout and Diablo, as well as configuration files for the online gaming platform Steam.
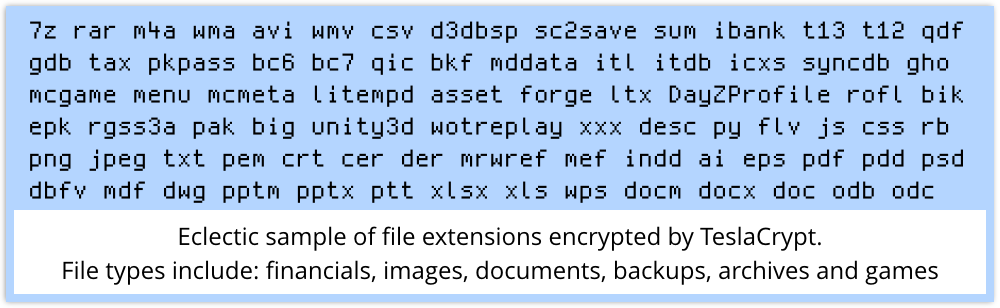
There’s more: TeslaCrypt also seeks out files related to tax returns, personal finance such as Intuit’s Quicken software, and iTunes.
TeslaCrypt can locate files on connected devices and drives and encrypt those too – USB drives, network file shares, cloud storage folders, or other connected storage devices are vulnerable.
TeslaCrypt vs. CryptoLocker
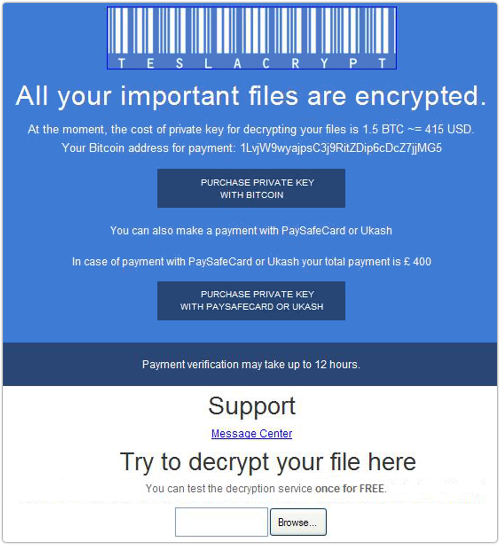
Like recent versions of CryptoWall and other CryptoLocker imitators, TeslaCrypt demands payment in Bitcoins, or by other irreversible and largely anonymous e-payment systems such as Ukash.
The warning screen provides a link to a page on the Tor network which offers further instructions on how to pay.
TeslaCrypt currently charges 1.5 Bitcoins (about US$420 in March 2015), but if you pay in Ukash the price goes up to £400 (about US$600).
Victims are encouraged to upload one file and get it decrypted “for free” – a sort of proof-of-concept intended to convince you that the crooks really do have the decryption key and will follow through on their end of the deal if you pay.
If you have any doubts about how to make your payment, TeslaCrypt helpfully offers a “support” service where you can send a message to the crooks.
Interesingly, when TeslaCrypt runs, it creates a shortcut on the desktop called CryptoLocker.lnk.
But even though the TeslaCrypt authors may be using the familiar CryptoLocker “brand,” that’s where the similarity ends: the new malware doesn’t use the same code as the original CryptoLocker.
Why the ransomware threat is growing
Ransomware isn’t really new – older forms of ransomware that locked up your computer screen rather than your files emerged many years ago.
But file-encrypting ransomware like TeslaCrypt has become a highly successful business model for cybercriminals, making it likely we’ll be seeing many “new and improved” variants.
Although cybercriminals have developed many schemes for making money, from sending spam to stealing passwords and banking information, ransomware offers easy profit.
And it is very profitable.
The US Department of Justice estimates that the original CryptoLocker gang made $27 million in just two months after it first began spreading in September 2013.
Because so many victims of ransomware have proved willing to pay, with one study finding that 40% of CryptoLocker victims paid the ransom, we can count on ransomware continuing to proliferate.
Going after gamers is a devious but savvy move by the TeslaCrypt gang: as a group, gamers are expected to spend more than $111 billion (yes, with a “B”) in 2015.
TeslaCrypt seems like a play for greater windfall profits by expanding the pool of potential victims who’ll be willing to pay to get their files back.
How to stay safe from ransomware
TeslaCrypt arrives via spam, either in malicious email attachments or via links to malicious websites that download the ransomware, so protecting your computers with anti-spam and web filtering software can help to prevent the ransomware messages from getting through.
Before ransomware can do its dirty work, it must contact a command and control server to generate the public-private encryption key pair.
Next-generation firewalls and anti-malware software that can detect suspicious traffic to the command and control server can stop the malware when it connects to attackers’ servers.
If you’ve been a victim of ransomware and don’t want to pay the ransom, there’s not much you can do if you don’t have backups – the RSA encryption used by modern ransomware is too strong to break.
It’s always a good idea to back up your important files, but if you leave your backup drive permanently connected, ransomware might encrypt your backed-up files, too. If possible, disconnect that drive when your backup is complete.
For more advice on preventing ransomware infections, and what to do if you’re a victim, give a listen to Sophos experts Paul Ducklin and Chester Wisniewski discuss “dealing with ransomware” in the podcast below.
(Audio player above not working? Download, or listen on Soundcloud.)
NB. Sophos detects TeslaCrypt proactively as HPmal/EccKrpt-A, using its Host Intrusion Protection System (HIPS).
Find and remove malware with the free Sophos Virus Removal Tool
The free Sophos Virus Removal Tool is a simple tool for Windows users that works alongside your existing anti-virus to find and get rid of any threats lurking on your computer. Download and run it, wait for it to grab the very latest updates from Sophos, and then let it scan through memory and your hard disk. If it finds any threats, you can click a button to clean them up.
Image of blue screen with binary code background courtesy of iunewind / Shutterstock.com.