You’re probably all-too-familiar with “foistware.”
That’s where you decide you like product X, so you download it and install it.
But during the install process, it suddenly recommends other software, and if you aren’t careful, you end up downloading and installing that as well.
One well-known example of foistware is Adobe’s Flash Player installer, which typically urges you to install Intel’s McAfee Security Scan Plus product at the same time:

We’ll take the view for now, just to keep things simple, that an optional offer that is turned on by default can be considered “opt-in.”
We don’t really agree with that, but we’ll go with “opt-in” on the grounds that the installer doesn’t proceed until you have had a chance to review the page and (here’s where the semantics get tricky) opt out of the additional component.
Another well-reported – nay, infamous – “foistware” example from a few years ago was CNET’s bundling of a browser toolbar with the popular network security tool NMAP:
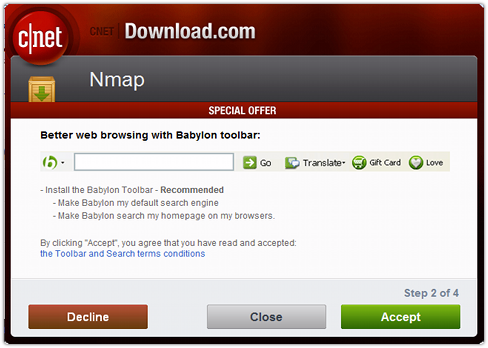
The NMAP case was made worse by the fact that CNET not only implied some sort of agreement between NMAP and the toolbar company, but also implied an agreement between CNET and NMAP to provide a modified NMAP installer in the first place.
(In fact, CNET simply rebundled NMAP because it was free software, albeit not free-for-all.)
As Gordon Lyons, the creator of NMAP, wrote with understandable angst at the time:
The problem is that users often just click through installer screens, trusting that download.com gave them the real installer and knowing that the Nmap project wouldn't put malicious code in our installer. Then the next time the user opens their browser, they find that their computer is hosed with crappy toolbars, Bing searches, Microsoft as their home page, and whatever other shenanigans the software performs! The worst thing is that users will think we (Nmap Project) did this to them!
So the first order of business is to notify the community so that nobody else falls for this scheme. Please help spread the word.
Foistware back in the news
The use of foistware as a product marketing strategy is in the spotlight again, this time thanks to BitTorrent, Inc., makers of the small-and-simple Torrent client uTorrent.
(In this context, u- is read as the Greek letter μ, pronounced “mew” in English, being the scientific abbreviation for “micro-“.)
When we tried the installation, uTorrent tried out two foistware steps.
First, we received a Special Offer for BitTorrent Users, recommending something called a “Five Knives Bundle”:
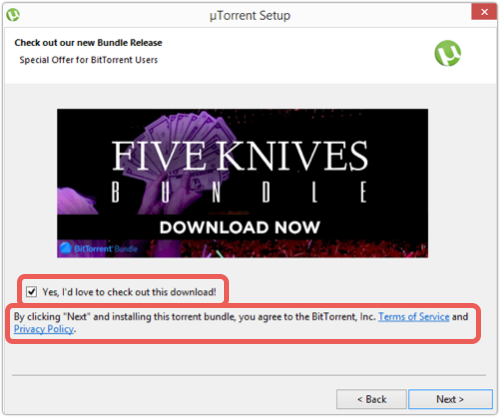
The dialog window was opted-in to the offer, but we were admittedly free to decline the offer before clicking next.
(Jumping ahead slightly, when we did decline the offer, uTorrent installed itself and honoured our request not to receive the Five Knives download.)
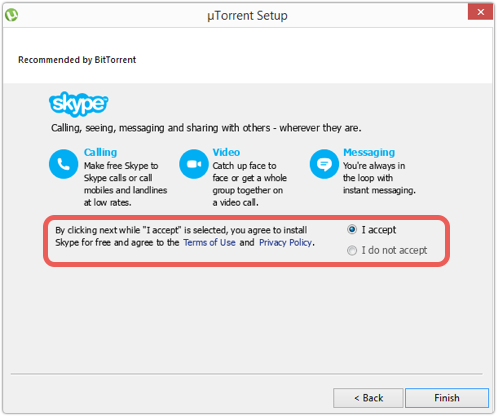
Next came a Recommended by BitTorrent dialog, promoting Microsoft’s Skype software.
There was a note to remind us that just clicking next would automatically install Skype “for free,” though that is perhaps an interesting choice of words considering that Skype is free anyway, and the button is actually labelled [Finish]:
Going ahead with the defaults meant that as soon as uTorrent was installed and running, it started torrenting a 418MB file entitled “Five Knives Savages Bundle”.
And it installed and launched Skype for us, leaving us with a Skype sign-up screen:

The Epic Scale connection
As we have noted above, foistware is not unusual in the software industry in general, nor for uTorrent in particular.
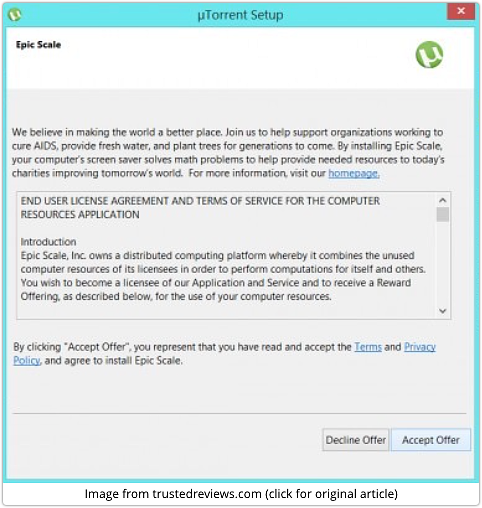
But there was a visible public outcry recently when the second uTorrent foistware dialog – the one that installed Skype in our example above – offered a program called Epic Scale instead:
The problem with Epic Scale is that, for all the charitable intentions it claims on its own website, it is primarily a cryptocurrency mining client.
Apaprently, it goes after Litecoin, rather than the more commonly-used and better-known Bitcoin, but the programming principles are the same.
You throw as much processing power as you can, using your CPU and your graphics card, if you have one, at grinding out cryptographic calculations (SHA-256 hashes, as it happens).
Every now and then, you produce a SHA-256 hash with a certain pattern of bits that means you might just have won a small prize: some cryptocurrency!
Except in this case, you haven’t won the prize: Epic Scale has, although it claims to donate 75% or more of the value of these earnings to charity.
But why the outcry?
How or why is this worse than installing Skype?
On the surface, it’s no different at all.
But the problem is that when cryptocurrency miners like Epic Scale’s run, they really put the digital hammer down, typically consuming more electrical power, and generating much more waste heat, than usual.
Overall, therefore, your computer runs slower, hotter and more expensively than you would expect.
The cost of your “charitable donation” may be more than you first thought.
But it’s OK!
Of course, you opted in, and you can opt out again later by uninstalling the foistware independently.
So it’s not all bad.
But should this be allowed, or should the practice of “foisting” software be prohibited?
The upside is that it allows companies like BitTorrent, Inc. (and, apparently, Adobe) to offer their own software for free, yet still recognise some revenue from affiliated marketing activity.
The downside is that it can backfire on both the foister (e.g. BitTorrent, Inc.) and the foistee (e.g. Epic Scale) if users find the combination unpalatable.
So, as long as the foister and foistee have an agreement for co-operation; as long as the foisting is made obvious; and as long as the foisted software is installed so it can be uninstalled independently, a free-market economy would surely have to agree that foistware is OK.
What to do?
If product X offers you product Y as well, read the small print.
If in doubt, simply decline the foistware: if product X cares for your business, you will not be disadvantaged by declining.
Easy as that!
Image of burning CPU courtesy of Shutterstock.