Looking for an explanation of Superfish? See our article here: Lenovo “Superfish” controversy – what you need to know.
The Lenovo “Superfish” controversy was caused by the revelation that Lenovo, for the last three months of 2014, had shipped adware known as “Superfish” on some of its notebook computers.
The real problem with this software was not so much that it was adware, but that it posed a privacy and security risk.
Briefly put, Superfish:
- Installs a network filter that intercepts all your web traffic, including HTTPS.
- Carries out a so-called Man in The Middle attack to decrypt your HTTPS traffic.
- Installs a Trusted Root Certificate so that the MiTM decryption doesn’t produce any warnings.
Even if Superfish doesn’t deliberately go after any personally identifiable information in your secure transactions, you have to assume that the programmers haven’t made any blunders that might let crooks abuse its privileged position.
That, on its own, is enough of a security concern to justify the immediate removal of Superfish.
But Superfish also makes it easy for crooks to extract the private signing key it uses for its MiTM work, and to abuse that key to sign content of their choice.
Because the Superfish root certificate is authorised to sign both websites and programs, crooks can abuse it not only to trick you into trusting a fake web page, but also to trick you into trusting any software that you download from it.
In short: if you have Superfish installed, you want to get rid of it.
Remove the software
Fortunately, for all that the software is unsafe, it doesn’t seem to be devious, so you can uninstall it conventionally.
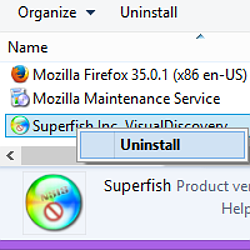
Head to Control Panel | Programs | Programs and Features and look for an entry entitled Superfish Inc. VisualDiscovery.
Right click and choose Uninstall.
Your browsing will no longer be monitored by Superfish’s MiTM filter.
Unfortunately, the Superfish uninstaller does not remove the Trusted Root Certificate it added so that it could masquerade as your bank, webmail server, company network, and so on.
Removing the certificate
To prevent future malware from taking advantage of that certificate, you should remove it.
You need to run the Windows utility called MMC, short for Microsoft Management Console.
An easy way to do this is to use the Run option from the Start menu; type in mmc as the name of the program you want to start:
Go to File | Add/Remove Snap-in... to give yourself access to the certificate management menu:
Choose Certificates and then press [Add>] and [OK] to activate the snap-in you need:
Go back the main MMC console, and click on the triangle next to Certificates in the left-most column to expand the list:
Go to Trusted Root Certificates | Certificates and scroll down until you see the Superfish certificate.
Now right-click and choose Delete:
There’s a final warning that this “might prevent some Windows components from working properly,” but in this case we want to make sure that anything relying on the Superfish certificate won’t work at all:
Click [Yes] and that should be that.
For future reference
For future reference, a good habit to adopt is clicking on the HTTPS padlock in your browser’s address bar whenever you are using a secure site.
Trickery such as that wrought by Superfish’s fake certificate is then much more obvious, because Superfish will show up as the certificate authority that vouched for the site:
If you are familiar with what to expect, the difference is obvious:
Note that if you remove the Superfish root certificate without uninstalling the Superfish software, you’ll nevertheless be safer than you were.
The fake certificates used by the Superfish filter will no longer be trusted, so you will see warnings like this:
We hope this helps!
(For more detail about Superfish, please see our article here: Lenovo “Superfish” controversy – what you need to know.)
Image of fish used in Facebook post courtesy of Shutterstock.