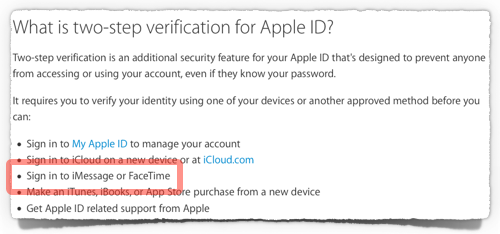
Apple has quietly extended its two-step verification feature to more of its ecosystem.
If you have the “Apple two-step” turned on, then the iMessage and FaceTime services are now protected by it.
Apple provided two-step security for your AppleID back in March 2013, and extended the protection to iCloud in September 2014.
Ironically, extending protection for iCloud was largely precipitated by Apple’s own advice, issued at the time of 2014’s Giant Nude Celebrity Photo Leak Scandal.
Some of the stolen photos in that scandal were almost certainly acquired from iCloud, which led to accusations that iCloud itself had “been hacked.”
It turned out that the problem was almost certainly down to poor iCloud password choices by the victims, which led Apple to urge everyone, “Use two-step verification!”
Which, embarrassingly for Cupertino’s spokespeople, didn’t actually extend to iCloud at that point.
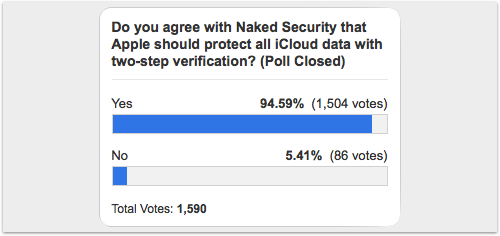
We ran a poll so that Naked Security readers could help us send a message to Apple to correct this oversight:
Good result!
Apple agreed with those readers who agreed with us, and iCloud quickly got “two-stepped.”
So we’re glad to see two-steppification now extended even further.
Isn’t this just 2FA?
Many news stories you’ll see are calling it “two factor authentication” (2FA).
That’s close, or perhaps close enough, but Apple has done the right thing by giving a slightly different name to its own authentication system.
2FA is where you have to come up with two separate things – factors, in fact – when you login, rather than just one.
Most bank accounts that allow ATM (cashpoint) withdrawals, for instance, won’t give you any money unless you can present a card and type in a secret code, or PIN.
That’s a basic form of 2FA, and one of the reasons that you’re told not to write your PIN on the back of the card is that to do so spoils the “two-factor” part.
If someone steals the card, they get both factors at once, so you’ve effectively downgraded yourself to 1FA.
→ Of course, you shouldn’t really write down your PIN anywhere, unless perhaps it’s on a slip of paper you lock in a safety deposit box. But writing it on the card itself would be a double disaster.
How does it work
For computer logins, 2FA usually works in one of three ways:
- You carry around a small hardware “fob” that displays an ever-changing sequence of login codes.
- You receive an SMS on your mobile phone with a one-time login code.
- You run a software program on your mobile phone that works like the hardware fob.
Apple chose the SMS-based approach, although after you have registered a mobile phone number and received at least one SMS, you can also receive login codes via Apple’s Find My iPhone app.
SMS-based authentication comes in for a lot of criticism from a small but vocal minority who don’t have mobile phones, or live in areas of poor coverage.
But for the vast majority that do have mobile phones, it’s surprisingly handy (if German speakers will pardon the inadvertent pun) because you don’t need to carry a special fob for each account.
Every login attempt produces its own SMS, and each SMS contains a code that’s valid only for a short time, say, one minute or until you successfully log in, whichever comes sooner.
So, unlike your password, which a crook can acquire by guessing, by keylogging, by shoulder-surfing, or in numerous other ways, SMS codes work once only, so they can’t be re-used.
The “two-step” shortfall
The reason Apple doesn’t use the terminology 2FA is refreshingly honest.
For at least some Apple users, the “two-step” doesn’t, strictly speaking, rely on two factors.
That’s because, if you have an iPhone or a 3G/LTE-enabled iPad, you probably receive your SMSes on the same device that you’re using to logon in the first place.
So, when the SMS arrives, or the Find My iPhone app pops up, and you type in the code that you just received, it’s vaguely like having your PIN written on your cashpoint card.
In short, there are definitely two steps, and there are definitely two passwords (the one you chose, which remains constant, and the single-use code in the message), but there aren’t necessarily two independent factors.
So why bother?
Is this shortcoming enough of a reason not to bother with the Apple two-step?
No.
- You don’t have to receive the SMSes on the same device as the one on which you’re logging in.
- The SMS or Find My iPhone message still provides extra security if your password is stolen.
- The arrival of an unexpected SMS indicates suspicious activity elsewhere.
In short, if you’re using Apple’s online services, the two-step is probably for you.
Perhaps you don’t have a mobile phone? Perhaps you have unreliable coverage? Perhaps you have a curious service provider who charges you for receiving SMSes? Perhaps you just don’t like giving Apple your phone number?
In that case, ignore our advice – but please don’t rush to your keyboard to tell everyone else that it’s a bad idea, just because it doesn’t work well for you.
Two-step verification is not a silver bullet, but it does make things trickier for the crooks, just like picking a proper password in the first place does.
If you’ve resisted until now, make today the day you reconsider.
It is Friday the Thirteenth, after all!
→ Apple has an FAQ page about its two-step verification. It is written in remarkably plain English, and is refreshingly free from jargon. Even if you don’t have an Apple account, it’s worth reading, just to see how it’s written.