 Need to break the law, but lack the technology chops to do it yourself?
Need to break the law, but lack the technology chops to do it yourself?
Now, as they say, there’s an app for that.
More precisely, there’s a market for it, launched in November, called Hacker’s List.
As of Monday morning, the site was down, either because it was mobbed by every tech journalist on the planet, or because a whole lot of people really, really want to do things like break into their lovers’ Facebook and Gmail accounts to sniff out cheaters.
Massive amounts of new traffics equals rapid server expansion. Please mind our mess.
Prying open a boyfriend’s private accounts is just one of the crimes listed in a Task Rabbit/Craigslist-esque service-for-hire fashion that were spotted by the New York Times.
Besides the California woman who’s willing to pony up $500 to get the dirt on her potentially philandering significant other, some of the other things that people are eager to assign to “professional hackers around the world” in a manner that’s “safe, fast and secure” include breaking into a landlord’s website, changing student grades, damaging people’s reputations… and so the list goes on.
The man who is looking for someone who can break into his landlord’s website said in his post that he’ll pay up to $2000.
Another user who claimed to be living in Australia recently posted that he’d be willing to pay up to $2000 for somebody to pry a list of clients out of a competitor’s database:
I want the client lists from a competitors database. I want to know who their customers are, and how much they are charging them.
Other listings wanted somebody to get a grade changed “ASAP!” – perhaps before parents became aware of the real grade?
One person posted a simple request for somebody to “Distroy credability”:
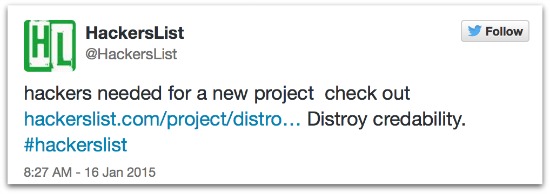
hackers needed for a new project check out http://hackerslist.com/project/distroy-credability ... Distroy credability. #hackerslist
Also posted were requests for an iPhone hack, a “Hack a gmaila account” job, a “whats app list and spy the phone” assignment, and to “Hack database of a central bank”, as well as scrubbing unflattering content off the web.
Are these listings for real? They could well be. It’s certainly not the first such site to offer “hacking” services that cross over into the blatantly illegal.
The NYT spoke to a site that reviews the legitimacy of such services, hackerforhirereview.com.
It gave Hacker’s List a positive review, with the owner of the site saying that he’d rated the site favorably because it’s a “really cool concept” that limits the ability of customers and hackers to take advantage of one another.
It also lowers the bar for entry into online crime, said Thomas G. A. Brown, a senior managing director with FTI Consulting and former chief of the computer and intellectual property crime unit of the United States attorney’s office in Manhattan.
The NYT quotes him:
Hackers for hire can permit nontechnical individuals to launch cyberattacks with a degree of deniability, lowering the barriers to entry for online crime.
As of Friday, the 40 “hackers” who registered on the site to bid for jobs must have been rolling in offers, given that there were 844 registered job posters.
Hacker’s List promises to make the transactions anonymously and offers to hold a customer’s payment in escrow until the task is completed. It’s collecting a fee on each completed job.
While many of the tasks listed on the site are clearly illegal, Hacker’s List claims to be insulated from legal liability, saying that it neither endorses nor condones illegal activities.
It boasts a 10-page terms and conditions section that both hackers and job posters have to sign off on and which plainly states that users shouldn’t use the service “for any illegal purposes.”
Will that impress any judges or juries?
Time will tell. As experts note, much of these types of crimes are so widespread nowadays, it remains to be seen how much prosecutorial muscle will be put to investigating any of the password-cracking, database-breaching shenanigans that the site is set up to enable.
After all, these postings are coming in from all over the world. That’s quite the cross-border law enforcement headache, particularly when you’re talking about what’s small potatoes on a global-crime scale: i.e., the domestic-squabble sort of crime such as breaking into your lover’s social media account or using spyware on his or her phone.
Of course, from an ethics standpoint, none of this is small potatoes at all.
It’s just plain dismaying that spying on others, ruining their credibility, gaining unfair competitive advantage and even cracking a bank’s database could be so casually listed, as if any one of them were postings for a lost cat or a request for help in cleaning out the basement.
This is one of the few times when I’ve wished for a news story to turn out to be a prank.
Unfortunately, given even the briefest scan of Naked Security headlines concerning spyware or data breaches, it very likely is quite real.
Image of hackers courtesy of Shutterstock.

Harold Austin
This is real, tested it in the past on an email account, the guy used standard spear phishing twitter emails. Looked quite good but would not fool a security enlightened citizen. Never paid him of course…
Tom Fiorillo
The Deep Web (not the Dark Web) contains so much information about people, it’s frightening that companies and governments connect the computers with that information to the Internet. A few years ago I was looking up an old college chum, on a whim I went to the local government site for the district in which he lives. I then went to their taxation department, and drilled down to real property tax records; there I found a floor plan for his house. A standard Google search did not show this information in the results, but reams of information about us are available simply by persevering through sites. By law this information is suppose to be public record, but by concatenating all the information you find, you end up with a pretty good dossier.