 You’d expect Apple’s OS X search engine, Spotlight, to end up with a lot of information about you.
You’d expect Apple’s OS X search engine, Spotlight, to end up with a lot of information about you.
After all, it’s programmed, amongst other things, to search through your files to create an index that makes it easy to locate your stuff.
Can’t remember where you put the stylised picture of your beloved bicycle?
Just hit Apple+Space and type the characters “bike” into the Spotlight bar.
Can’t find that email you received from the tax office?
Spotlight can track it down for you, assuming that you haven’t turned off Mail and Messages in your Spotlight preferences.
→ If you’ve ever looked at the list of programs running on your Mac and seen a bunch of mdworker processes, perhaps using a fair amount of your CPU power, those are Spotlight’s indexing drones, or “spiders”, at work.
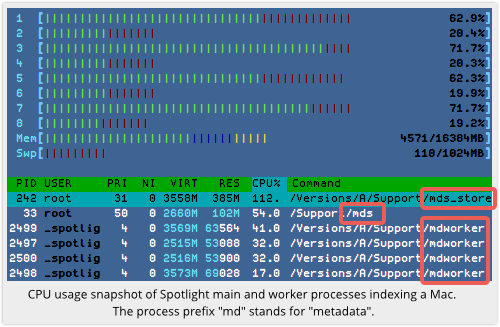
What you probably didn’t expect, though, is what German IT publisher Heise reported recently.
Spotlight can be so helpful, when it thinks it’s found something you’re after, that it plays into the hands of marketers, spammers and scammers.
The trouble with tracking
When someone sends you an HTML email, which is most of the time these days, they can include all sorts of web-like features, including images.
If they want to make sure you see the image, they can embed it right in the email itself, using a multi-part MIME message, like this:
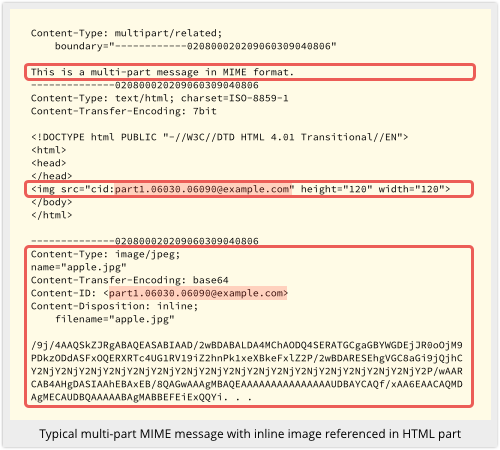
Or they can encode it directly into the HTML image tag, where it looks something like this:
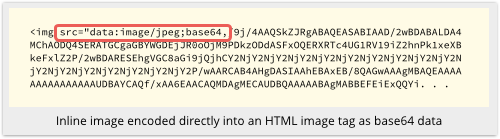
Alternatively, the sender can include the image as a web-style link, so that the image is only downloaded and displayed if and when you read the message.
The polite reason for sending images that way is that neither your email server nor your email client get lumbered with bulky base64-encoded blobs of data for messages you never get around to reading:
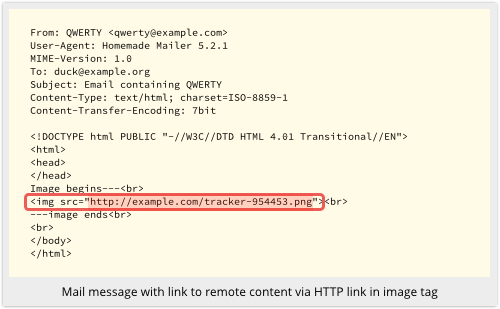
In practice, however, image links serve a less noble purpose: they are used by marketers – and by spammers and scammers – to keep track of which messages get read, by monitoring which images get downloaded.
Additionally, because your email client “calls home” to the sender’s web server to fetch the image, the sender learns exactly when you opened the email (from the timestamp in the web server logs), and approximately where (from your IP number, which loosely denotes your location).
Disable remote images
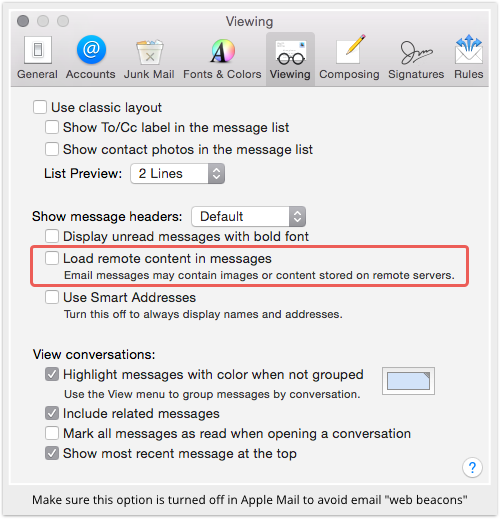
The prevalance of image-based email tracking is why we recommend that you tell your email software not to fetch remote content by default.
In the latest version of Apple Mail, you use the Mail|Preferences|Viewing dialog, and make sure that Load remote content in messages is off:
If you receive a message with a remote link, such as the QWERTY example we pictured above, you’ll see only the text that is in the message, plus a Load Remote Content button:
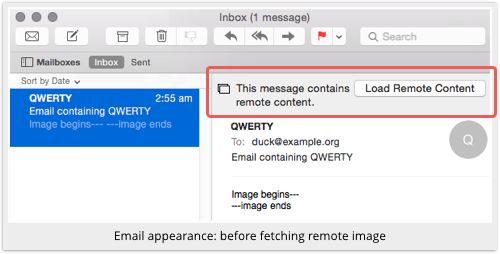
If you decide you trust the sender enough to fetch the images (you can review the actual HTML source of the message first by pressing Option+Command+U, if you know what to look out for), you can click the button.
Only then will the download take place and the image appear:
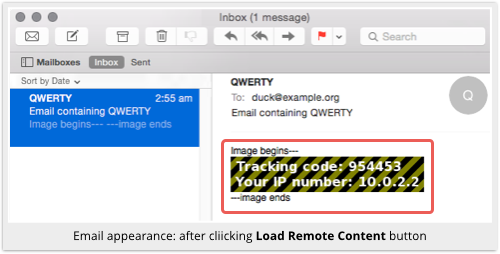
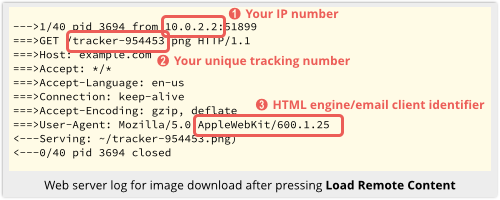
If you look at the web server logs, you’ll see, as we already mentioned, that the HTTP request issued by the Apple Mail application does, of necessity, reveal some information about you.
But at least that only happens with your say-so:
The Spotlight backdoor
Here’s where the problem reported by Heise Online comes in.
When Spotlight locates one of your emails in a search, it pops up a handy preview window.
But the preview is created by Apple’s QuickLook software component, not by the Mail application.
And QuickLook doesn’t bother to check whether you have turned Load remote content in messages on or off.
So, if you have an email where you have cautiously and deliberatly not fetched any images referenced in that email, because that’s exactly what marketers, spammers and scammers want to you do…
…then Spotlight will helpfully fetch those images anyway:
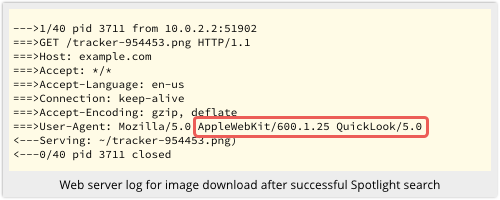
Interestingly, the image server’s web logs pretty much tell the sender that this was a Spotlight search, not a “proper” reading of the message, because of the User-Agent string in the web request:
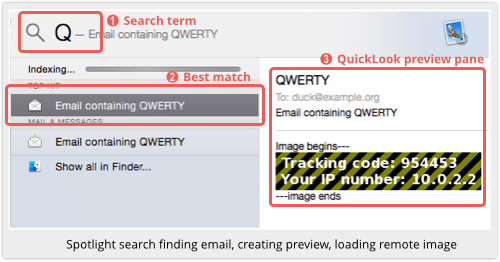
In the Spotlight search screen above, you can see that Spotlight matched the subject line in the email, QWERTY, as soon as we pressed the letter Q.
Being an uncommon letter, the first and best match was the booby-trapped email, which was immediately opened up.
Spotlight didn’t wait to see if we really were searching for QWERTY, or if we were actually more interested in quiddity or querulousness.
Additionally, and ironically, the very act of searching for spam to delete it could trigger any “web beacon” image links that it contains.
What to do?
This can’t really be considered a catastrophic vulnerability.
But it is a privacy problem, and Apple needs to fix it.
Here are two possible directions that Cupertino could take:
- Make QuickLook and other low-level data processing components retrieve the security and privacy settings of all installed applications that are associated with the content it is previewing. Honour the strictest settings found.
- Move important security and privacy settings into System Preferences. Where individual applications or system components wish to override these defaults, allow stricter settings only.
In the meantime
If you are willing to forgo searching inside your mail and messages, you can tell Spotlight not to include them in its results:
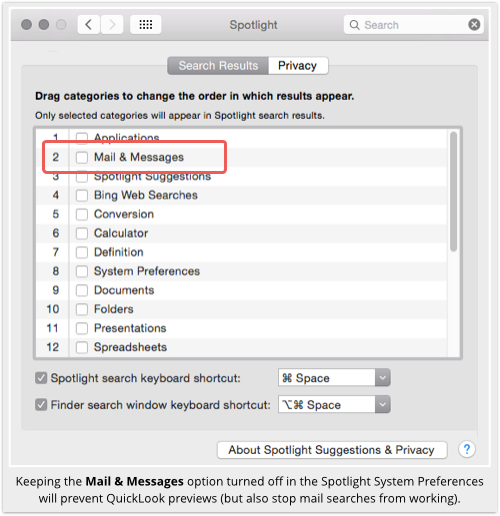
→ The Spotlight options will probably appear in a different order on your Mac. You may find Mail and Messages down on the second page, below 12th place. The order of the settings merely decides the order in which they are shown in the search results, so you can put the ones you find most useful closer to the top.
If Mail and Messages is turned off, then Spotlight won’t display any matches from your mail files, so QuickLook will never be called upon to produce an email preview window, and unexpected web-beacon tracking won’t happen.
You won’t be able to search through your emails, though, until Apple makes it safe to turn Mail and Messages back on.
