These days, crooks aren’t just after your banking passwords or your credit card numbers.
Hacked social media accounts have real value in the cyberunderground, because they provide crooks with a way to reach out convincingly to your friends and family.
If a random stranger tells you to click a link, install an app, or download a file, you’ll be suspicious; but if your mum, or a close friend, or your boss does the same thing, you’ll be inclined to believe them.
So, following our recent warnings about scams trying to phish your Instagram account passwords…
…in this article we’ll show you the other side of that nasty equation.
Here’s what the crooks actually do with social network accounts once they’ve got access.
This one was received by one of our team via their LinkedIn account, and at first glance it seems unexceptionable:
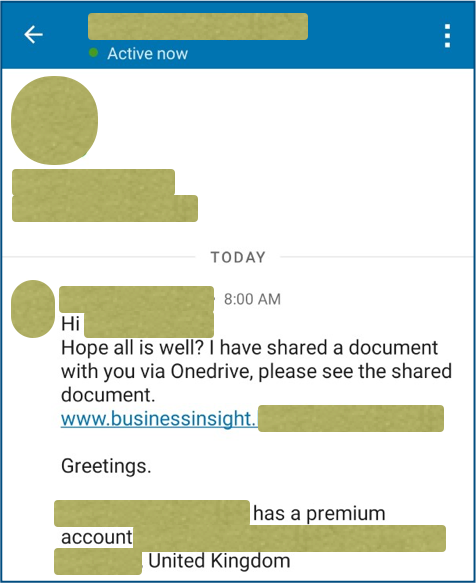
The sender was someone that the recipient knows in real life and keeps in touch with professionally via LinkedIn.
Sending cloud-based documents to business contacts – using online file storage services such as OneDrive, DropBox and Google Docs – isn’t unusual.
If the file has a personal angle, such as privately asking you if you’re interesting in applying for a new job, it’s perfectly reasonable for the sender not to mention the nature of the document in the original message.
In this case, the recipient was suspicious right away because the sender used their full name, rather than the shortened form they usually go by.
The URL started with the believable text www.businessinsight, giving it a genuine look, but ended with the name of someone else’s website – in this case, an professional entertainer in the USA, whose server had apparently and unobtrusively been hacked.
Clicking the bogus link used a redirection script on the hacked server to divert the request to a second server, this time for a business in Mexico – complete with a valid HTTPS certificate to put a padlock in your address bar.
The final URL ended with /office365, so we’re assuming it was supposed to come up as a clone of the Microsoft Office365 login page that would invite you to enter your username and password – not entirely unexpected, given that the sender of the scam message explicitly mentioned using OneDrive, which is part of Microsoft’s Office365 ecosystem.
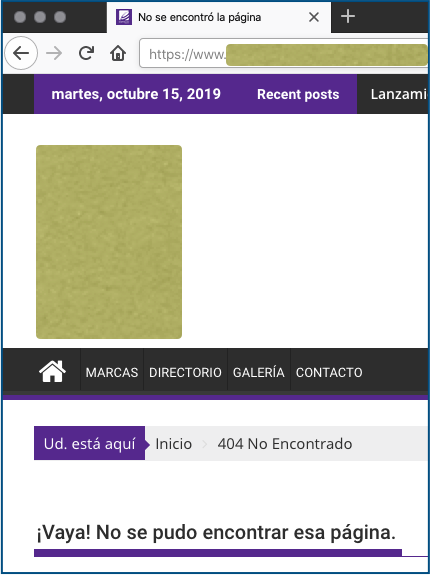
Fortunately, it looks as though the affected site in Mexico has already spotted this scam and removed the offending content, because we ended up on a 404 No Encontrado page – 404 is the HTML code for “not found”, and no encontrado means “not found” in Spanish:
What else are the crooks up to?
We wondered if the same crooks were running any other scams via different subdomains of the entertainer’s website, so we tried related text in place of businessinsights, and immediately hit pay dirt:
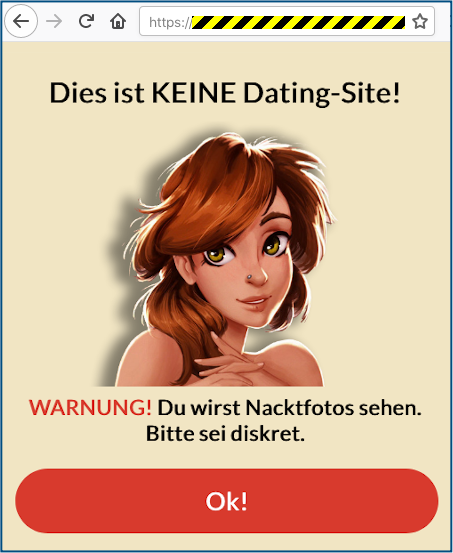
All the other subdomains we tried redirected us to one of several different “dating site” portals, all of them NSFW.
The content varied by the country from which we initiated the connection, but all of them made their nature pretty clear – and expected you to sign up and pay a fee before you could go much further.
As far as we could tell, all the diversions were handled via the same PHP redirection script on the unfortunate US entertainer’s site.
By redirecting only URLs that the entertainer himself didn’t intend to serve up, and thus wouldn’t know to look for, the crooks made sure that that the original web pages continued working just fine, so neither he nor his customers would see anything unusual.
Nevertheless, the redirection script provided the crooks with a general-purpose mechanism for running a range of different spamming, phishing and scamming campaigns at the same time, with the target site determined by the URL that the crooks used each time.
By default, the crooks seem to be trying to earn referral fees from sexual hook-up sites; but for at least one specific domain, they’re phishing for new online passwords.
What to do?
Our colleague promptly did the right things, namely: didn’t click through “just to see what might happen”; asked us to investigate; and contacted the sender to warn them that their account had almost certainly been hacked.
We recommend that you react the same way if someone you know acts out of character and sends you a message that doesn’t feel right:
- Check for giveaway mistakes. Unfortunately, the crooks don’t always make typos, or use the name you only get called by your mum when you are in trouble. But if they do make mistakes, look out for them, and use them as a sign that the message is bogus.
- Report suspicious messages and sites to your favourite cybersecurity company. You can report potential cyberthreats – files, emails and URLs – to Sophos via our Submit a Sample page.
- Let the sender know if you can. Friends don’t let friends stay hacked, so do your best to make the sender aware. But don’t reply only to the account you think has been compromised, because the crooks may very well see your warning first and delete it. Try contacting the sender via an alternative channel, such as a phone call.
- Pass on our advice about proper passwords and 2FA. Make sure you, your friends and your family are all making it as hard as possible for the crooks to get into your accounts.
And if you’re running a web server that doesn’t need or get a lot of attention because it’s there merely as an adjunct to your non-internet-based business – for example, if you’re a plumber, or a dog-walker, or an entertainer – then don’t leave your server to the depradations of the crooks.
Make sure that whoever looks after your website for you does the right thing, including keeping up with the following checklist:
- Patch early, patch often. That includes the operating system, the server applications, and any plugins added to extend the functionality of the site.
- Pick proper passwords and use 2FA. If you can do it in your home life, they can do it in their professional lives, too.
- Monitor and report changes. Most websites are organised via some sort of content management system (CMS) such as WordPress, Drupal or Joomla. These keep a systematic record of additions, deletions and changes – a changelog can often help you find new problems before the crooks do, or spot that crooks are snooping around before they do any real harm.
LEARN MORE ABOUT SOCIAL NETWORKING ACCOUNT ATTACKS
Social networking section starts at 28’24”.
Click-and-drag on the soundwaves below to skip ahead in the podcast.
Audio player above not working? Download MP3, listen on Soundcloud or on Apple Podcasts, or get it from Spotify.
STAY SAFE ONLINE – OUR TOP TIPS IN JUST 60 SECONDS
The Naked Security team share their tips for staying safe online.
— Naked Security (@NakedSecurity) October 10, 2019
If you could give just one tip, what would it be?#NCSAM #BeCyberSmart pic.twitter.com/OHVfNuK6lq

Bryan
> a professional entertainer in the USA, whose server† had apparently and unobtrusively been hacked
† also his domain registrar–unless a wildcard DNS directive sends
WhateverYouCanImagine[.]ViolatedEntertainer[.]com
to the same host.
…and this story thereby provides an answer to the question we’ve all asked in the name of convenience:
“We can add a subdomain anytime, without updating DNS–what’s the downside?“
Bryan
The article doesn’t mention whether someone reached out to the entertainer,† so I hope someone has.
† cue ragtime piano music
Paul Ducklin
By the time the article went live, the redirects were no longer happening – you’d get an error instead. Someone definitely changed something, and I don’t think it was the crooks!
Paul Ducklin
I assumed it was a DNS-only hack at first – I reasoned the same way as you – and therefore that someone had simply added a heap of subdomains and served them up for themselves.
But all the bogus subdomains I tried ended up back at the main website, redirected to the same PHP script, from where they were re-redirected, either into an ecosystem of PII-grabbing “dating sites”, or to the bogus OneDrive login URL.
Because of that, I inferred that the hack involved some sort of unauthorised changes on the main server, regardless of what else the crooks did, so I focused on that aspect.