If you’re one of the 100,000+ users of AMP for WP, good news – the popular plugin for implementing Accelerated Mobile Pages returned to WordPress.org last week.
AMP is a Google technology through which users of publishing partners such as WordPress can create pages that will load faster on mobile devices. Doing that requires a plugin, which is where AMP for WP comes in.
The plugin’s hiatus, which began when it abruptly disappeared on 21 October, was starting to look a little unusual.
According to a note from the developer, the reason for the disappearance was an ominous-sounding security flaw that “could be exploited by non-admins of the site.”
It also said that existing users could continue using the plugin in the meantime, which wouldn’t have sounded terribly reassuring to anyone using it in its vulnerable state as the days turned into weeks.
We’ve got a report from the WordPress that they found a security Vulnerability in our plugin which could be exploited by non-admins of the site, so to prevent the exploitation they temporary withdraw our plugin for further download. But the existing user’s will be able to use the plugin like always.
The day after AMP for WP reappeared on WordPress.org on 14 November, WebARX, the company that discovered the security problems, finally explained the weakness.
Wrote researcher Luka Šikić:
In WordPress plugin development, you have the ability to register ajax hooks which allows you to call functions directly on
wp-admin/admin-ajax.php?action=action_name.
Except this hook didn’t check a user’s account role, which meant:
Under plugin settings, admins can place ads, add custom HTML in header or footer and since there is no user role validation, any user could inject their ads, mining scripts or javascript malware.
In other words, a sneaky elevation of privileges that would be impossible to detect until the damage had been done.
What to do
The patched version of AMP for WP is 0.9.97.20 (see full changelog) so applying this should be the first priority. If a site allows open user registration, applying this update becomes a critical issue.
You can check if you have the Accelerated Mobile Pages plugin by logging in to WordPress and choosing Plugins from the menu. If any plugins need updating they will appear orange in the list of plugins, and if you have the latest version of AMP for WP it will appear blue, like this:
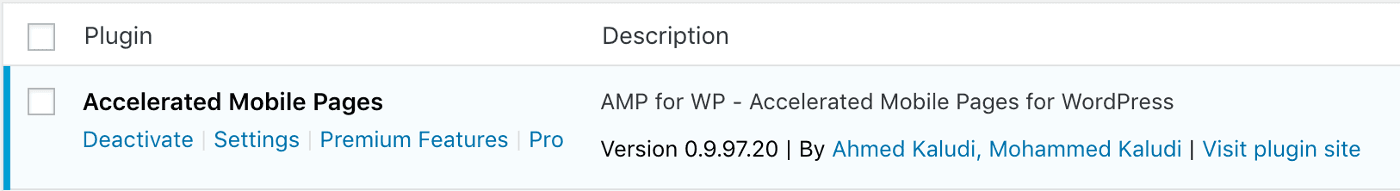
A useful next step is to ask if your site needs user registration at all. Switching it off makes your site less prone to this class of vulnerability (see the recent WordPress GDPR plugin flaw for a related example of the same problem), and it’s easily done by simply unchecking the tick box under Settings > Membership.
If you plan to leave registration turned on, simply be aware that it comes with additional risks.
As ever, we should always start by making life harder for attackers.
