Do you remember the infamous Morris worm that paralysed the internet back in 1988, or the Christmas Tree worm that hit IBM mainframes in December 1987?
Well, BACKLASH goes back further than both of those – all the way back, indeed, to the 1830s, so it predates even electrical telecommunications, let alone the era of electronics.
Until the first commercial installation of an electrical telegraph by Englishmen William Cooke and Charles Wheatstone in the late 1830s, telegraphy – short for “distant writing” – relied on optical signalling devices.
These devices worked mechanically and typically relayed messages between observers perched in towers, equipped with telescopes.
And it was a on just such a mechanical system, known as the Chappe Telegraph after its French inventor, Claude Chappe, that the BACKLASH vulnerability was exploited in the early nineteenth century.

OK, we made up the cool-sounding name BACKLASH for the purpose of this article.
(Backlash is unwanted play in a mechanical system of gears and pulleys that causes it to operate imprecisely, so our excuse is that the name is a relevant figure of speech.)
What’s ahead is a fascinating story nevertheless, for which we’re thankful to North American technology journalist Cory Doctorow, who brought it to our attention earlier this week.
Doctorow was writing about a 2017 essay by technohistorian Tom Standage, intriguingly entitled The crooked timber of humanity, where Standage describes what he calls “the world’s first cyberattack”.
That got my attention!
World’s first cyberattack?
The BACKLASH trick had to do with market prices for stocks and bonds, given that you could play the market to your advantage if you could get hard facts fast while everyone else was left to guess.
In the 1830s, data moved slowly.
News from Paris to Bordeaux could take days to travel the 500km or so between the cities, so the Blanc brothers, bond traders in Bordeaux, set out to find a covert method to be the first people in the Bordeaux to get information on whether the market was rising or falling.
The obvious fast-track for stock market data was the aforementioned Chappe Telegraph network, which connected up many cities in France in the 1830s, including a circuit that relayed data from Paris to Bordeaux.
But bandwidth was seriously limited, and the network was built to serve the government in general and its military intelligence needs in particular.
The Chappe network was therefore a tightly closed system operated under strict protocols designed to prevent commercial use, including the bond market purpose envisaged by the Blancs.
You can imagine where this is going.
The Blancs found a way to inject their own data into government transmissions in a way that they could detect the inserted data further down the line, but without affecting the final message and thus giving the hack away.
As both Standage and Doctorow documented, the Blancs used the 1830s equivalent of the Backspace character to pull off this add-then-remove detectable data trick.
Apparently, the brothers bribed a telegraph operator in Tours to insert what’d we now call in-band signals, and paid an accomplice just outside Bordeaux to keep an eye on the penultimate tower in the telegraph line through a surreptitious telescope.
The accomplice read off the in-band data, which reported whether the bond market was rising or falling.
What Standage and Doctorow missed
That’s a cool story all on its own, but we couldn’t help feeling that both Standage and Doctorow skipped some intriguing aspects of the saga.
Why rely on Backspace codes, which were obviously at risk of being purged from the data stream along the way?
Even more significantly – a detail mentioned only in passing by Standage – the Blancs injected the data at Tours.
But why start the hack in Tours, given that it’s almost half way to Bordeaux, and therefore more than a day’s ride from Paris to start with?
We decided to dig more deeply, hoping to figure out exactly how the Chappe network’s message signalling worked so we could offer a full technical explanation of the hack.
We finally settled on three fascinating publications on the subject as our main references: one by French researcher Prof. J-M. Dilhac, the second by Dutch-American computer scientist Gerard Holzmann, and the last by English engineer John Hearfield.
Unfortunately, the more we found out, the less we really knew about the Chappe system, not least because its protocols were continually adapted until the record left behind was bewildering, leaving an accurate re-implementation from scratch as good as impossible.
Indeed, John Hearfield had much the same confusing exploratory experience that we did, saying with candid clarity:
The system couldn’t work without [control signals such as a sort of
Backspace], and I had intended to explore how the Chappe brothers solved this problem, and then compare it with more modern solutions. Several websites claim to describe the special signals, but I have little confidence in any of them since they contradict one another. […] It’s all very confusing, and I can’t untangle it.
But why stop when you’re having fun?
Network signalling
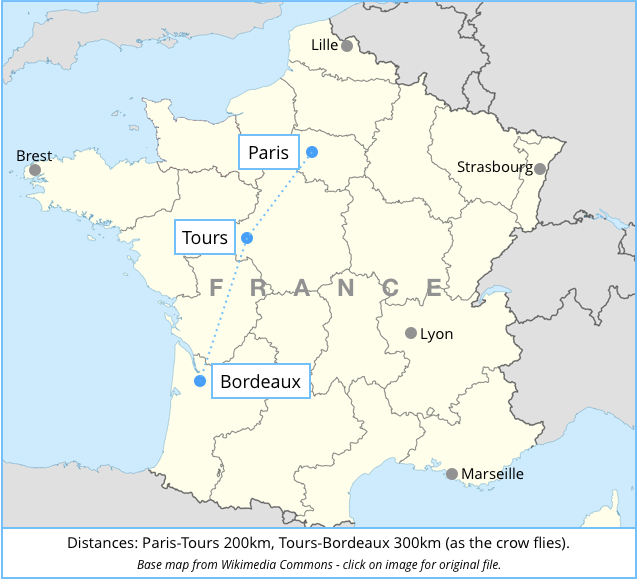
The Chappe system relied on a network of towers fitted with mechanical arms that could be seen, on a clear day at least, through a telescope on the next tower, typically 10km to 15km away.
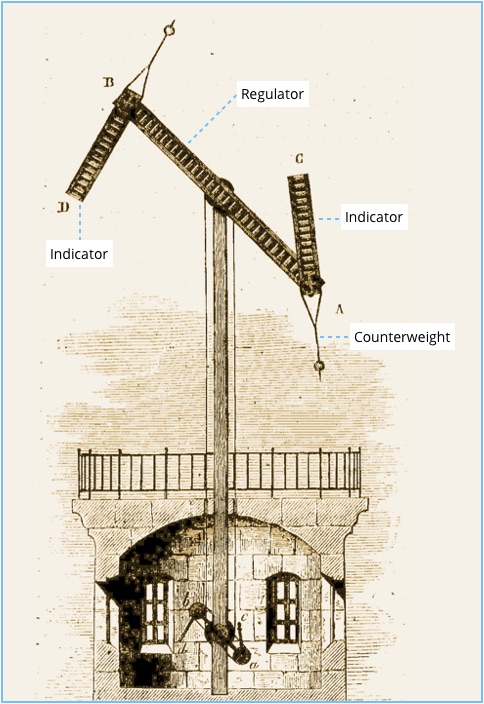
With two small arms known as indicators at the end of a longer arm of about 4 metres called the regulator, and with eight positions for each indicator and four for the regulator, a large number of different states could be represented by adjusting the ropes connected to each of the arms.
In theory, a four-position regulator with two eight-position indicators can depict 4×8×8 = 256 different data states, just like an 8-bit byte can today.
By signalling each symbol in a message in turn, and waiting for the next tower along to acknowledge receipt, data could be trickled down the line, jumping 10km or more at each step until it reached the city at the other end of the circuit.
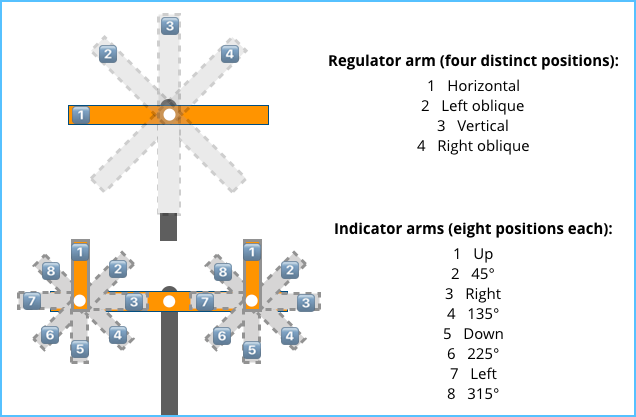
In practice, however, only two of the four regulator positions (horizontal and vertical) were used to signal data symbols, and the indicator positions in which the arms stuck straight out from the regulator were avoided.
Apparently, full-stretch indicators (positions 7 on the left and 3 on the right in the indicator arm diagram above) were difficult to distinguish from indicators tucked in behind the regulator, and therefore the stretched-out positions weren’t used.
Each data signal could therefore pick from two regulator positions and two sets of seven indicator positions, for 2×7×7 = 98 different settings in total, almost as many as can be stored in a packed binary-coded decimal (BCD) byte these days, where the numbers 0-99 can be represented.
We’ll call each of these data representations a “step”, which we think is what the French word used at the time (temps) refers to.
As far as we can tell, the standard data transmission unit in each data packet of a Chappe telegraph message conveyed two steps, for a maximum of 98×98 distinct values that could be conveyed in each tower-to-tower signal.
In practice, not all 98 step codes were used each time, but there were still about 8000 different values (roughly 213 values, or 13 bits of data) that could be encoded into each two-step transmission packet.
Amusingly, transmission speeds depended on who was telling the story, just as they do with broadband providers today.
Holzmann lists some official figures of the day, quoting best-effort tower-to-tower signalling rates of 5 seconds to 11 seconds each, but the average signalling latency seems to have been assumed at about 20 seconds.
In fact, common estimates of the real world numbers suggest that 30 seconds would be a fair guess at the average, taking into account variable factors such as the weather and operator skill.
13 bits every 20 seconds is about 40 bits a minute, or just 3 kilobytes a day, assuming ten usable hours of daylight and continuous operation.
The use of codebooks, however, for example where 4008 might stand for a common phrase such as “until tomorrow” or “in the English Channel”, gave a form of compression that would get more out of 3 kilobytes that just 3000 individual characters in a handwritten message.
Nevertheless, you can see why the government wanted to keep the bandwidth for itself, even though it could have made a fortune selling it off given its scarcity.
Why backspaces, and why Tours?
The details omitted by Standage and Doctorow – why backspaces, and why Tours? – turn out to be the most intriguing parts of the story.
Apparently, part of the security of the Chappe system was based in obscurity.
Regular telegraph operators, of whom there were of necessity many, were never taught what the various signal arm positions meant, except for those positions needed for error correction and flow control.
That’s a bit like teaching them about zeros and ones, and how to encode a byte of 8 bits and frame it with a start bit, a parity bit and a stop bit…
…but only telling them the first 32 entries of the ASCII table – the ones known as control characters.
In other words, unless the Blanc brothers had been able to bribe a high-up telegraph officer, one entrusted with the data codebooks, they couldn’t have added sensible text into official messages anyway, so their ruse would never have worked.
With a lowly telegraph operator on their payroll, they could insert signal codes of their own devising, but only if they immediately used a Backspace to get rid of them in the final transcript, where they would stick out like sort thumbs.
The Backspace trick was therefore born as much of necessity as of technical smarts.
As for Tours, it turns out that any telegraph station at which multiple signalling lines met – a network hub or router in modern parlance – was operated a bit like an email server, using what’s known as store-and-forward.
Tours was a hub, so messages arriving there weren’t immediately sent on to the next tower, one 13-bit packet at a time, because there were multiple “next towers” to choose from.
Instead, messages were received in full, decoded by a high-ranking telegraph Director, and queued up for retransmission later, after they’d been re-encoded, once again by a Director.
Obviously, any sneaky in-band data inserted by means of control characters such as Backspace was not carried across during the decoding process, which repaired the message by performing any necessary error corrections, leaving a clean message to be re-encoded later.
So, because the Blancs couldn’t unleash their BACKLASH hack in Paris itself, because their Backspaces would be lost before Bordeaux, they first needed to get the news across the first 200km to Tours, without drawing unwanted attention to the crooked telegraph operator.
Apparently, they sent innocent-looking packages that would be unsuspicious if ever they were intercepted and opened.
The data, a single bit, was encoded in the colour of the wrapping paper, with white paper to denote “market rising” and grey to denote “market falling.”
From Tours, of course, the Blancs could sneakily piggy-back on the government’s high-speed data link, with each packet travelling about 10km every 30 seconds for the last 300km of the journey, way faster than any stagecoach, horse rider or even carrier pigeon.
By this subterfuge, they were able to get market news ahead of other bond traders in Bordeaux.
How it ended
The BACKLASH system of covert in-band signals, what today we know as steganography, went unnoticed for two years, from 1834 to 1836.
Apparently, the scam was never detected by technological means, even though every packet in every transmission was supposedly logged at every tower along the way.
It seems that BACKLASH was only exposed when the crooked telegrapher needed to take a leave of absence in the summer of 1836.
He tried to recruit his replacement to be a stand-in steganographer while he was away, but the newcomer reported the scam instead of joining it.
Interestingly, the Blancs were tried for their “cybercrime” but found to have broken no law in force at the time.
They were therefore acquitted in 1837.
Whether they or other traders carried on using the BACKLASH hack after it was exposed, whether the authorities thereafter made the effort to look out for suspicious “errors” in transmission, and whether tricks like BACKLASH were subsequently criminalised, we can’t tell you.
Our guess is that the Blanc brothers figured they’d played the game hard enough already, and decided to quit while they were ahead.
What to do?
- Don’t ignore your logs. If you keep them, make them serve a security purpose by looking for anomalies.
- Don’t rely on security through obscurity. Once the secret’s out, you’ve lost the battle.
- Don’t blindly recover from errors. Errors, especially those you can’t yet explain, may be trying to tell you something, so try to understand why, not merely what.
- Don’t let protocols and data formats get so complicated that the next generation can’t understand them. HTML, the syntax of the Bash language and Content Security Policy, we’re looking at you.

Anonymous
Cory Doctorow is a Canadian not a Tank!!
Paul Ducklin
Actually, he’s British, isn’t he? (Though I guess that doesn’t stop him being Canadian as well.)
By “US journo” I meant “journalist in the US”, which I think is true (he lives in California, does he not?) but I agree that doesn’t it necessarily read that way. I am going to change it to “North American”, which ought to do the trick.
Thanks for the note.
DannAgro
Thanks, Paul for a fascinating history lesson. I’d seen pictures of the arms and regulatory in old encyclopaedias, but not realised the sophistication of the system.
Paul Ducklin
As far as I can make out, by the end of the Chappe Telegraph’s life (it saw service in Crimea in the 1850s, because it was still easier to set up than running the wire needed for an electric telegraph, but that after that the electric telegraph swept it aside), the signal encoding had gone from “en deux temps et trois mouvements” (two steps of data, conveyed by three three movements of the signalling arms) to a series of variant encodings that required up to “quatre temps” (four steps) per data packet, giving access to three additional codebooks, presumably of up to 8000 code entries each.
Details are scant, and you imagine that complexity would be greatly increased, along with an increase in transmission errors, give the number of times the operator would need to flap the arms to convey each symbol if the fifth codebook were in use. Holzmann has a discussion of the extended codebooks on p.34 of the PDF I linked to above.
John
Also reminds me of the Grand Trunk Company, in Going Postal by Terry Pratchett.
Mahhn
Very cool. Thanks.
Gavin
Fabulous!
Nomphra
Yes, this was a fascinating read!! Thank you so much for this article!! :)
enyeword
I enjoyed this article!
Small typo: “bea” for “be a”
Mark Stockley
Fixed, thanks!