Network hardware vendor DrayTek has announced a security hole in its Vigor range of routers.
About 20 different models are affected, most of which seem to have firmware patches available already, so if you have a DrayTek Vigor, please go and check right away if you’re affected.
DrayTek hasn’t given precise details of how the attack works, which is probably a good thing, but it seems to involve what’s known as Cross Site Request Forgery (CSRF).
That’s where a crook can trick your browser into sending commands to websites you’re still logged in to, behind your back. In this case, the website in question is the web interface of your router.
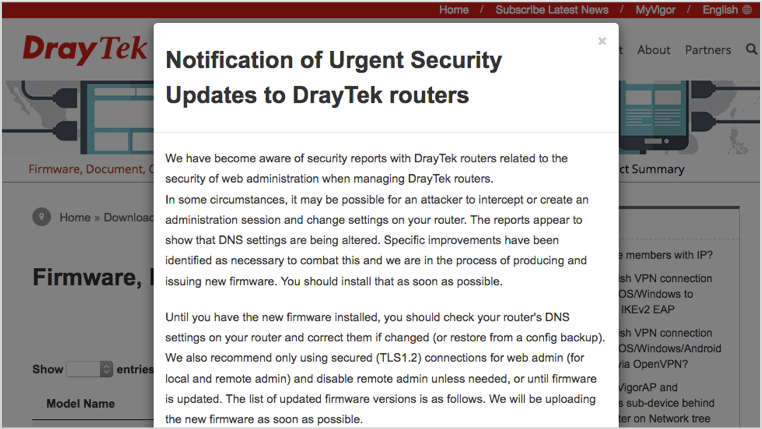
We have become aware of security reports with DrayTek routers related to the security of web administration when managing DrayTek routers. In some circumstances, it may be possible for an attacker to intercept or create an administration session and change settings on your router.
It seems that cybercriminals have been tricking some DrayTek Vigor routers into altering DNS settings via the router configuration interface, switching your DNS server from the one you usually use to an imposter server operated by the crooks.
We don’t have an exhaustive list of rogue DNS servers associated with this security hole. However, DrayTek reports that the IP number 38.134.121.95 can be considered an IOC, or indicator of compromise, as it seems to be owned by crooks. You can find out the IP number of your usual DNS server (or servers) by asking your ISP, or you can chose a trusted public DNS server like Google’s well-known service at 8.8.8.8.
This sort of cybercriminal trick is called DNS hijacking, and it can be tricky to spot – typically, the crooks run a DNS server that mostly tells the truth, so that your web browsing works just fine most of the time.
Imagine, for instance, that you regularly use a search engine called findme.example, located at the IP number 192.0.2.42.
If the crooks control your DNS server, they might tell you the truth about findme.example 99 times out of every 100 times you visit, sending you unexceptionably to the legitimate server at 192.0.2.42, just as you’d expect.
But 1% of the time, they could direct you to an imposter server at, say, 198.51.100.6, and you might very well not notice the anomaly.
Worse still, if you do notice and decide to investigate, everything might be back to normal, leaving you to shrug and carry on unsuspiciously.
What to do?
DrayTek has put up a decent advice page for its UK users, handily headlining it with the text:
TL;DR – Check the DNS settings on your DrayTek router and install new firmware. Please read all of this advisory.
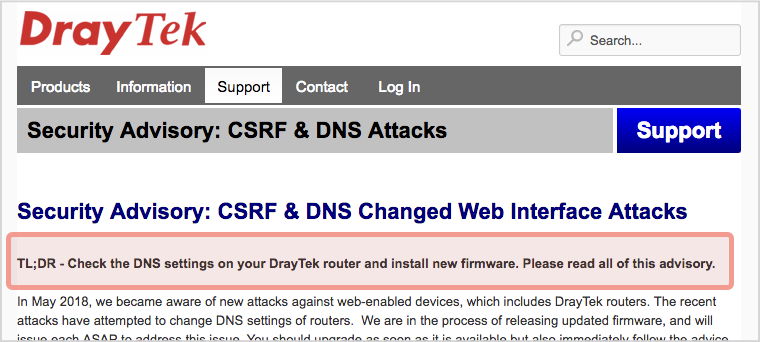
Take DrayTek’s advice: the article is well worth reading even if you’ve already updated your firmware (indeed, it’s useful even if you don’t have a DrayTek router) because it’s full of security tips that are worth doing anyway.
In particular, it seems that this CSRF security hole only works if you previously logged in to the DrayTek administration interface, and then never logged out.
Make a habit of logging out explicitly from your router before closing the admin screen, so your browser won’t be able to reconnect automatically, either by accident or design.
In fact, even though it’s a bit less convenient, we recommend logging out from any website or online service when you aren’t using it – that includes Facebook, Twitter, your webmail, and so on.
Try to be logged in less, not more, so you’re less likely to catch yourself out, or to be caught out by crooks clicking buttons on your behalf.
