Star Trek fans might remember an episode from the original series where our heroes were transported to a mirror universe where their counterparts served an evil version of the Federation. At the end of “Mirror Mirror“, it is the alternate universe’s Spock who begins to set things right.
One has to wonder if the creators of the recently discovered Kirk ransomware had that episode in mind. SophosLabs threat researcher Dorka Palotay told Naked Security that this new specimen appeared a few days ago.
It hasn’t shown much by way of teeth to date – the lab has only seen two samples so far. But its features are certainly noteworthy.
It’s encrypted, Jim
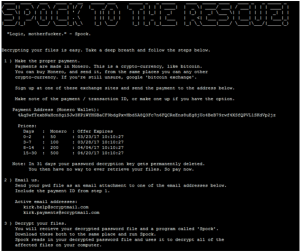
The first sample is Star Trek-themed, which appends .kirked to the name of the encrypted files. The ransom note that goes with it offers a program called Spock to decrypt the files – for a fee, of course.
The Kirk ransomware is written in Python and uses the usual encryption methods: AES to encrypt the files and RSA to encrypt the AES key. The encrypted AES key is saved in a file called pwd. Decryption is impossible without this file.
Palotay said the ransomware displays a message box, claiming to be the so-called Low Orbital Ion Cannon program, an open source network stress-testing application. Then it encrypts more than 600 different file types.
The second sample is a variant of Kirk ransomware, which calls itself Lick ransomware. Palotay said:
It works very similar to the previous one, except that it appends .Licked extension to the encrypted files, sends the encrypted key to pastebin.com and disguises itself as a decryptor.
Monero is the new (or old) latinum
Unlike the ransomware families SophosLabs has seen so far, this family uses Monero for ransom payment, which is a cryptocurrency similar to bitcoin. Monero has already been popular among cyber-criminals. You could say it’s the new latinum – the favored currency of the Ferengi. Or, you could say it’s the old one. (These temporal paradoxes give us a headache.)
SophosLabs researcher Attila Marosi wrote a paper last year about Mal/Miner-C malware, which criminals are using to mine this cryptocurrency.
SophosLabs detects this ransomware as Troj/Ransom-EJN.
How to protect yourself
Though this ransomware seems small at the moment, it’s worth a reminder about the advice we regularly offer to prevent (and recovering from) attacks by ransomware and other malware.
Here are some links we think you’ll find useful:
- To defend against ransomware in general, see our article How to stay protected against ransomware.
- To protect against JavaScript attachments, tell Explorer to open .JS files with Notepad.
- To protect against misleading filenames, tell Explorer to show file extensions.
- To learn more about ransomware, listen to our Techknow podcast.
- To protect your friends and family against ransomware, try our free Sophos Home for Windows and Mac.
Techknow podcast — Dealing with Ransomware:




RichardD
“Start” Trek? :o)
(First sentence under the “It’s encrypted, Jim” heading.)
Kate Bevan
Well spotted, and thanks! Fixed now!
Bill Brenner
Gah! Thanks, Richard.