DNS is short for Domain Name System, the online service that converts server names into network numbers.
Without it, you wouldn’t be able to refer to a server called example.com – you’d have to remember 93.184.216.34 instead.
Actually, it’s even worse than that, because busy websites like www.facebook.com don’t have just one network number.
Big web properties may have racks and racks of customer-facing servers in operations centres all over the world, giving them a wide variety of network number ranges on a wide variety of different networks.
Busy sites typically use DNS to direct you to a specific server based on load levels, maintenance schedules, your current location, and so on, in order to improve speed, spread load and avoid bottlenecks.
In other words, DNS is extremely important, to the point that the internet would be unusable without it.
For that reason, DNS is implemented as a hierarchical, distributed global database, which is a fancy way of saying that no one DNS server holds the entire database, and no one server is critical to the operation of all the others.
For example, to figure out where nakedsecurity.sophos.com lives, your own company’s (or ISP’s) DNS server takes a top-down approach:
- Ask the so-called root servers, “Who looks after the .COM domain name data?”
- Ask the .COM part of the hierarchy, “Who is officially responsible for DNS for SOPHOS?”
- Ask the SOPHOS name servers, “Where do I go to read NAKEDSECURITY?”
Each DNS reply contains a Time To Live number, or TTL, that says how long to remember the answer, typically somewhere from 1 minute to 1 hour, after which the result is thrown away.
That greatly reduces the number of times a full, top-down hierarchical query is needed, while ensuring that the system can recover automatically from incorrect or outdated answers.
As you can imagine, the root servers are the key to the entire DNS service, because all as-yet-unknown answers must be requested by starting at the top.
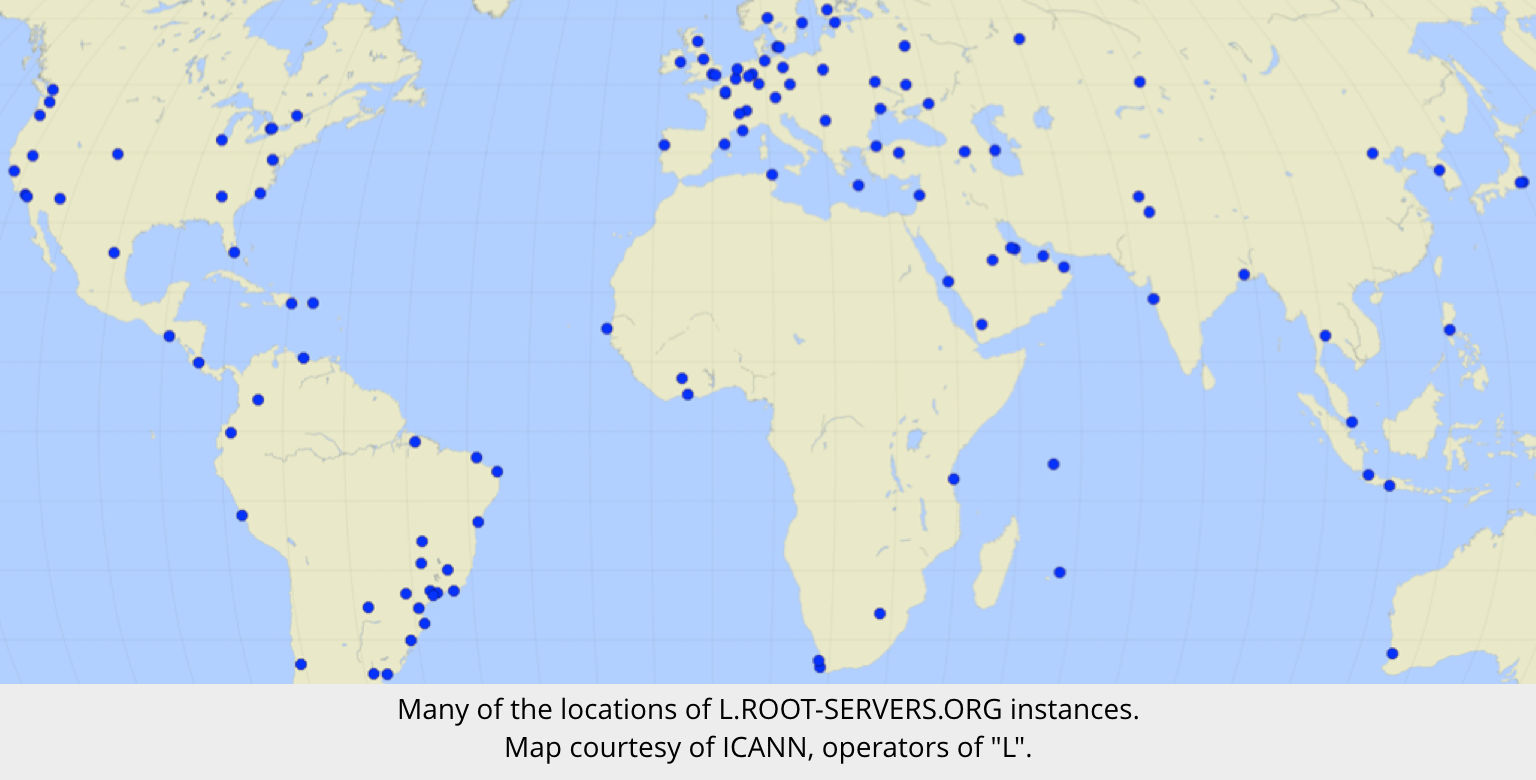
So there are 13 root servers, prosaically named A to M, operated by 12 different organisations, on 6 different continents.
In fact, each “server” actually consists of a server farm of many physical servers in multiple locations, for reliability.
Server L, for example, is mirrored in 128 locations in 127 towns and cities (San Jose, California, hosts two instances) in 68 countries, from Argentina to Yemen.
Because you need to consult a root server by number to look up where the root servers are by name, DNS servers themselves keep a static numeric list of all the root servers.
Generally speaking, only one root server IP number ever changes at a time, and such changes are rare, so even an old root server list will work, at least to start with.
A DNS server with an outdated list can try each of the 13 roots in turn, until it figures out where to update to the latest list.
In short: DNS is surprisingly resilient, by design, and DDoSing it is correspondingly hard.
A DDoS, or distributed denial of service attack, is where a cybercriminal deliberately and repeatedly generates time-wasting internet requests to bog down an online service. Like prank callers to 911 or other emergency service phone numbers, this gets in the way of genuine traffic, to the detriment of legitimate users. Extreme internet DDoS attacks may even cause the targeted server, or the network it is on, to crash.
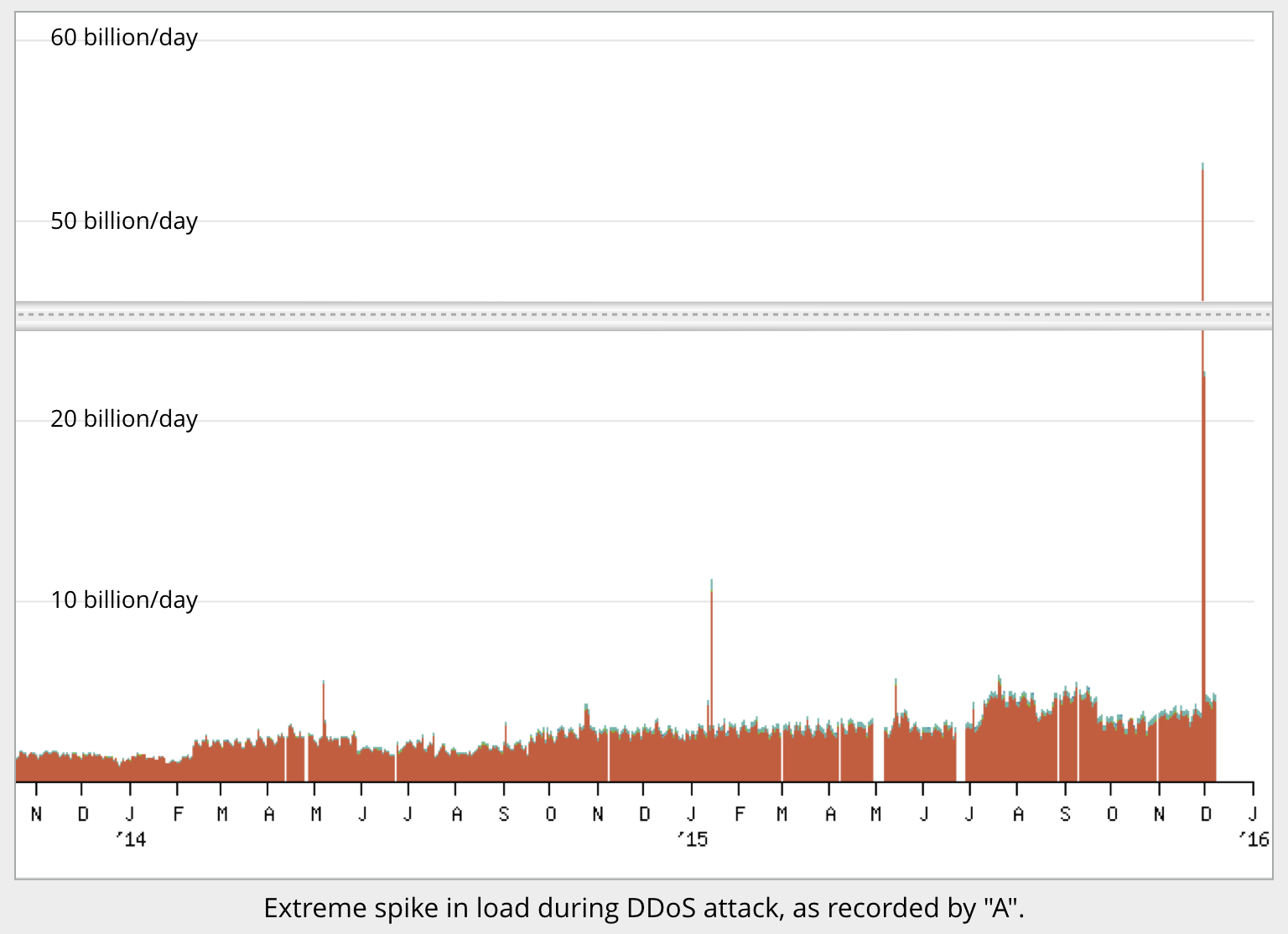
Unsurprisingly, however, the root servers do get DDoSed from time to time, sometimes on an astonishing scale.
Indeed, the Root Server Operators recently reported a DDoS on the last day of November 2015, and the first day of December, that reached 5,000,000 bogus requests per second per root server letter.
The total attack time was just under four hours, so the DNS root servers would have experienced close to 1 trillion (1012) bogus requests during the two attack windows.
There was some bad news:
The incident traffic saturated network connections near some DNS root name server instances. This resulted in timeouts for valid, normal queries to some DNS root name servers from some locations.
But some very good news as well:
Several DNS root name servers were continuously reachable from virtually all monitoring stations for the entire duration of the incident.
Simply put, the DNS root servers took an unprecendented hammering, but nevertheless stood firm, keeping the global DNS fully functional throughout.

Jake
All the things we take for granted in this world… Great article!
Paul Ducklin
Indeed. And thanks.
Anonymous
Nice treatment
Respok
What are your thoughts on using OpenDNS ?
ed horst
What would the purpose be of such an attack? Just to be a jerk and cause outages, or ??
Paul Ducklin
Yes.
Peter
What alarms me is that this gives the attackers data on what impact 5 million requests a second actually does. From that they may be able to start planning a larger attack which will have more of an impact. For all we know this was just a test run.
Maybe we will be lucky and the 12 organisations that look after the root servers will increase the amount of servers/resilience so that a future larger attack would also fail. However the pessimist in me says that the expense to do that would mean it will only happen after such an incident.
Anonymous
I was thinking something similar, if this large scale attack put whoever did this on the map.. well then their sure to come back harder.
Arne Rathjen RA
Still: who ran that attack ? Why ? What exactly would have happened if the assault
had been successful ?
A.Hostettler
The only reason to do attacks like that is Research Education and Science and it will never stop before port 0 is closed!
Science Educatin and Research is not a Crime and if ICANN and IANA learned someting it is what it is :**