You may wonder why we’re writing about Wi-Fi Protected Setup, better known as WPS, at all.
You may wonder why we’re writing about Wi-Fi Protected Setup, better known as WPS, at all.
We already outlined its dangers back in the dying days of 2011.
In fact, we said, just over three years ago, “disable WPS support.”
To summarise, WPS was invented to make it easier to get a secure Wi-Fi connection via your home router.
Usually, you’d do something like this:
- Plug a cable between your PC and your new router.
- Login to the administrative console, usually via a series of GUI screens in your browser.
- Set a decent administrative password for your next login.
- Turn on Wi-Fi, using WPA2.
- Type in a decent Wi-Fi password. (We recommend at least 14 well-mixed up characters.)
Then, when you or your friends want to jump online, you just turn on Wi-Fi on your laptop or phone, choose the right router network, and type in the WPA2 password. (The password is called a PSK, short for pre-shared key, because that’s what it is.)
Most laptops and mobile devices will usually offer to remember that password for later, so you only ever have to type in the wacky and complicated PSK once on each device.
But that’s not simple and quick enough, apparently.
It would be much easier, it seems, if your friends only had to type in a special 8-digit code that you read out to them.
Then the router would securely transmit to them the much more complex PSK, so their computer could remember it without them ever having to enter it.
After all, typing 866319 on a mobile phone keypad is much easier than typing tISa14c[!!]PWD, even if you only have to enter it once.
→ Alarm bells should be ringing in your head by now. An eight-digit PIN is also a lot easier to guess than a 14-character passphrase. So WPS is a bit like keeping the key to your high-security $10,000 company safe in a $9.99 petty cash box in the top drawer of your desk.
The first problem with WPS
The first problem with WPS turned out to be the cryptographic protocol by which a client and a router convince each other they know the 8-digit PIN.
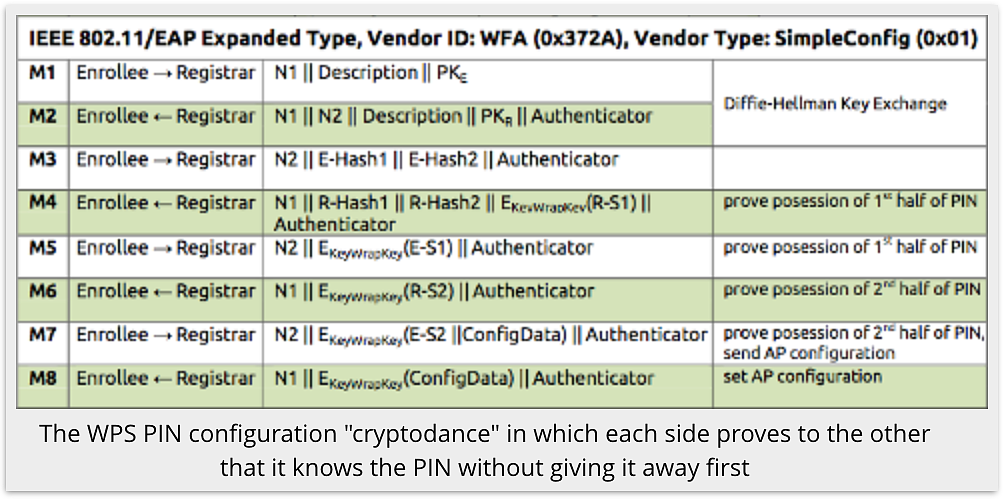
Firstly, the eighth digit of the PIN is a check digit, computed from the first seven, so the PIN is effectively only seven digits long.
Secondly, you prove you know the PIN in two stages (M4 and M6 above), each of which proves you know half of the PIN.
Thirdly, the protocol terminates immediately if you make a mistake after M4, where you verify the first half of the PIN.
In other words, once you have tried 12340000 and failed, you immediately know that every PIN from 12340000 to 12349999 is incorrect.
You don’t need 100,000,000 guesses to try every possible PIN (108, the quantity of different 8-digit numbers).
You need 10,000 guesses (104) to lock in the first four digits of the PIN, plus 1000 guesses (103) to finish the job with the three variable digits in the second half.
That makes a brute force attack just 0.01% as time-consuming as you’d expect, given 8 digits of PIN.
The second problem
What’s worse is that Swiss researcher Dominique Bongard found a defect in many router’s implementations of M3 in the protocol above.
Briefly explained, at step M3 above, the router encrypts the actual PIN, using a strong algorithm (AES) with secret keys consisting of two randomly-chosen numbers, and sends you the result.

That way, the router has committed to its proof that it knows the PIN, but in a way that you can’t verify until later.
Only after you prove to the router that you know the PIN will the router tell you those random numbers so that you can decrypt M3 and satisfy yourself that the router also knew the PIN from the start.
It’s a bit like a sealed-bid auction, where the router’s bid is locked in before yours, but in a way that you can’t see it in order to determine your bid.
But what our Swiss researcher found is that many routers didn’t seal their bids very well, using “random” numbers that you could guess, or in some cases calculate for yourself.
In other words, at step M3, you could simply fail the protocol, and set about cracking the encryption on the M3 data packet.
That would reveal the PIN directly, no guessing required.
And yet more problems
It turns out there are other holes in some WPS implementations, too.
These relate to how the router “knows” the PIN in the first place.
 Usually, the PIN is printed on a sticker under your router, so that attackers need physical access to your router first in order to get virtual access via the WPS PIN.
Usually, the PIN is printed on a sticker under your router, so that attackers need physical access to your router first in order to get virtual access via the WPS PIN.
Of course, having physical access is as good or better than having virtual access anyway.
→ The attackers wouldn’t even need to bother with Wi-Fi: they could plug directly into a wired port, and do a hard reset, once they were actually inside the cupboard under your stairs where you keep your router.
But how does the router know what’s printed on that sticker?
As a researcher known as Craig reported on the /dev/ttyS0 “embedded device hacking” site last year, some D-Link routers computed the PIN directly from the router’s MAC address.
A MAC address is the hardware identifier burned into the firmware on your network card; it is intended only to number each network card uniquely, not to have any cryptographic or security-related purpose.
Indeed, every Wi-Fi packet you transmit, even if its contents are encrypted, includes the MAC of your network card, plus the MAC of the device to which you are sending the packet.
So anyone who can sniff even a single packet from a vulnerable D-Link router can acquire its MAC address, and from that can calculate the WPS PIN.
Belkin vulnerable, too
Turns out D-Link isn’t the only one.
Many Belkin routers do something very similar, Craig found recently, although they try to be a bit more subtle.
These vulnerable routers roll part of the MAC address and part of the router’s own serial number into the number-crunching that generates the WPS key.
Like the WPS PIN, the serial number is usually printed on the underside of the router, meaning that it ought to be a secret, at least from a remote attacker.
Except that Craig found that affected Belkin routers don’t keep the serial number secret.
If you send the right sort of probe packet to a vulnerable router, you get back a response that just happens to include the serial number.
Probe packets are unauthenticated (meaning anyone can ask) and unencrypted (meaning anyone can read the replies).
Non-secret secrets
In other words, Belkin, like D-Link, sometimes uses non-secret information to compute a secret cryptographic key.
Worse still, anyone in the vicinity of your router can unsuspicuously ask your router to give away that non-secret information.
That’s like telling the world your new puppy’s name on Twitter, and then using it as your password.
What to do?
Turn off WPS on your router. (If there isn’t an option to do do, or if you turn it off but it keeps on working anyway, use a different router.)
• Don’t try to invent your own cryptography.
• Don’t try to invent your own random number generator.
• Don’t “secure” the key to your safe in your desk drawer.
• Do consider using the Sophos UTM as a secure router. (Sophos Wi-Fi products don’t support WPS. Problem solved.)
Sophos UTM Home Edition
Want a secure router for your network gateway at home?
Try our award winning UTM.
The Home Edition includes all the Sophos UTM features: email scanning, web filtering, a VPN, web application security, and everything you need to keep up to 50 devices on your home network secure, 100% free for home use.
In you live in a shared house, or you have children to look out for online, this could be just the product you need.
Better yet, you get 12 free licences for Sophos Anti-Virus for Windows that you can install and manage throughout your household, right from the UTM web console.
Understanding firewalls and secure gateways
Listen to our Sophos Techknow podcast, Firewalls Demystified
(Audio player above not working? Download, or listen on Soundcloud.)