** 本記事は、Updated: 3CX users under DLL-sideloading attack: What you need to know の翻訳です。最新の情報は英語記事をご覧ください。**
Sophos X-Opsが、国家レベルのグループによる可能性があるサプライチェーン攻撃に関する状況を追跡しています。このページでは、状況の概要、脅威分析、ハンター向けの情報、および検出保護に関する情報を提供します。
私たちは、脅威および検出ガイダンスを含め、イベントと理解の発展に応じて、このページを更新していきます。
[最新版:2023年3月30日午後3時30分(太平洋夏時間)に公開された内容には、影響を受けるバージョンの詳細、ffmpeg.dll の誤用、悪意のあるリポジトリの削除、Lazarus 脅威グループが使用する PE シェルコードローダーとの比較、攻撃への露出を決定するために顧客が使用できるさらに 3つのクエリ、およびさまざまな追加の検出情報が含まれています。]
概要
影響を受けたソフトウェアは、Windows、MacOS、Linux、Android、iOS で利用可能な正規のソフトウェアベースの PBX 電話システムである 3CX です。脅威アクターは、Windows と MacOS の一部のバージョンにインストーラーを追加して、さまざまなコマンドアンドコントロール (C2) サーバーと通信するように悪用しました。
ソフトウェアは、Windows と MacOS のソフトフォンデスクトップクライアントのデジタル署名されたバージョンで、悪意のあるペイロードが含まれています。3CX によると、Update 7 for Windows、バージョン番号18.12.407 および 18.12.416、および Electron Mac App のバージョン番号 18.11.1213、18.12.402、18.12.407、および 18.12.416 が影響を受けています。私たちがこれまでに観察した中で最も一般的な事後攻撃は、侵害されたシステムのブラウザをターゲットとするインフォスティーラーの存在です。この執筆時点では、3CX は Windows アプリケーションの影響を受けたバージョンを非推奨にしています。
現時点で、私たちの顧客データによって影響を受けたプラットフォームは Windows と MacOS のみであり、これは 3CX が提供する影響を受けたプラットフォームの情報と一致しています。サポートフォーラムの情報によると、Android および iOS のバージョンには影響がないと考えられています。
脅威の分析
3月22日、3CX のユーザーは、エンドポイントセキュリティエージェントによる 3CXDesktopApp の誤検出の可能性について議論を開始しました。
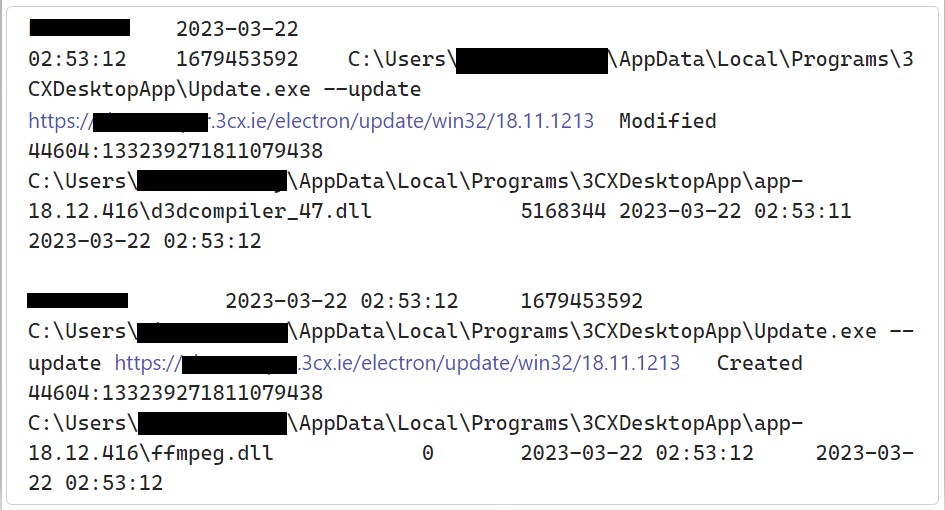
図1:悪意のあるバージョンがドロップされた瞬間のアップデートプロセス
Sophos MDR は、2023年 3月 29日に、自社の顧客に向けられた 3CXDesktopApp に起因する悪質な活動を初めて確認しました。さらに、Sophos MDR は、このキャンペーンがパブリックファイルストレージを活用してエンコードされたマルウェアをホストしていることを確認しました。このリポジトリは 2022年 12月 8日から使用されており、3月 29日に侵害のニュースが広く伝わった後、リポジトリは削除されました。
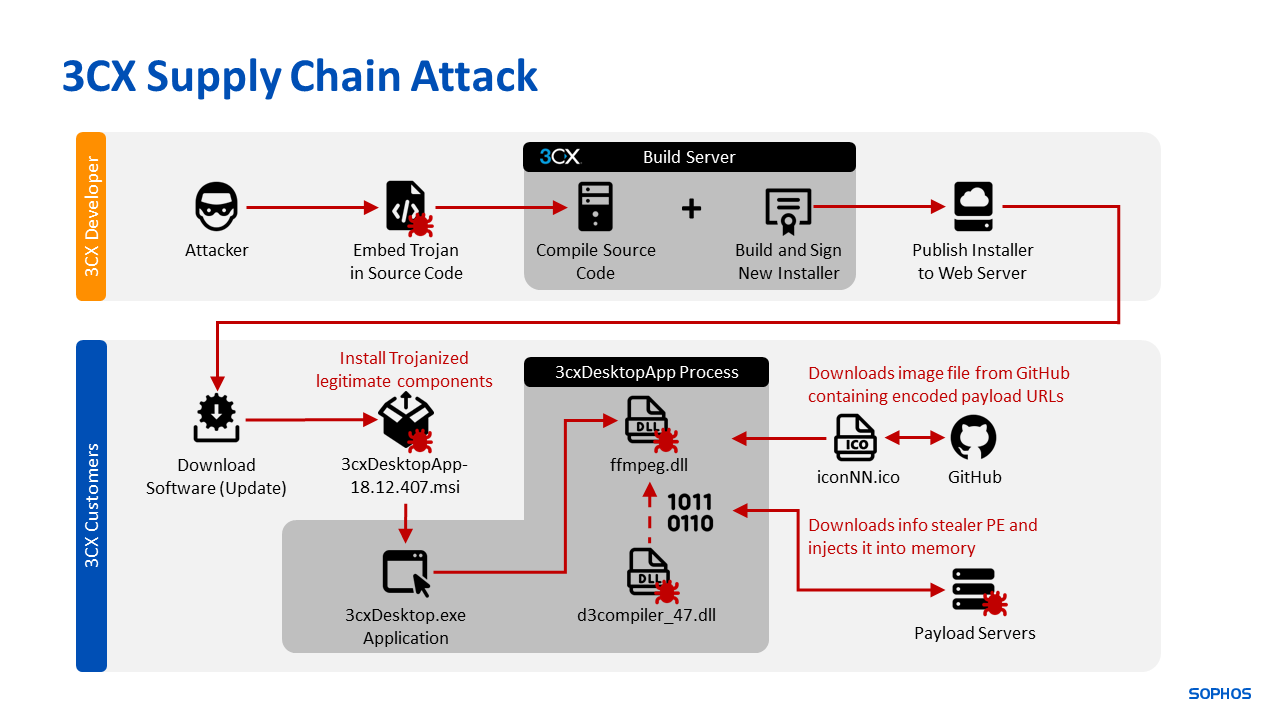
この攻撃は、DLLサイドロードのシナリオを中心に展開され、様々なコンポーネントが関与しています。これは、顧客が影響を受けたパッケージの異常に気づくことなく、3CXデスクトップパッケージを使用することができたことを保証するものと思われます。私たちは、3 つの重要なコンポーネントを特定しました。
- クリーンローダーである 3CXDesktopApp.exe
- 暗号化されたペイロードが含まれる d3dcompiler_47.dll
- トロイの木馬化ローダーである ffmpeg.dll, a Trojanized loader
図2は、Windowsで動作する攻撃の流れを高水準で示したもので、MacOS版では後のステップに若干の違いがあります。
図2:攻撃の流れを示す高水準な図
ffmpeg.dll ファイルには、https[:]//raw.githubusercontent.com/IconStorages/images/main/ の GitHub ファイルストレージから悪意のあるエンコードである .ico ペイロードを取得する埋め込み URL がありますが、やはり侵害に関するニュースが広まると、このリポジトリは削除されました。
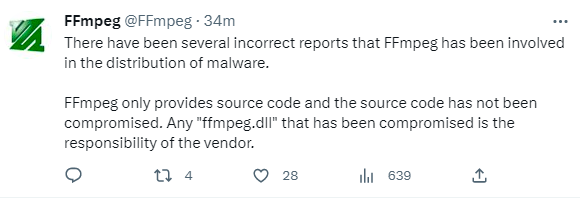
ffmpeg.dll ファイルには、3CX 独自の証明書で署名されたものを含め、いくつかのバリエーションが見られました。これらは、正規の ffmpeg.dll に悪意を持ってパッチを当てたものと思われます。木曜日の声明で、ffmpeg のソースコードに取り組んでいるチームは、3CX の侵害との関係性を避けるために注意を払っています。
図3:ffmpeg が Twitter で自分のコードを擁護した時の様子
通常の DLL サイドローディングのシナリオでは、悪意のあるローダー (ffmpeg.dll) がクリーンな依存関係を置き換え、ペイロードをキューに入れるだけです。しかし、このケースでは、3CX 製品に通常あるように、このローダーも完全に機能します。その代わりに、DllMain 関数に追加のペイロードが挿入されています。これにより、容量が増えましたが、疑惑が低くなった可能性があります。トロイの木馬のアドレスが C2 ビーコンに到達しても、悪用された 3CX アプリケーションの機能は期待通りに機能したのです。
図4:影響を受けた 3CX の開発者と顧客が経験したこと
悪用されたソフトウェアの機能を維持させることは、私たちが見てきた他の DLL サイドローディングのケースと似て非なるものですが、このキャンペーンは、私たちが見てきた現在の DLL サイドローディングのケースとも少し異なっています。特に、使用されている PE シェルコードローダが、私たちの経験上、ユニークであることに注目しています。これまでは、Lazarus グループに起因する事件でしか見たことがなく、今回のコードは、これらの過去のサンプルとバイト単位で一致している。
ハンティング情報
Sophos XDR で影響を判断する
1. ホストが脅威アクターのインフラと通信しているかどうかを判断する:Data Lake
以下のクエリは、このキャンペーンで使用されている様々な既知の URL と通信しているホストを検索するものです。
SELECT
meta_hostname,
sophos_pids,
domain,
clean_urls,
source_ips,
destination_ips,
timestamps,
ingestion_timestamp
FROM
xdr_data
WHERE
query_name = 'sophos_urls_windows'
AND
(LOWER(domain) LIKE '%akamaicontainer[.]com%'
OR LOWER(domain) LIKE '%akamaitechcloudservices[.]com%'
OR LOWER(domain) LIKE '%azuredeploystore[.]com%'
OR LOWER(domain) LIKE '%azureonlinecloud[.]com%'
OR LOWER(domain) LIKE '%azureonlinestorage[.]com%'
OR LOWER(domain) LIKE '%dunamistrd[.]com%'
OR LOWER(domain) LIKE '%glcloudservice[.]com%'
OR LOWER(domain) LIKE '%journalide[.]org%'
OR LOWER(domain) LIKE '%msedgepackageinfo[.]com%'
OR LOWER(domain) LIKE '%msstorageazure[.]com%'
OR LOWER(domain) LIKE '%msstorageboxes[.]com%'
OR LOWER(domain) LIKE '%officeaddons[.]com%'
OR LOWER(domain) LIKE '%officestoragebox[.]com%'
OR LOWER(domain) LIKE '%pbxcloudeservices[.]com%'
OR LOWER(domain) LIKE '%pbxphonenetwork[.]com%'
OR LOWER(domain) LIKE '%pbxsources[.]com%'
OR LOWER(domain) LIKE '%qwepoi123098[.]com%'
OR LOWER(domain) LIKE '%sbmsa[.]wiki%'
OR LOWER(domain) LIKE '%sourceslabs[.]com%'
OR LOWER(domain) LIKE '%visualstudiofactory[.]com%'
OR LOWER(domain) LIKE '%zacharryblogs[.]com%'
OR (LOWER(domain) LIKE '%raw.githubusercontent[.]com%' AND LOWER(clean_urls) LIKE '%/iconstorages/images/main/%')) 2. ホストが悪意のあるファイルに接触したかどうかを判断する
SELECT f.filename, f.directory, ROUND((f.size * 10e-7),2) AS size_MB, h.sha256, f.type,
f.attributes, f.mode,
datetime(f.btime,'unixepoch') AS file_created_time,
datetime(f.atime,'unixepoch') AS file_last_access_time,
datetime(f.mtime,'unixepoch') AS file_last_modified_time,
datetime(f.ctime,'unixepoch') AS file_last_status_change_time,
f.uid, u.username AS file_owner
FROM file f
LEFT JOIN users u ON f.uid = u.uid
LEFT JOIN groups g ON f.gid = g.gid
LEFT JOIN hash h ON f.path = h.path
WHERE f.path like 'c:\users\%\appdata\local\programs\3cxdesktopapp\app\%'
AND (f.filename = 'ffmpeg.dll'
OR f.filename LIKE 'd3dcompiler%.dll'
OR f.filename = 'trololo.dll')
AND (h.sha256 = 'c485674ee63ec8d4e8fde9800788175a8b02d3f9416d0e763360fff7f8eb4e02'
OR h.sha256 = '11be1803e2e307b647a8a7e02d128335c448ff741bf06bf52b332e0bbf423b03'
OR h.sha256 = '7986bbaee8940da11ce089383521ab420c443ab7b15ed42aed91fd31ce833896'
OR h.sha256 = 'aa4e398b3bd8645016d8090ffc77d15f926a8e69258642191deb4e68688ff973')
3. ホストが影響を受けるバージョンを実行しているかどうかを判断する
SELECT
MIN(ingestion_timestamp) AS first_seen,
MAX(ingestion_timestamp) AS last_seen,
meta_hostname,
ARRAY_JOIN(ARRAY_AGG(DISTINCT(meta_hostname)), ', ') AS hosts,
ARRAY_JOIN(ARRAY_AGG(sophos_pid),', ') AS spids,
LOWER(name) AS name,
sha256,
company_name,
file_description,
file_size,
file_version,
original_filename
FROM
xdr_data
WHERE
query_name = 'running_processes_windows_sophos'
AND (
LOWER(name) = '3cxdesktopapp.exe'
OR LOWER(original_filename) = '3cxdesktopapp.exe'
OR LOWER(product_name) ='3cx desktop app')
GROUP by
meta_hostname,
LOWER(name),
sha256,
company_name,
file_description,
file_size,
file_version,
original_filename
ORDER BY
meta_hostname desc
4. ホストが脅威アクターのインフラと通信しているかどうかを判断する (MacOS 向け)
SELECT
meta_hostname,
date_format(from_unixtime(time), '%Y-%m-%d %H:%i:%s') AS date_time,
ingestion_timestamp
pid,
name,
cmdline,
path,
parent,
gid,
uid,
euid,
egid,
sha1,
sha256
FROM
xdr_data
WHERE
query_name = 'running_processes_osx_events'
AND LOWER(cmdline) LIKE '%sh -c%'
AND LOWER(cmdline) LIKE '%/3cx desktop app/updateagent%' また、3CX のソフトウェアのユーザーは、同社のコミュニケーションチャネル (ブログ およびサポートと情報のフォーラム) を引き続き監視することをお勧めします。3月30日現在、同社はアプリのアンインストールと再インストールを推奨しており、状況が改善されるまでの間、同社のブラウザベースの PWA クライアントを使用することも提案しています。
この攻撃に関するIOCの最新リストは、Sophos の GitHub で公開されています。
検出と保護
SophosLabsは、悪意のあるドメインをブロックし、以下の検出結果を公表しています。
スタティック(静的)検出:
- Troj/Loader-AF (Trojanized ffmpeg.dll)
- Troj/Mdrop-JTQ (installers)
- OSX/Mdrop-JTR (installers)
- OSX/Loader-AG (Trojanized ffmpeg.dll)
レピュテーション検出:
- Mal/Generic-R / Mal/Generic-S (d3dcompiler with appended shellcode)
メモリ検出:
- Mem/Loader-AH
また、この脅威に関連する既知の C2 ドメインのリストをブロックし、上述のように、Sophos の GitHub 上の IOC ファイルでそのリストに追加していく予定です。最後に、影響を受けた 3CXapplication にバンドルされている ffmpeg.dll の 2 つの悪意のあるバージョンは、そのハッシュによって低評価であるとのフラグが立っています。
SophosLabs では、このソフトウェアに起因する活動に対する追加の検出機会を積極的に調査しています。さらに、Sophos MDR をご利用のお客様には、MDR Detection Engineering チームが、フォローアップ活動を検出するためのさまざまな動作検出を実施しています。
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)