 So far, Adobe doesn’t seem to have put out any fixes for Update Tuesday [2015-02-11T08:00Z].
So far, Adobe doesn’t seem to have put out any fixes for Update Tuesday [2015-02-11T08:00Z].
Perhaps the company feels it’s ahead of the game this month, having put out three “out-of-band” emergency updates since January’s Update Tuesday?
Anyway, no matter, because Microsoft’s updates have more than made up for it, even if only in the excitement they’ve generated.
Here comes JASBUG
For better or for worse, two of Microsoft’s nine bulletins for February 2015 have stolen the spotlight.
These vulnerabilities are MS15-011 and MS15-014, and they both relate to Microsoft’s Group Policy system.
They’ve acquired a high profile for a number of reasons:
- They both allow Remote Code Execution (RCE) in the most general way possible: by feeding imposter files from a server to a client. (I ask for a trusted program; you send me malware instead.)
- They both involve Group Policies and Group Policy Objects (GPOs), features of Windows Active Directory that are ironically supposed to simplify administration, improve consistency and boost security.
- One of the two bugs has been given a catchy, media-friendly name (JASBUG) and a big PR shove by one of the companies that helped to uncover it.
The elevator summary for this brace of bugs is as follows.
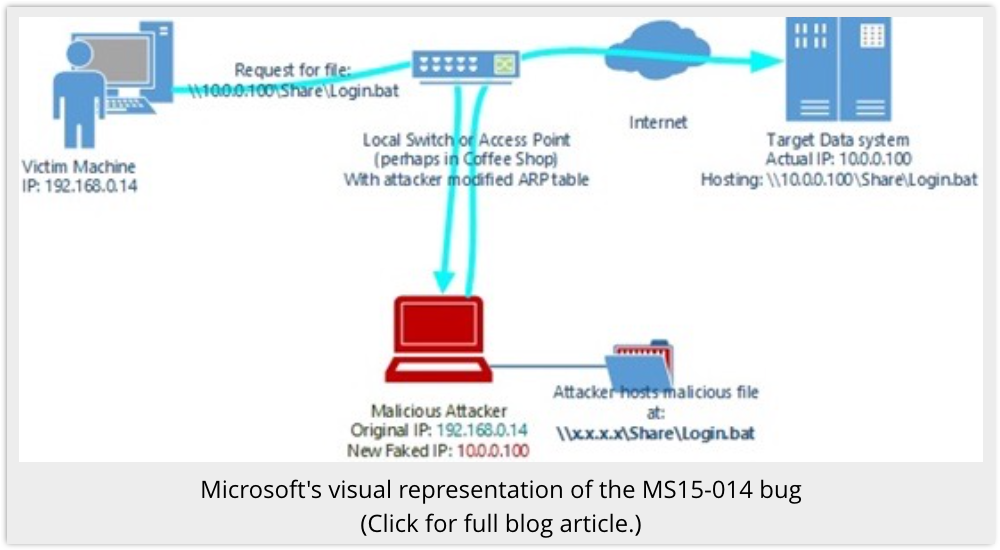
When a computer connects to an Active Directory network, the server carefully authenticates the client before allowing it at any files.
But the client doesn’t necessarily authenticate or verify the server, or can be tricked into not doing so. (Old-school security, remember, was always about protecting the network from dodgy outsiders, rather than the other way around.)
So, in some cases, when you try to fetch files from certain file shares, an attacker may be able to redirect your network traffic to an imposter server.
Your Windows client software won’t notice the switch, so the crook can then feed you imposter files, including malware-laden, booby-trapped programs, scripts or documents.
Don’t forget the rest
The publicity that has surrounded JASBUG – curiously, JAS Global Advisors, one of the companies that helped find it, actually decided to name the flaw after itself – has a downside.
Indeed, JASBUG is a serious hole that puts corporate networks at risk, and, if exploited successfully, makes RCE trivially easy, because the crooks get to feed you fully-formed imposter files.
But be careful that you don’t let JASBUG overshadow the other fixes in the February 2015 Update Tuesday repertoire.
Notably, beware of deferring Microsoft’s other fixes “until the biggie is patched,” not least because just applying the update isn’t quite enough to sort out JASBUG, although a regular update will fix the others.
Unfortunately, there are plenty of others this month.
Three of these give the crooks a chance at RCE exploits on almost any Windows computer, whether it’s logging on to an Active Directory network or not:
- MS15-009 – Security Update for Internet Explorer. This update patches 41 vulnerabilities, including one that is already publicly known. This includes exploitable bugs that can be triggered merely by getting you to look at a booby-trapped web page.
- MS15-010 – Vulnerabilities in Windows Kernel Mode Driver. This update patches 6 vulnerabilities in the kernel. This includes yet more font-rendering problems, so that an innocent-looking font file (embedded, for example, in a document or web page opened by a regular user) could give an attacker the keys to the whole castle by taking over execution right inside the operating system itself.
- MS15-012 – Vulnerability in Microsoft Office. This closes three remotely exploitable holes in Office – and, very importantly, in the Microsoft Word Viewer. A booby-trapped attachment that you merely look at could take over your computer.
Patch the lot!
So, for all that your network administrators at work might be sweating the most right now about JASBUG, don’t take that attitude home with you.
At home, where you probably don’t even use Active Directory or GPOs, JASBUG most likely won’t affect you at all.
But the three bugs listed above in Explorer, Office and the kernel itself could let a crook take over your computer at any time.
And remember that kernel vulnerabilities, where a file opened by a user can compromised the entire operating system, are essentially “trifecta bugs,” combining RCE, Security Bypass and EoP (elevation of privilege) into one Big Bang.
Notably, even the Word Viewer, which many people use as a “risk-reduced” version of Office for looking at untrusted files, could put you at risk of booby-trapped web downloads or email attachments.
The bottom line
You know what we’re going to say.
It may sound trite, but it never gets old: patch early, patch often.
→ For a full list of this month’s fixes, please see the SophosLabs Vulnerabilities page.
Patchwork letters and background of denim cloth courtesy of Shutterstock.

Nomphra
Anyone still running Server 2003 SP2 or Vista SP2 (or XP via the Custom Support Program) should be wary of KB3013455. This has been found to cause font corruption, so you may find your users complaining of “fuzzy text” (or perhaps just headaches).